Nmap 6 Cookbook: The Fat Free Guide to Network Security Scanning (2015)
Introduction
Nmap is a network scanning utility created by Gordon “Fyodor” Lyon that can be used to discover, audit, and troubleshoot networked systems. It is free software released under the GNU General Public License (see gnu.org/copyleft/gpl.html). Nmap is is actively developed by a community of volunteers and is an evaluable tool for network administrators and security auditors.
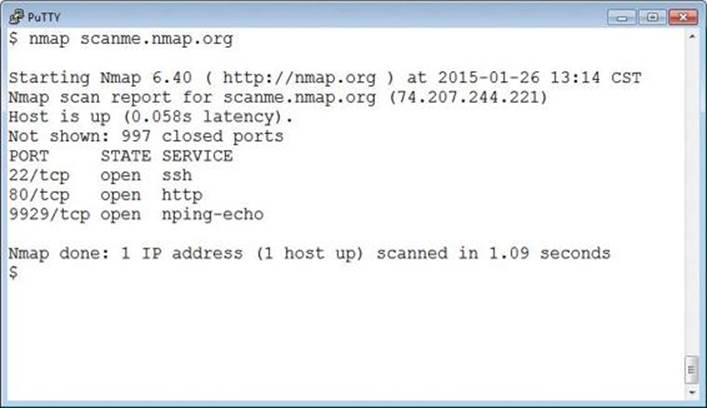
A typical Nmap scan
Nmap’s award-winning suite of network scanning utilities have been in constant development since 1997 and continually improve with each new release. Version 6 of Nmap (released in May of 2012) adds many new features and enhancements. Some of the best new features added to Nmap 6 are listed below:
- Improved service and operating system version detection
- Better support for Windows and Mac OS X
- Addition of the Nping utility (discussed in Section 14)
- Continued enhancement of NSE (the Nmap Scripting Engine, discussed in Section 15)
- Full support for IPv6
- Better overall performance
The Nmap project relies on volunteers to support and develop this amazing tool. If you would like to help improve Nmap, there are several ways to get involved:
Promote Nmap
Nmap isn't just a tool made exclusively for "hackers". It's a wonderful program that every network administrator should know about. Despite its fame (Nmap has been featured in several movies), it isn’t widely known outside of technically elite circles. You can help promote Nmap by introducing this wonderful tool to your friends or writing a blog entry about it.
Note: Show your friends how cool Nmap is by pointing them to Nmap's movie credit page at nmap.org/movies.
Report Bugs
You can help improve Nmap by reporting any bugs you discover to the Nmap developers. The Nmap project provides a mailing list for this, which can be found online at seclists.org/nmap-dev.
Note: Thousands of people worldwide use Nmap. Additionally, Nmap developers are very busy people. Before reporting a bug or asking for assistance, you should search the Nmap website and mailing lists to make sure your problem hasn’t already been reported or resolved.
Contribute Code
If you’re a programmer with some spare time on your hands, you can get involved with Nmap development. To learn more about contributing code to the Nmap project visit nmap.org/data/HACKING. Nmap also sponsors Google Summer of Code. If you're a student you can apply to join this annual program at nmap.org/soc and gain valuable experience while also helping to improve the Nmap suite.
Submit TCP/IP Fingerprints
If you’re not a programmer, you can still improve Nmap by submitting any unknown TCP/IP fingerprints you discover while scanning. Submitting fingerprints is easy and it helps improve Nmap’s software version and operating system detection capabilities. Visitnmap.org/submit/ for more information or to submit your discoveries.
Note: More information on this topic is covered in Section 6.
Sponsor Nmap
The Nmap project does not accept donations. If, however, you have a security related service you would like promote, you can sponsor Nmap by purchasing an advertising package on the insecure.org website. For more information, visit insecure.org/advertising.html.
Conventions Used In This Book
Nmap running on Microsoft Windows systems:
C:\> nmap scanme.nmap.org
Nmap running on non-privileged accounts for Unix/Linux/Mac OS X:
$ nmap scanme.nmap.org
Nmap running on Unix/Linux/Mac OS X systems as the root user:
# nmap scanme.nmap.org
Using the sudo command to elevate privileges for Unix/Linux/Mac OS X:
$ sudo nmap scanme.nmap.org
Note: Windows users may omit the sudo command where used in examples as its use is not necessary and will not work on Microsoft based systems.
Using command line options with Nmap:
# nmap -T2 scanme.nmap.org
Important: Nmap’s command line options are case sensitive. The -T2 option (discussed in Section 7) in the example above is not the same as -t2 and will result in an error if specified in the incorrect case.
Additional Nmap output truncated (to save space):
[...]
Keyboard sequences:
<ENTER>, <CTRL + C>, etc.