Information Security Management Handbook, Sixth Edition (2012)
DOMAIN 2: TELECOMMUNICATIONS AND NETWORK SECURITY
Internet, Intranet, Extranet Security
Chapter 2. E-Mail Security
Terence Fernandes
While e-mail still serves the theoretically simple purpose of transmitting information just like regular mail, it does so in a digital form, allowing for more options, customization, convenience, and an overall experience that is more aligned with the demands of our modern world, which is, day after day, relying more on the Internet and its different associated services.
As mentioned earlier, this technology has evolved in many ways and continuously offers new methods of usage; however, it still relies on quite basic protocols. For example, although we can now use a browser to directly manage our mailbox, clicking on the send button is still translated and eventually handled by the server in the same way as if a SMTP (Simple Message Transfer Protocol) transaction was initiated. These complex evolutions, associated with rather modest yet powerful protocols, make securing e-mail transactions a challenge on various levels.
We will first describe how e-mail actually functions and illustrate the different scenarios used nowadays. We will then state the major security threats and vulnerabilities that the e-mail ecosystem faces. Finally, we will develop various solutions to make the use of e-mail more secure and see that trying to fix issues related to e-mail security is not always a matter of technical solution, but sometimes involves management decisions and the strict enforcement of policies.
How Does E-Mail Actually Work?
When trying to understand the exchange of digital information that occurs while using e-mail, it is first interesting to know that different scenarios can result in the transmission of data. For example, it is possible to send and receive e-mails between two user agents on the same machine, or to exchange messages between two users through one single internal network. But the most common scenario can be described by identifying a user agent residing in network A, which sends a message to another user agent residing in network B. In this section, we will focus on this last scenario because it will give us an overview of the e-mail architecture and exchange process. The general idea can easily be extrapolated to the other scenarios as well.
Let us imagine a situation where Alice wants to send a message to Bob, each residing in different networks. Alice has several solutions to help her write the message. The most common one would be for Alice to use some software that would act as an e-mail client, to write and then send her message. When Alice is ready to send the message, the e-mail client transfers the message to a Mail transfer agent (MTA). We can see that the e-mail software in this case, or a Webmail in other examples, is really just an interface between the user and the MTA client.
Usually, it will send the message across the network using an application-level “transfer” protocol, called Simple Message Transfer Protocol (SMTP), defined in RFC 821 (Internet Engineering Task Force, 1982). The role of the MTA client is to transfer the message to the MTA server through the network that Alice is connected to. This MTA server can be either on the same network or on a different one, in which case, Alice will need to use its Internet access to reach the server.
The MTA server acts as a back-to-back agent, with a server running and receiving the message sent by Alice’s MTA client, and as an agent preparing to send this message across the Internet to another MTA server linked to Bob’s network. This recipient server is also a back-to-back user agent, with the first one being the agent receiving Alice’s message from the first MTA server, and the second agent being a mail access agent, allowing Bob’s client to retrieve the message and display it in the e-mail software that he commonly uses. This retrieval operation involves another set of application-layer protocols, often described as “access” protocols (Comer, 2009), with the most common ones being Post Office Protocol (POP), defined in RFC 1939 (Internet Engineering Task Force, 1996), and Internet Message Access Protocol (IMAP), defined in RFC 3501 (Internet Engineering Task Force, 2003). Figure 2.1 gives a visual representation of the flow just described.
Many other e-mail architectures exist, particularly in a corporate environment (e.g., Microsoft Exchange is one of the most popular), but these will not be described in this chapter. However, the potential vulnerabilities and important security principles described in the following sections can be applied to any of those architectures. It is important to identify and understand the flaws that such a system can have, to better understand the risks and find appropriate solutions to secure the use of e-mail. We will describe these in the following section.
