Hacking Wireless Networks (2015)
Part III
Advanced Wi-Fi
Hacks
Chapter 15
Authenticating Users
In This Chapter
ᮣ Understanding authentication
ᮣ Looking at authentication problems
ᮣ Understanding EAP
ᮣ Cracking LEAP
ᮣ Protecting your network
In this chapter, we provide an overview of the user-authentication mechanisms to better illustrate their existing limitations. By authentication, we mean that one entity has to prove its identity to the other before a secure transaction can take place. Because 802.11-based wireless LANs are relatively new technologies, you may find the available authentication features are not as comprehensive or robust as you would like. We’d agree. Fortunately, each new standard improves upon existing standards. But it’s an ongoing battle; we can always find tools to exploit weaknesses described in this chapter.
Those flaws arise partly because the vendors frequently disable built-in security features as default settings — and partly because people either fail to change the defaults, or don’t use built-in security features as part of their overall defense in-depth strategy.
Three States of Authentication
A basic, indispensable security service is authentication. In the standard 802.11, we don’t authenticate users, but we authenticate machines. Under some common (but vulnerable) security setups, if you want people to authenticate their machines to a particular access point, then you make sure they know the shared key. (Bad idea.) This chapter shows you why you don’t want to use the shared key to authenticate.
22_597302_ch15.qxd 8/4/05 7:11 PM Page 282
282 Part III: Advanced Wi-Fi Hacks
First off, it’s worth looking at the three states a wireless client goes through in the authentication process:
ߜ Unauthenticated and unassociated: The client selects a basic service set by sending a probe request to an access point with a matching SSID.
ߜ Authenticated and unassociated: The client and the access point perform authentication by exchanging several management frames. Once authenticated, the client moves into this state.
ߜ Authenticated and associated: Client must send an association request frame, and the access point must respond with an association response frame.
A client can authenticate to many access points, but will associate only with the access point with the strongest signal.
In the second state, we just casually mention the client authenticates to the access point. It’s not quite that simple.
Authentication according to IEEE 802.11
The IEEE 802.11a and b specifications define two ways to “validate” wireless users who are attempting to gain access to a wired network. One does the job; the other one doesn’t:
Open-system authentication: convenient but dangerous
This “authentication” technique isn’t really authentication because the access point accepts the mobile station willy-nilly without verifying its identity. The access point authenticates a client when the client simply responds with a MAC address during the two-message exchange, in a simple (and insecure) process:
1. Client makes a request to associate to an access point.
2. The AP authenticates client and sends a positive response — voilà! The client is associated.
Shared-key authentication
Shared-key is a cryptographic — that is, real — technique for authentication.
It is a simple “challenge-response” scheme based on whether a client has knowledge of a shared secret. In this scheme, the access point generates a random 128-bit challenge that it sends to the wireless client. The client, using a cryptographic key that is shared with the access point, encrypts 22_597302_ch15.qxd 8/4/05 7:11 PM Page 283
Chapter 15: Authenticating Users
283
the challenge or nonce (as it is called in security vernacular) and returns the result to the access point. Then, the access point decrypts the result that the client computed and sent, and allows access only when the decrypted value is the same as the random challenge transmitted. The algorithm used in the cryptographic computation and for the generation of the 128-bit challenge text is the same RC4 stream cipher used for encryption.
This authentication method is a rudimentary cryptographic technique at best; it doesn’t provide mutual authentication. That is, the client does not authenticate the access point — therefore there’s no assurance that a client is communicating with a legitimate wireless network. It is also worth noting that simple unilateral challenge-response schemes have long been known to be weak. They suffer from numerous attacks, including the infamous
“monkey-in-the-middle” attacks covered in Chapter 12.
At least the shared-key authentication process seems to be on the right track.
Here’s how it works:
1. The client requests association.
2. The access point sends random cleartext (128-bit challenge).
3. The client encrypts challenge (the nonce) and sends the result.
4. The access point verifies the encrypted challenge.
5. The access point authenticates the client and sends a positive response and then associates the client.
The IEEE 802.11 specification does not require shared-key authentication.
I Know Your Secret
If we asked you which authentication scheme was more secure, we venture you would answer shared-key authentication. Logically, you might think shared-key authentication is more secure than open-system authentication.
