Introduction To Network Security: Theory And Practice (2015)
Chapter 1. Network Security Overview
1.4 Basic Security Model
The basic security model consists of four components: cryptosystems, firewalls, anti-malicious-software software (AMS software), and intrusion detection systems (IDS system). Figure 1.10 shows this security model.
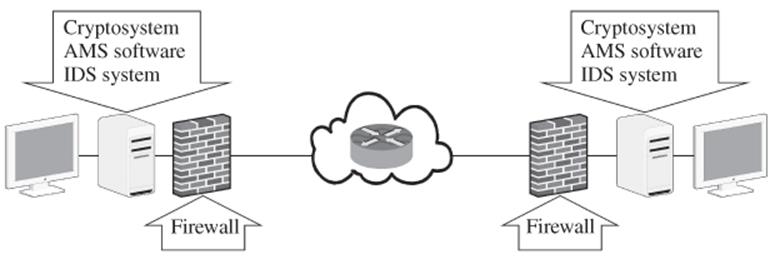
Figure 1.10 Basic security model
Cryptosystems use computer cryptography and security protocols to protect data. Security protocols include encryption protocols, authentication protocols, and key management protocols. Figure 1.11 shows the encryption and decryption components. It is customary to use ![]() to denote an encryption algorithm,
to denote an encryption algorithm, ![]() its decryption algorithm, and
its decryption algorithm, and ![]() the secret key.
the secret key.
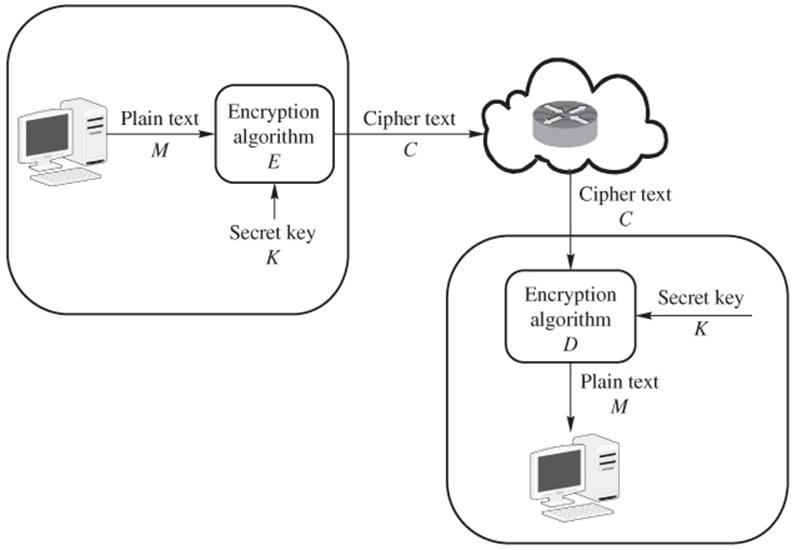
Figure 1.11 Network model of cryptosystem
Firewalls, AMS software, and IDS systems are used to protect data stored in networked computers. Firewalls are special software packages installed in computers and networking devices that check incoming and outgoing network packets. Certain features of firewalls have also been incorporated into hardware devices to achieve faster processing speeds. AMS software scans system directories, files, and registries to identify, quarantine, or delete malicious code. IDS systems monitor system logins, study user behaviors, and analyze log files to identify and sound alarms when intrusions are detected.
In addition to using firewalls, AMS software, and IDS systems, we may also set up sacrificial decoy machines to lure attackers' attentions away from important computers. Decoy machines are also known as honeypots.
This book is centered around these four major components. This book also introduces honeypot technologies.