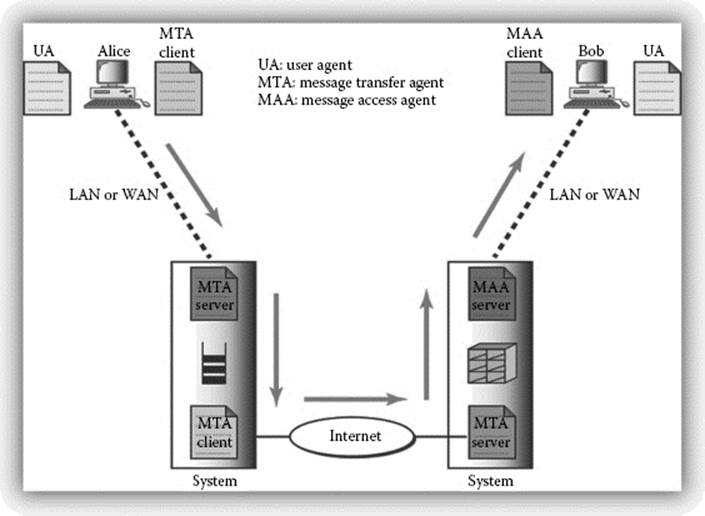
Figure 2.1 Traditional e-mail flow. (K. Vaccaro, Email.ppt, 2011 © All Rights Reserved.)
E-Mail System at Risk
Recognizing e-mail vulnerabilities is a serious challenge as various security issues, on different layers, can target and compromise the security of the e-mail system. Indeed, we will see vulnerabilities, from the protocols used to transmit or retrieve the message that are, by default, insecure, to a corporate e-mail policy that might be too lenient. The vulnerabilities are diverse and need to be carefully reviewed to provide an architecture that is globally safe, or at least, minimizes a reasonable number of risks.
Even if, at first, e-mail was designed to only carry text in its body, with the evolution of personal computing, the increase of the bandwidth capacity available, and the extensive use among businesses, e-mail users naturally began to exchange more than just plaintext and attached documents, photographs, small videos, and even executable programs to their digital exchanges. E-mail has become a very simple and efficient way to share content between users, with the classic example of a mother e-mailing the photographs of her newborn baby to her family. We can also think of a company sending with ease and in a very short amount of time, a business proposal by e-mail to its future client. These legitimate uses of the e-mail attachment function justify the usefulness of this service in both a corporate and a personal environment and explain why we, as users, choose to rely more on e-mail for our communication needs and see it as an essential component of the new computing era.
However, ill-intended people quickly understood that such a solution would be an easy yet powerful vector of attack to rapidly spread malicious codes or software to numerous users (Bradley, 2006, chap. 6). Such malicious codes or software are often designated as “virus” or “malwares” and are intended to harm either the installed programs or the hardware components of the infected machine, steal information from it, or use the machine as a relay to send more information across the network.
On 26 March 1999, “Melissa” became the first widespread virus that used e-mail to propagate onto more than a million computers across the globe (F-Secure). The virus spread at an unprecedented rate, infiltrating thousands of networks in a matter of hours and forcing big corporations like Microsoft and Intel to shut down their e-mail servers to protect their assets. One of the reasons that can explain this fast-paced infiltration was the behavior of this virus regarding its propagation. Indeed, once the virus infected a machine, it would send itself to the first 50 entries in the address book, using one of the e-mail accounts available on the computer, all of this of course, without the user’s knowledge. The virus was embedded in a Word document, which supposedly contained passwords that would give you full access to pornographic Web sites. It made use of the “macro” functions to execute its malicious code, to lower the security features of Microsoft Word, it modified keys in the Windows registry, and compromised the template used by Word for every new document (normal.dot), infecting every single new document by default (CERT—Carnegie Mellon Software Engineering Institute, 1999). Other variants of the virus were even more destructive, targeting Windows system files, for example.