Oddly enough, you’d be wrong. Because of the way the shared-key authentication works, it’s actually less secure. The math shows why: An attacker starts to gather management messages from the authentication process. One message contains the random challenge in cleartext. The next message contains the encrypted challenge, using the shared key. Hey, no problem for the hacker; the RC4 algorithm is not complex: The algorithm does an exclusive OR operation on the plaintext to derive the ciphertext, as follows: P XOR R = C
22_597302_ch15.qxd 8/4/05 7:11 PM Page 284
284 Part III: Advanced Wi-Fi Hacks
Uh-oh. And if you’re with us so far, then the rest is just simple math: If P XOR R = C then C XOR R = P
If P XOR R = C then C XOR P = R
where P = plaintext, C = ciphertext, and R = key stream (or random bytes).
Now the attacker knows everything: algorithm number, sequence number, status code, element ID, length, and challenge text. It’s the attacker’s turn, and here’s how it looks, blow by blow:
1. The attacker requests authentication.
2. The access point responds with a cleartext challenge.
3. The attacker uses the challenge with the value R (as just shown) to compute a valid authentication-response frame by XORing the two values together. Result: He can compute a valid CRC value.
4. The attacker responds with a valid authentication-response message and associates with the AP to join the network.
The attacker did not need to know the shared-key due to the flaw!
(Welcome aboard, stranger. Oops.)
Due to the problems with shared-secret authentication, the standard developers specified WPA and WPA2, both using 802.1X with Extensible Authentication Protocol (EAP).
Have We Got EAP?
So what is 802.1X? Did we mean 802.11 x? No, 802.1X is another IEEE standard, which provides a framework for true user authentication and centralized security management. It provides port level authentication. Initially, the developers offered to standardize security on wired network ports, but others found that the standard had applicability for wireless networking as well.
EAP (Extensible Authentication Protocol) has three components: ߜ The supplicant: A client machine trying to access the wireless LAN.
ߜ The authenticator: A Layer 2 device that provides the physical port to the network (such as an access point or a switch).
ߜ The authentication server: This verifies user credentials and provides key management.
22_597302_ch15.qxd 8/4/05 7:11 PM Page 285
Chapter 15: Authenticating Users
285
When the supplicant requests access to an access point, the AP demands a set of credentials. The user then supplies the credentials that the AP may in turn forward to a standard RADIUS (Remote Authentication Dial-In User Service) server for authentication and authorization. RADIUS is commonly used to authenticate dial-in users. However, 802.1X supports the use of an enterprise authentication server or a database service, including a RADIUS
server; an LDAP directory; a Windows NT Domain; Active Directory Service or NetWare Directory Service. The exact method of supplying credentials is defined in the 802.1X standard EAP (Extensible Authentication Protocol).
Extended EAP is an addition to the Wi-Fi Protected Access (WPA) and 802.11i (WPA2) certification programs, which further ensures the interoperability of secure Wi-Fi networking products for enterprise and government users.
These standards don’t specify a set of credentials, so there are several contenders. EAP is, in effect, an authentication “bucket” that allows developers to create their own methods of passing credentials — and it’s the main security measure in 802.1X. Following are the six commonly used EAP methods in use today:
ߜ EAP-MD5
ߜ PEAPv0/EAP-MSCHAPv2 or PEAPv1/EAP-GTC (Generic Token Card) ߜ EAP-Cisco Wireless a.k.a. LEAP
ߜ EAP-FAST
ߜ EAP-TLS
ߜ EAP-TTLS/MSCHAv2
The Wi-Fi Alliance certifies EAP-TLS, EAP-TTLS/MSCHAPv2, PEAPv0/EAP-MSCHAPv2, PEAPv1/EAP-GTC, and EAP-SIM.
Cisco Systems Inc.’s proprietary LEAP (Lightweight EAP) was the first password-based authentication scheme available for WLANs.
So those are the contenders. Regardless of the one you select, you will need an enterprise authentication server. Whether it is ADS, NDS, LDAP-compliant database or RADIUS is up to you.
Let’s look at each EAP method.
This method seems easy to digest
The EAP-MD5 method relies on an MD5 hash of a username and password to pass credentials to the authenticator from the supplicant. A message digest (MD) or hash is a mathematical summary of all or any part of a message. In 22_597302_ch15.qxd 8/4/05 7:11 PM Page 286
286 Part III: Advanced Wi-Fi Hacks
other words, a hash is the transformation of a string of characters into a usually shorter fixed-length value or key that represents the original string.
This method offers no key management or dynamic key generation, thereby requiring the reuse of static WEP keys. (Smell trouble brewing? We do too.) This method prevents unauthorized users from accessing your wireless network directly, but offers nothing over the proven insecure static WEP
encryption scheme. Attackers can still sniff your traffic and decrypt the WEP key. EAP-MD5 also does one-way authentication, there is no mutual authentication — that is, there is no way for the wireless client to verify the access point. Because of this, a determined attacker could plant a rogue access point, called an evil twin, on your network and fool your wireless clients into thinking that it is a secure access point. Because EAP-MD5 offers no significant improvements over the standard 802.1X, EAP-MD5 is considered the least secure of all the common EAP standards.
Not another PEAP out of you
Protected EAP (PEAP) is an authentication protocol that uses TLS (Transport Layer Security) to enhance the security of other EAP authentication methods.
PEAP for Microsoft 802.1X Authentication Client provides support for EAP-TLS, and uses certificates for mutual authentication, and Microsoft Challenge Handshake Authentication Protocol version 2 (EAP-MS-CHAP v2), which uses certificates for server authentication and password-based credentials for client authentication. Then the client sends the user identity to the authentication server encrypted with the public key of the server. Only the authentication server can read this encrypted information, because it uses its private key.
PEAP works with Active and NetWare Directory Service — that’s a bonus —
but we’re not out of the woods yet. An attacker can trick the authenticator into sending identity or credentials without the protection of a TLS tunnel —
allowing the attacker to intercept the information.
Another big LEAP for mankind
EAP-Cisco Wireless or LEAP (Lightweight EAP) was the first password-based authentication scheme available for WLANs. Like EAP-MD5, LEAP accepts a username and password from the wireless device and passes them to the RADIUS server for authentication. What sets LEAP apart from EAP-MD5 are the extra features it adds. When LEAP authenticates the user, one-time WEP
keys are dynamically generated for that session. This means that every user on your wireless network is using a different WEP key that no one knows, not even the user. LEAP also stipulates mutual authentication.
22_597302_ch15.qxd 8/4/05 7:11 PM Page 287
Chapter 15: Authenticating Users
287
LEAP uses MS-CHAPv1 to pass the logon credentials for both the client and access point authentication. MS-CHAP is the challenge handshake authentication protocol developed by Microsoft and used for remote authentication.
Unfortunately, the version of MS-CHAP that LEAP uses has known vulnerabilities, and can be compromised by a determined enough attacker with the right tools. You can do off-line dictionary attacks. (Hold on, we’ll get there!
Look at the use of asleap and LEAPcracker later in this chapter.) That was EAP-FAST
Extensible Authentication Protocol-Flexible Authentication via Secure Tunneling (EAP-FAST) is a publicly accessible IEEE 802.1X EAP type developed by Cisco Systems. Cisco made it available as of February 8, 2004, as an IETF informational draft.
EAP-FAST uses symmetric key algorithms to achieve a tunneled mutual authentication process. The tunnel establishment relies on a Protected Access Credential (PAC) that can be provisioned and managed dynamically by EAP-FAST through an authentication, authorization, and accounting (AAA) server (such as the Cisco Secure Access Control Server).
You can find more information about EAP-FAST at www.cisco.com/en/US/
products/hw/wireless/ps430/products_qanda_item09186a00802030dc
.shtml.
Beam me up, EAP-TLS
EAP-Transport Level Security (EAP-TLS) is a certificate-based protocol supported natively in Windows XP. Instead of username/password combinations, EAP-TLS uses X.509 certificates to handle authentication. Both the client and the authentication server require certificates to be configured during initial implementation, in other words, mutual authentication. Like LEAP, EAP-TLS
offers dynamic one-time WEP key generation, and authenticates the access point to the wireless client as well as the client to the AP. Implementing EAP-TLS requires a public key infrastructure (PKI) to facilitate the handling and sharing of keys. Some organizations may consider this a show-stopper due to its overall cost and complexity.
EAP-TLS provides eavesdropping protection through the use of TLS.
EAP-TLS works with Active Directory using a Microsoft Certificate Server.
This method is preferable; especially when running a Win32 client and you are already using certificates. Otherwise you have a steep learning curve to conquer.