“Melissa” is just one of the iconic examples of the many viruses that have either used or still capitalize on e-mail as a vector of propagation. They constantly innovate their way of operating; e.g., they mask the true extension of the attached file, thereby hoping to exploit an operating system flaw, because, by default, Windows hides known file extensions. Using this method, an apparently innocent .txt text file can instead reveal a .exe executable program. Viruses also heavily rely on a concept called “social engineering,” which, in this case, could be described as a science that has been developed to find ways to fool or trick the targeted user into trusting the malicious e-mail. We will see that this concept is used by several other types of threats and develop it further on.
Even though the trend currently shows that e-mail virus-based intrusions are declining (Kaspersky, 2010), they still represent a serious menace that can threaten and damage various company’s assets in terms of data (e.g., expose confidential information) or affect the network and, consequently, business operations (e.g., e-mail servers down), while costing billions of dollars in maintenance, prevention, and recovery every year.
Another serious threat related to the exchange of digital information using e-mail is called “spam” or “junk e-mail.” Most e-mail users are now familiar with the spam concept, which is defined as abundant amounts of unwanted e-mails sent to an extensive list of addresses. This concept, which is basically a marketing one, relies heavily on the idea that revenues can be obtained by sending very large amounts of advertisement and then capitalizing on the percentage of responses. In order to be successful in your campaign, you need to generate more revenues from the positive responses compared with your up-front cost of sending the advertisement material. However, it is interesting to remind ourselves of the comparison with regular junk mail because in this case, it is costly for the sender (he has to pay the shipping cost for every single piece of mail), whereas with e-mail, the cost of sending a message to 1 or 1000 recipients is the same for the sender. Indeed, the sender’s Internet Service Provider (ISP) and possibly their e-mail provider, if different, will transfer the message at their own cost (Barile, 2006, 202–12). We therefore understand better how spam can be profitable, considering that the up-front cost is negligible, but the amount of potential customers reached is enormous. Revenues are generated as soon as the first victim clicks on a link—legitimate or not—to buy a product or service advertised in the e-mail, with the potential of many more unsuspicious users contributing to potentially large sums of money.
Interestingly, several studies describe global e-mail traffic to be mainly spam, with numbers reaching as high as 85 percent of the traffic in June 2010 (Kaspersky, 2010). Given the fact that e-mail traffic was estimated to be around 117 trillion messages in 2010 (Pingdom Statistics, 2011), we can easily see why spam represents a challenge for network administrators all around the world, as it wastes an incredible amount of resources and bandwidth. Plus, spam requires the use of a lot of those network and human resources to try to avoid further serious damages to companies and ISPs’ network infrastructure. For example, in certain cases, spam is used to perpetrate DoS attacks against e-mail servers (Paul, 2007) or against a specific mailbox (the concept of “mail bomb”), as the amount of traffic generated by spam messages that are being sent to a specific location, can, if not filtered properly, easily saturate the destination server and make the use of e-mail impossible for other users.
To be able to send such an amount of e-mail through several networks around the world, hackers use botnets, which are small programs similar to viruses that are installed covertly on an infected machine, and use the machine’s resources to send a spam message across the network(s) that it is connected to. These infected machines are often called “zombies” to amusingly refer to their passive state in the transmission of unwanted e-mail messages.
However, apart from the network challenges that spam poses, it also acts as a powerful vector for other types of attacks, including the one we have already discussed, namely, malicious attachments. According to Kaspersky’s 2010 Security Bulletin, between 2.2 percent and 6.29 percent of spam traffic in 2010 contained malicious attachment(s) and given the description of spam that we have just illustrated, we can easily see why such a powerful solution that could virtually reach an extensive number of users, using illegitimate ways of transmission, would be an ideal carrier of malicious software.
One of the largest security threats related to e-mail, and often conveyed using spam, is the content of the message itself. Indeed, even though e-mail was designed to only permit the exchange of text, a translation protocol called MIME, defined in RFC 2045 (Internet Engineering Task Force, 1996), allows the implementation of rich-format content like, e.g., formatted text or HTML code in the message itself. It is then quite simple to implement a malicious JavaScript in the HTML code and retrieve information from the victim without his/her knowledge. On 23 September 2010, Dave Michmerhuizen, a security researcher from Barracuda Labs, reported the following:
Barracuda Labs has seen an enormous increase—in fact, well over one million instances a day—of spam containing malicious HTML […]. After all, what harm can an HTML file do?