22_597302_ch15.qxd 8/4/05 7:11 PM Page 288
288 Part III: Advanced Wi-Fi Hacks
EAP-TTLS: That’s funky software
You can use EAP-TTLS to provide a password-based authentication mechanism. EAP-TTLS was pioneered by Funk Software as an alternative to EAP-TLS. In EAP-TTLS implementations, only the authentication server is required to have a certificate. Extensible Authentication Protocol-Tunneled Transport Layer Security (EAP-TTLS) authentication uses a two-stage authentication process, which eliminates the need for a certificate on the user side.
The access point still identifies itself to the client with a server certificate, EAP-TTLS establishes the identity of the server using EAP-TLS. The users now send their credentials as username/password. EAP-TTLS then passes the credentials in either PAP, CHAP, MS-CHAPv1, MS-CHAPv2, PAP/Token Card, or EAP form. Sometimes EAP-TTLS is set to use MS-CHAP. Unfortunately, this method is vulnerable to monkey-in-the-middle attacks (which we cover in Chapter 13).
Because EAP-TTLS does not require that you distribute certificates to users, it’s a far more convenient protocol to use than EAP-TLS.
The downside to EAP-TTLS is that an attacker can trick the server into sending identity or credentials without the protection of a TLS tunnel.
Implementing 802.1X
To implement 802.1X in your wireless deployment, you have to do some research and be prepared to mix and match vendor’s offerings depending on what EAP protocol you plan to use.
First you have to pick a RADIUS server to handle the credential verification.
The following list provides different RADIUS servers that can handle some or all of the EAP standards:
ߜ Microsoft’s Internet Authentication Service (IAS): This is part of Windows 2000, and can authenticate both EAP-TLS and EAP-MD5. If you own a copy of Windows 2000 Server, you already have this RADIUS server, and can access it through Control Panel➪ Add/Remove Programs. You can find information about IAS at www.microsoft.com/windowsserver2003/
technologies/ias/default.mspx.
ߜ Cisco’s Secure Access Control Software (ACS): This server was developed for both the UNIX and Windows platforms. It is a full-fledged TACACS+ and RADIUS server — and, beginning with version 2.6a, it handles wireless authentication with EAP-Cisco Wireless and EAP-TLS.
You can find information about SecureACS at www.cisco.com/en/
US/products/sw/secursw/ps2086/.
22_597302_ch15.qxd 8/4/05 7:11 PM Page 289
Chapter 15: Authenticating Users
289
ߜ Steel Belted RADIUS: Funk Software is generally known for this product.
They have a stripped-down version of that platform (known as Odyssey) that handles wireless authentication exclusively. Odyssey handles the widest range of EAP types by supporting all four of the commonly used protocols, EAP-MD5, EAP-TLS, EAP-Cisco Wireless, and EAP-TTLS. You can find information about Steel Belted RADIUS and Odyssey at www.funk.com/.
ߜ AEGIS: This product, from Meetinghouse Data, offers a RADIUS server that runs on the Linux platform and handles EAP-TTLS and EAP-TLS
authentication. You can find information about AEGIS at www.mtghouse.
com/products/aegisserver/index.shtml.
ߜ freeRADIUS: This is an open-source project that runs on the Linux platform. freeRADIUS supports both EAP-MD5 and EAP-TLS. You can find freeRADIUS at www.freeradius.org/.
The second piece needed to implement 802.1X is an access point that can pass the authentication messages. Because the AP acts only as a conduit for the authentication messages, there are no compatibility clashes between certain access points and different EAP protocols. As long as the EAP protocol fits the standard, then an 802.1X-enabled AP can use it. Generally all enterprise-level APs are either currently capable of handling 802.1X requests either out of the box or through a firmware upgrade for existing equipment. If you have a much smaller environment (or just don’t want to spend the money on enterprise class APs), there are hacks available for home-user-level APs to support 802.1X
authentication.
The final piece of the 802.1X puzzle is the client software. Again, depending on your OS and preferred EAP standard there are several to choose from, such as:
ߜ Cisco: Cisco writes its ACU client piece to make its adapters work with EAP-Cisco Wireless on all flavors of Windows, Apple, and Linux.
ߜ Windows XP: Windows XP has a built-in client for EAP-TLS and EAP-MD5.
It only works properly with Microsoft issued certificates though. This client is supposed to be released for Windows 2000 and CE.NET as well.
ߜ Odyssey: Funk’s Odyssey client currently works on all flavors of Windows except CE. Linux, CE and Apple versions are all due out in the next few of months. The Odyssey client handles EAP-MD5, EAP-TLS and EAP-TTLS, and will soon offer EAP-Cisco Wireless support for non-Cisco hardware.
ߜ AEGIS: The AEGIS client from Meetinghouse Data offers EAP-TLS, EAP-TTLS, and EAP-MD5 support for all flavors of Windows (except CE) and Linux.
ߜ Others: Several open-source clients are being worked on currently, most notably Xsupplicant from the open1X project.
22_597302_ch15.qxd 8/4/05 7:11 PM Page 290
290 Part III: Advanced Wi-Fi Hacks
To use 802.1X, do the following:
ߜ Set the authentication method to Open.
ߜ Have your broadcast keys rotate every ten minutes or less.
ߜ Use 802.1X for key management and authentication.
ߜ Look over the available EAP protocols and decide which is right for your environment.
ߜ Set the session to time out every ten minutes or less.
You can find a list of open EAP issues at www.drizzle.com/~aboba/EAP/
eapissues.html. Also, you can find a commercial EAP testing tool from QA Cafe (www.qacafe.com/suites-eapol.htm). You can use its EAPOL to test your 802.1X authentication. EAPOL is a serious lab-testing tool and is not really intended for “script kiddies.” It provides test coverage of the EAPOL
protocol along with specific EAP-MD5, EAP-PEAP, EAP-TLS, and EAP-TTLS
tests. Check out the site and you’ll find a demo version for Linux.
Let’s look at a major EAP problem: cracking LEAP.
Cracking LEAP
Implementations of 802.1X with LEAP established a strong foothold in the enterprise market. Because LEAP was one of the first solutions available, crackers wrote LEAP crackers. As such, LEAP represents a large security vulnerability for most enterprise wireless LANs. Even so, few enterprises seem to care.
The LEAP weakness was well known from the beginning, because LEAP is essentially an enhanced version of EAP-MD5 with Dynamic Key Rotation and Mutual Authentication. Part of the problem is that LEAP relies on MS-CHAPv2
(Microsoft Challenge Handshake Authentication Protocol version 2) to protect the authentication of user credentials. MS-CHAPv2 is weak because it does not use a salt for the NT hashes, uses a weak 2-byte DES key, and sends usernames in cleartext. So LEAP inherits the following MS-CHAP flaws: ߜ Cleartext username
ߜ Weak challenge/response DES key selection: a 8-bit challenge, hashed with MD4 (Can you say, “You’ve got to be kidding?”)
ߜ Absence of a salt for the stored NT hashes
22_597302_ch15.qxd 8/4/05 7:11 PM Page 291
Chapter 15: Authenticating Users
291
Because LEAP is susceptible to off-line dictionary and brute-force attacks, you should not use LEAP for secure networks. Cracking LEPA is made easier by maintaining a 4-terabyte database of likely passwords with pre-calculated hashes. What most users think is a strong password is usually really weak and breakable within minutes. An attacker can do this with relative impunity and zero chance of detection, since the attack is passive and performed off-line. Cisco feels that you can make LEAP secure by increasing the complexity of the password, thereby thwarting off-line dictionary and brute-force attacks. Although this is true, the possibility that someone actually will create a ten-character, uppercase-and-lowercase, alphanumeric password peppered with special characters is (to put it mildly) slight. Think about the passwords in your organization. Let’s face facts: Any password you expect people to remember is easily cracked using a dictionary or brute-force attack.
For an attacker who’s in a hurry (and most of them are), cracking LEAP is far more productive than cracking the infamously weak WEP protocol. You can usually crack LEAP in several minutes, compared to the hours it might take to crack WEP. So LEAP is a definite target.
There are several LEAP solutions available, including these gems: ߜ asleap
ߜ THC-LEAPcracker
ߜ anwrap
These are discussed in detail in the following sections.
Using asleap
Should you want to test your implementation of LEAP to see whether your organization uses strong passwords, you can use asleap from Joshua Wright.