The answer is—plenty … (Michmerhuizen, 2010)
The HTML code contained in the message is usually displayed by default by most e-mail clients. The users are then, if not already just by viewing the message, usually one click away from being infected. Indeed, if they choose to open one of the links, they could be redirected to a malicious Web page that would try to upload a malicious payload onto the victim’s machine. Also, the HTML code can be embedded in a file, usually with an .html or .htm extension, and can be attached to the e-mail as a malicious attachment that would infect the targeted computer upon opening.
The previous security issues related to the e-mail architecture exposed the technical use of the vulnerabilities of the system and the malicious use of the e-mail service. But, to have a global picture of the security of e-mail communication, it is also interesting to explore a vulnerability that, although not obvious at first sight, is one of the most dangerous: the user itself.
Indeed, the best security solutions will neither prevent nor protect against an incident like a user giving away his password or using the one that is very easy to guess. Similarly, the powerful security measures implemented on a company’s network are useless if a careless employee were to use a company’s laptop to send e-mail over an unencrypted network at a coffee shop, for example. The failure to use basic computer security principles by some of the employees of a company can be disastrous in terms of the loss of assets and image and requires resources like people, time, and money to fix the problems caused. Also, users can respect those principles directly related to e-mail, but at the same time, fail to protect data or could be compromised while using other services. Shawn Davis, at the NetSecure conference held in February 2011 at the Illinois Institute of Technology, explained how easy it is to retrieve the Facebook password of a user that displays too much information on his/her public profile and therefore facilitate the guess of the password retrieval’s security questions (Davis, 2011). To worsen the problem, most users use the same credentials, or an easy-to-guess combination of the same password, for many services. A study by CPP UK shows that
46 percent of British internet users, 15.6 million, have the same password for most web-based accounts and five per cent, or 1.7 million, use the same password for every single website.
Some 29 per cent use variations of the same password, for example using days of the week or adding numbers to the end of a word.
Memorable dates, children’s names and mother’s maiden names are each used by one in 10. One in five users sign in with their pet’s name. (The Telegraph, 2010)
Therefore, we can understand how the same password used for several Internet-based services can represent a serious, difficult to protect from, yet often overlooked threat for both personal and business e-mail accounts. This example also emphasizes the point that vulnerabilities related to e-mail can be found by exploring threats other than those directly related to the service itself and that global security measures are necessary to protect the e-mail.
The recent trend in terms of security threats, also capitalizing on the social engineering aspects and using e-mail as a vector, is called “phishing.” Phishing e-mails are designed to match the design and layout of specific Web sites to try to deceive and trick the users into providing some of their personal information, like their name, their e-mail address, their telephone number, or more importantly, their social security number or their bank account numbers and passwords for online access. These attacks have been increasing in the past few years—one in every 250 e-mails sent in March 2011 was a phishing attack (Symantec Corp., 2011)—although their complexity and the design of the malicious e-mail have greatly improved. It has actually reached the point where the received phishing e-mails are very close, if not almost identical, to a legitimate e-mail sent by one of the targeted companies, making the distinction between a valid and a fraudulent e-mail quite difficult for a regular user. Phishing attempts usually target financial companies like PayPal (PayPal Inc.), and national banks like Chase (JP Morgan Chase Bank Inc., 2011) or Bank of America (Bank of America Inc.), but a fair amount of these phishing attacks also target e-mail service providers, such as Hotmail (Microsoft Corp.) and Gmail (Google Inc., 2011). Other types of scams, like the famous “Nigerian Prince” (Barile, 2006, 218–19), use false stories and promise financial gain in exchange for personal information.