This tool makes it easy to capture the required login traffic by allowing you to spot WLANs that are using LEAP — and then de-authenticate users on the WLAN, forcing them to reconnect and reenter their usernames and passwords. You’ll find that weak passwords fall rapidly when pitted against a tool such as asleap.
asleap allows you to scan the wireless-network broadcast spectrum for networks that use LEAP, capture wireless network traffic, and crack user passwords. asleap is a busy little program. Here’s a quick look at what it does: ߜ Recovers weak LEAP passwords
ߜ Reads frames from any wireless interface running in RFMON mode
22_597302_ch15.qxd 8/4/05 7:11 PM Page 292
292 Part III: Advanced Wi-Fi Hacks
ߜ Monitors a single channel, or hops channels to look for target networks that are using LEAP
ߜ Actively de-authenticates users on LEAP networks, forcing them to reauthenticate, which makes the capture of LEAP passwords very fast ߜ Only de-authenticates new users, doesn’t waste time on user accounts that aren’t running LEAP
ߜ Reads from stored libpcap files or AiroPeek NX files
ߜ Reads live from any Ethernet network interface
ߜ Uses a dynamic database table and index to do lookups on large files very rapidly
ߜ Cracks PPTP VPN authentication sessions that use MS-CHAP
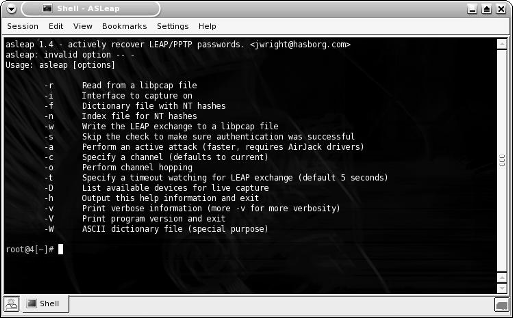
Figure 15-1 shows the syntax for asleap.
Figure 15-1:
The asleap
syntax.
Should you want to find more information about asleap, check out the mailing list at http://lists.sourceforge.net/lists/listinfo/
asleap-users.
The source and Win32 binary distribution are available at http://asleap.
sourceforge.net. The latest version does PPTP as well as LEAP captures.
asleap is released under the GNU Public License (GPL).
Using THC-LEAPcracker
The THC-LEAPcracker Tool suite contains tools to break the NTChallenge-Response encryption technique used by Cisco Wireless LEAP Authentication.
Also included are tools for spoofing challenge packets from Access Points, so you can perform dictionary attacks against all users.
22_597302_ch15.qxd 8/4/05 7:11 PM Page 293
Chapter 15: Authenticating Users
293
You can find THC-LEAPcracker at http://thc.org/releases.php?s=
4&q=&o=.
Using anwrap
Written by Brian Barto and Ron Sweeney, anwrap is a wrapper for ancontrol that serves as a dictionary-attack tool against LEAP enabled Cisco Wireless Networks. It traverses a user list and password list, attempting authentication and logging the results to a file. anwrap causes havoc on NT Networks that have lockout policies in place.
anwrap requires ancontrol and Perl. The ancontrol command controls the operation of Aironet wireless networking devices via the an driver. The anwrap author tested the tool on FreeBSD 4.7.
You can find anwrap at http://packetstormsecurity.nl/cisco/
anwrap.pl.
As a result of cracker tools like asleap, THC-LEAPcracker and anwrap, Cisco has de-emphasized the use of LEAP, especially for those organizations that can’t or won’t enforce strong passwords. They now recommend the use of EAP-FAST.
Network Authentication Countermeasures
If you had your heart set on a life of carefree wireless-network use, maybe you’re ready to put your head in the oven and turn on the gas. Don’t do it.
There are some things you can do to protect yourself. Help is on the way.
WPA improves the 8021.1 picture
Because of the WEP problems, the IEEE approved Wi-Fi Protected Access (WPA) as an interim solution to address those problems. WPA is an example of a software or firmware patch and does not require the hardware upgrade that 802.11i does.
The objective of WPA was to bring a standards-based security solution to the marketplace to replace WEP until the availability of the full-blown IEEE
802.11i Robust Security Network (RSN), an amendment to the existing wireless LAN standard.
22_597302_ch15.qxd 8/4/05 7:11 PM Page 294
294 Part III: Advanced Wi-Fi Hacks
Two key features WPA are its most significant improvements: ߜ 802.1X support: WPA uses 802.1X port access control to distribute per-session keys. Some vendors previously offered 802.11X support even though it was not specified in the standard. The 802.1X port-based access control provides a framework to allow the use of robust upper-layer authentication protocols.
ߜ Temporal Key Integrity Protocol (TKIP): WPA uses the Temporal Key Integrity Protocol (TKIP) to address WEP problems such as IV length and key management.
But WPA is not without its problems. Basically, one can crack Wi-Fi Protected Access Pre-Shared Keys that use short dictionary-word–based passphrases.