Once again, the preferred vector for these attacks is e-mail, and spam plays an important role in these phishing threats, by facilitating the sending of a large amount of forged e-mails, at a low cost, with potentially important gains even with a very low response rate. A typical attack would consist of a HTML formatted e-mail, with a layout similar to a targeted company’s Web site or newsletter, stating a false reason (like a security breach, a locked account, or a routine maintenance) to ask the user to provide his/her personal information by clicking on one of the embedded links that would take the user to a forged Web site. Other variants of attacks, especially used with scams such as the one described earlier, consist of a plaintext story, with personal information requested in a reply.
Technology is evolving very rapidly and while new services are emerging, new ways to use the existing ones, including e-mail, are developing as well. Indeed, although we have described a typical e-mail exchange using software acting as e-mail clients on physical machines in the first section of this chapter, a new concept called “webmail” has quickly grown in popularity; in 2008, it reached more than 650 million users (Email Marketing Report, 2008), while more than “94 percent of US Internet users have gone online to send or read e-mail” as of May 2010 (Pew Internet, 2010). Webmail allows users to send and receive e-mail through a Web interface accessible via a Web browser, while also offering them several options to manage their e-mail mailbox (e.g., folder arrangement, labels, and specific rules). While this Web interface has many advantages, including the convenient option of managing an e-mail mailbox from virtually any computer connected to the Internet, it is important to note that the e-mail architecture behind this interface stays the same, and clicking on the send button on the Web page is simply translated into a SEND command on one of the mail servers that handles the exchange of the specific account. Moreover, this new way of using the e-mail service brings new security challenges to the surface, especially those related to the use of the Web browser. For example, we have seen earlier in the chapter that e-mail providers are commonly targeted by phishing attacks. Additionally, a forensics analysis of the machine used to access the Webmail account can reveal private information, e.g., the e-mail address, the type of account, and whether or not the connection to the Web site is secure. These pieces of information are stored in the cache file of the browser, the registry, or other locations in the computer and can easily be retrieved (Lidinsky and Vaccaro, 2011). In addition to these issues, using a Webmail service, a company employee can bypass certain network restrictions enforced by the company’s policies (e.g., adding a personal account on his/her e-mail client located in his/her professional computer). Indeed, with a Webmail provider, the user can easily log on to his/her personal e-mail account, and, if not filtered properly, the traffic generated would be no different from regular Web traffic on port 80. All of the above-mentioned security issues would then threaten the company network and assets, if, e.g., the user downloaded an infected attachment or browsed a fraudulent Web site instead of its legitimate e-mail provider Web site.
Last but not the least, one of the major security threats is the dependence of e-mail on several intermediary clients, servers, and protocols that can themselves have vulnerabilities, which eventually threaten the integrity of an e-mail communication. For example, most Windows users choose Microsoft Outlook© as their primary e-mail client for managing their e-mail mailbox. Unfortunately, this software, along with many others, often needs to be patched to fix newly discovered security vulnerabilities, such as up-to-date viruses or HTML formatted messages, which could be exploited by hackers to compromise the user’s stored data. Some of these updates are not automatically applied, and the user ultimately decides to download and install them at his or her will. It can thus create a problem, when users wait for a long time, or even skip security updates, allowing malicious people and software to take advantage of those vulnerabilities for a certain period of time. Additionally, Web browsers and mail servers are also impacted by these security updates, ultimately putting the architecture at risk if the updates are not properly applied in a timely fashion.
Additionally, the usual mail protocols, namely, POP, IMAP, and SMT, often by default, use their nonsecure version to handle the exchange of e-mail messages (through common ports 25, 110, and 143), making the interception of traffic (e.g., using a sniffer like WireShark or other specialized software) potentially dangerous. The Hypertext Transfer Protocol (HTTP) traffic generated using Webmail services (through common port 80) can also be compromised if the secure version of the HTTP is not used. Also, some flaws in the format of the headers can lead to unexpected events, including failure of the mail server that handled those purposely badly formatted messages.
Finally, some common Internet attacks, although not specifically designed to target the e-mail system and architecture, can be used for that purpose. Man-in-the-middle attacks can compromise the certificates used to protect the transmission of e-mail messages, while DoS attacks targeting e-mail servers can cause problems in the sending and delivery of e-mail messages, to cite a few examples.
In the previous paragraphs, we explored some of the serious issues, vulnerabilities, and threats that can affect the e-mail architecture, either by disrupting its ability to handle messages, by transporting malicious content that could potentially be dangerous to both the servers and the end-user machine, or by letting unauthorized people exploit flaws that allow them to access and retrieve private data. From the examples we have shown, it therefore seems that the e-mail service, as well as the architecture it relies on, is very insecure, leading us to ask ourselves why these serious problems do not affect the popularity of e-mail across the world. In the next section, we will see that many measures, some easier to implement than others, contribute in making the e-mail system more secure and usable for both personal and professional correspondence.
Securing the E-Mail Architecture
One of the biggest security threats that we discussed in the previous section is related to malicious software, including viruses, malware, and spyware, which are attached to e-mail and rely on an unsuspecting user to open the attachment to infect the targeted machine. Fortunately, several solutions exist in protect the user against these threats. Indeed, as malicious software is not new to the computing world (it is worth remembering that the Melissa virus that we previously described is more than 10 years old), security companies, network administrators, and software developers have had time to work on ways to protect the end users from such threats. The most common layer of protection on Windows machines is antivirus software, either installed as a stand-alone program, or contained in a global security suite that would also include a firewall and protection against malwares along with a spam filter. Several renowned security vendors such as Symantec Corp. and McAfee Inc., offer these suites, including professional editions with enhanced security in a corporate environment. These software rely on updates of their virus definitions—either being downloaded automatically at regular intervals, or pushed directly to the user’s machine when serious threats are discovered—to protect the users and their data against malicious codes. The major downside of these solutions is that such suites are often seen as retroactive security measures, because initially they are dependent on the discovery of the malicious code and methods to render it ineffective, and subsequently, on the update being successfully and quickly delivered to a large pool of computers. Most antivirus software also use “heuristic” engines, which detect suspicious processes running on the operating system without relying on virus definitions; however, this method does not guarantee a perfect detection rate and often returns annoying false-positives. Almost all of the security suites will offer plug-ins for common e-mail clients, allowing automatic scanning of attachments. Additionally, the mail server itself can perform these security measures, and many ISPs offer such protection as automatic scanning of attachments, with Comcast Inc. and their SmartZone service being one of many other examples. Webmail providers like Hotmail also offer similar services.
Finally, the suites along with the measures taken by the ISPs and the Webmail providers help reduce the amount of spam received in the actual mailbox to a manageable level. Because of improved scanning and detection technologies—that use keywords, common patterns, definitions tables, and user’s input (Barile, 2006, 207–14)— it is possible to recognize as much as 95 percent of spam messages, tag them, and either put them in a specialized folder or delete them before they arrive in the user’s mailbox.
Resolving the phishing issue is, however, more complex, and even though a thin layer of protection against this specific threat is provided by the suites previously described, additional measures embedded either in the Internet browser or the network architecture, and more specifically the Domain Name System (DNS), are preferable for a more powerful defense. Indeed, we have seen that most phishing attempts included in e-mail messages will invite the user to visit a fraudulent Web site after clicking on a link on the message, thereby leaving the environment of the e-mail client, or the Webmail page. Updated versions of the most popular Internet browsers, including Microsoft Internet Explorer (versions 8 and 9), Mozilla Firefox, and Google Chrome, all include a phishing filter, based on a remote database, which warns an unsuspicious user when he or she browses a reported fraudulent Web site. Similarly, the DNS, which plays an important role in Internet browsing, has evolved to provide more protection for its users against phishing attacks. Explaining the functioning of the DNS is out of the scope of this chapter, but OpenDNS (OpenDNS Inc.) and Google DNS, e.g., provide their users with phishing protection, even with their free solutions. They also offer professional solutions, with enhanced features, tighter security measures, and better support. Nevertheless, regardless if the environment is a company or a personal network, we can see that these different solutions, all capable of working together, can provide acceptable protection against phishing links received in an e-mail that a user could accidently click on.
We have also developed issues related to the lack of proper training of some users. Fortunately, many options can remedy such problems. For personal users, several books and Internet documentation are available and can offer important information in terms of best security practices when using a computer and Internet-based services like e-mail or browsing. Public libraries in major cities, including, e.g., the Chicago Public Library, also offer training classes and workshops, giving users tips and advice to make their use of computers more secure and more prudent while using e-mail.
Companies are also encouraged to invest in professional training for their employees, to give them a basic knowledge of security measures that can prevent damaging events to the company. Private organizations and colleges, like the Illinois Institute of Technology, often offer such programs destined for professionals seeking to keep up to date with technology-related issues. Also, the policies of a company need to be carefully designed, reviewed, and enforced to provide an additional, but essential layer of protection. Writing a specific policy regarding the use of corporate e-mail with detailed instructions on how to avoid potential risks, and requiring all employees to read and acknowledge it, will strengthen the company’s security posture, in addition to providing grounds for potential legal action in case of a security breach caused by a careless employee. An example of the measures detailed in such policies and enforced by the administrators would be the disabling of the HTML content of e-mails received on corporate e-mail addresses to prevent vulnerabilities related to embedded malicious HTML code.
Secure versions of the security protocols should also be used by default, according to the specifications detailed in the respective request for comments (RFCs). The Secure Socket Layer (SSL), which is a secure protocol commonly used to provide integrity protection of the transmitted data, can be used conjointly with the POP and the SMTP protocols, e.g., (the port used will change from 110 to 995 for POP and from 25 to 465 for SMTP). Similarly, while accessing the Webmail service using the regular version of HTTP can lead to the interception of the user’s information across the network, using the secure version of the protocol, HTTPS, will make those common spoofing attacks much more difficult and provide the user with authentication protection between his or her machine and the distant server.
Conclusion
E-mail security has never been a more current subject than today. Indeed, while the usage of the basic e-mail service has evolved through time with the demands of its users and the innovative progress in technology, the vulnerabilities and threats are also growing more complex and involve new concepts like social engineering, which we have described in this chapter. At the same time, our world is increasingly interconnected via the Internet and increasingly dependent on its various services, either for business or personal purposes, while the amount of data stored and transmitted via e-mail rises constantly. This information, whether private or confidential, personal or business-related, interests malicious people who seek opportunities to make profits and quick financial gains by exploiting e-mail’s technical flaws and by fooling people who are careless or simply uninformed. A very recent example would be the Epsilon security breach that occurred on 4 April 2011, exposing millions of users’ e-mail addresses, along with partial private personal information from banks, stores, hospitals, customers, and patients. As this attack is seen as one of the biggest security breaches that has occurred in recent times, and yet, is probably not the last, it is important to carefully review and prudently implement various security measures on different layers to protect the e-mail service. In this chapter, we explored some of the methods and explained that the correct use of technical security solutions, along with the strict enforcement of procedures and appropriate training given to users, could effectively reduce the risks related to the use of e-mail to a minimum.
E-mail security can be defined as an interesting combination of processes and products, which requires a very careful analysis, combined with accurate risk assessments and the meticulous design of adequate solutions. It has been, and will continue to be, a very tough challenge to take on. But, at the same time, with users reaching more than a billion, it becomes even more clear and urgent that security is a priority that no personal user or business can afford to overlook in the future.
References
Bank of America Inc. Phony emails and fraudulent websites. http://corp.bankofamerica.com/public/public.portal?_pd_page_label=landing/directsecurity/fraud (accessed April 20, 2011).
Barile, I. Protecting Your PC, First Edition. Charles River Media, Boston, MA, 2006.
Bradley, T. Essential Computer Security: Everyone’s Guide to E-Mail, Internet and Wireless Security. Syngress, Rockland, MA, 2006.
CERT – Carnegie Mellon Software Engineering Institute. March 27, 1999. CERT® Advisory CA-1999-04 Melissa Macro Virus. http://www.cert.org/advisories/CA-1999-04.html (accessed March 19, 2011).
Comer, D. E. Computer Networks and Internets, Fifth Edition, vol. 1. Pearson, Upper Saddle River, NJ, 2009.
Davis, S. Effective Training and Policy Takes Fear out of Social Networking. Illinois Institute of Technology, Wheaton, IL, 2011.
Email Marketing Report. April 2008. Email and webmail user statistics. http://www.email-marketing-reports.com/metrics/email-statistics.htm (accessed April 14, 2011).
F-Secure. Threat description: Virus:W32/Melissa. http://www.f-secure.com/v-descs/melissa.shtml (accessed February 21, 2011).
Google Inc. Messages asking for personal information, March 20, 2011. http://mail.google.com/support/bin/answer.py?answer=8253 (accessed April 19, 2011).
Internet Engineering Task Force. RFC 821, August 1982. http://www.ietf.org/rfc/rfc0821.txt (accessed March 2011).
Internet Engineering Task Force. RFC 1939, May 1996. http://www.ietf.org/rfc/rfc1939.txt (accessed February 2011).
Internet Engineering Task Force. RFC 2045, November 1996. http://www.ietf.org/rfc/rfc2045.txt (accessed March 28, 2011).
Internet Engineering Task Force. RFC 3501, March 2003. http://www.ietf.org/rfc/rfc3501.txt (accessed March 2011).
JP Morgan Chase Bank Inc. Fraudulent e-mail examples, January 11, 2011. https://www.chase.com/index.jsp?pg_name=ccpmapp/privacy_security/fraud/page/fraud_examples (accessed April 20, 2011).
Kaspersky. Security bulletin 2010, December 2010. http://www.securelist.com/en/analysis/204792163/Kaspersky_Security_Bulletin_Spam_Evolution_2010 (accessed January 29, 2011).
Lidinsky, W. and Vaccaro, K. Web forensics. Institute of Technology, Wheaton, IL, 2011.
Michmerhuizen, D. HTML is not harmless—Email security update, September 23, 2010. http://www.barracudalabs.com/wordpress/index.php/2010/09/23/html-is-not-harmless-email-security-update/ (accessed April 2, 2011).
Microsoft Corp. Microsoft safety and security center. http://www.microsoft.com/security/online-privacy/phishing-faq.aspx (accessed April 19, 2011).
Paul, R. Spammers launch denial of service attacks against antispam sites, 2007. http://arstechnica.com/security/news/2007/09/spammers-launch-denial-of-service-attacks-against-antispam-sites.ars (accessed April 2, 2011).
PayPal Inc. Report fraudulent activity. https://cms.paypal.com/us/cgi-bin/?cmd=_render-content&content_ID=security/report_problem (accessed April 20, 2011).
Pew Internet. Trend data—Online activity, May 2010. http://www.pewinternet.org/Static-Pages/Trend-Data/Online-Activites-Total.aspx (accessed April 14, 2011).
Pingdom Statistics. Internet 2010 in numbers, January 11, 2011. http://royal.pingdom.com/2011/01/12/internet-2010-in-numbers/ (accessed March 6, 2011).
Symantec Inc. MessageLabs Intelligence: March 2011, March 2011. http://www.messagelabs.com/mlireport/MLI_2011_03_March_Final-EN.pdf (accessed April 13, 2011).
The Telegraph. Almost 16 million use same password for every website, study finds. The Telegraph (UK), 2010. http://www.telegraph.co.uk/technology/news/6922207/ (accessed January 2010).