You will find software to help with this as well. The WPA Cracker (www.tiny peap.com/page8.html) tool is somewhat primitive, requiring that you enter the appropriate data retrieved via a packet sniffer. The author recommends you use ethereal.
Joshua Wright, who wrote asleap, offers us CoWPAtty (http://new.
remote-exploit.org/), which is another off-line WPA-PSK–auditing tool.
For WPA, certain shorter or dictionary-based keys are easy to crack because an attacker can monitor a short transaction or force that transaction to occur and then perform the crack remotely.
So what do you do? Well, you can:
ߜ Choose better passphrases, especially ones that aren’t made up of words in the dictionary. Select passphrases that are random and at least 20 characters in length.
ߜ Use WPA Enterprise or 802.1X with WPA.
Alternatively, you can use virtual private network technology, such as those technologies described below.
Using WPA2
WPA is still based on the RC4 algorithm, a stream cipher. But a major component of new RSN specification in 802.11i is the use of the Advanced Encryption Standard (AES) for both data confidentiality and integrity.
We strongly recommend you look for and implement technology that supports 802.11i. The 802.11i specification offers Advanced Encryption Standard (AES)-based data link level cryptographic services that are validated under FIPS 140-2. The ratified standard WPA2 uses the AES-CCMP (Counter Mode-Cipher Block Chaining MAC Protocol) algorithm.
22_597302_ch15.qxd 8/4/05 7:11 PM Page 295
Chapter 15: Authenticating Users
295
The AES-based solution will provide a highly robust solution for the future but will require new hardware and protocol changes. (For more about the advantages of 80211i, WPA and AES, see Chapter 14.)
Using a VPN
Your organization may find that it is necessary to use a virtual private network (VPN) scheme. A VPN helps against the risk of eavesdropping by providing an encrypted tunnel between two networks that only authorized persons can access. A tunnel is created using an accepted technique between two end-points. Any data traveling between those two points is secured using encryption. The tunnel is set up and torn down each time you use it. (For more about VPNs, see Chapter 14.)
The solution you decide upon needs to fulfill your business needs. There are many different implementations of virtual private networking. These range from commercial third-party applications to those that are embedded in operating systems. There are several potential VPN solutions as follows: ߜ Point-to-Point Tunneling Protocol (PPTP)
ߜ Layer 2 Tunneling Protocol (L2TP)
ߜ IPSec
ߜ SSH2
You should know that people were kind enough to release other PPTP crackers (in addition to asleap), such as these:
ߜ Anger: Anger, which is a PPTP MS-CHAP challenge/response sniffer that can feed output to L0phtcrack. You can find Anger at www.
securiteam.com/tools/6F00X000AU.html.
ߜ Deceit: Aleph One released deceit, which you can find at http://
packetstormsecurity.nl/new-exploits/deceit.c.
ߜ Ettercap: Don’t forget to look at ettercap (http://ettercap.source forge.net/). Ettercap has plug-ins to sniff PPTP tunnels, decapsulate traffic, and retrieve user passwords. If that makes you think you should use something other than PPTP, you got it in one!
But just when you think another protocol is secure, you find out it isn’t.
There are CheckPoint VPN-1, Cisco VPN Client, Nortel Contivity VPN Client, OpenBSD isakmpd, PGPFreeware, SafeNet, and WAVEsec versions of IPSec that are susceptible to monkey-in-the-middle and buffer overflow attacks.
You can use ike-scan, IKEProbe, ipsectrace, and IKEcrack to test those
22_597302_ch15.qxd 8/4/05 7:11 PM Page 296
296 Part III: Advanced Wi-Fi Hacks
IPSec VPNs. The first three are available from www.forinsect.de/pen test/pentest-tools.html. You can find IKEcrack at http://ikecrack.
sourceforge.net/. You should also try kracker_jack to perform a monkey-in-the-middle attack. kracker_jack is part of AirJack (http://
sourceforge.net/projects/airjack/).
WIDS
Wireless intrusion detection (as detailed in Chapter 11) requires its own system. AirSnare is another tool to add to your Wireless Intrusion Detection System toolbox. AirSnare will alert you to unfriendly MAC addresses on your network — and will also alert you to DHCP requests taking place. If AirSnare detects an unfriendly MAC address, you can track that MAC address’s access to IP addresses and ports — or launch ethereal.
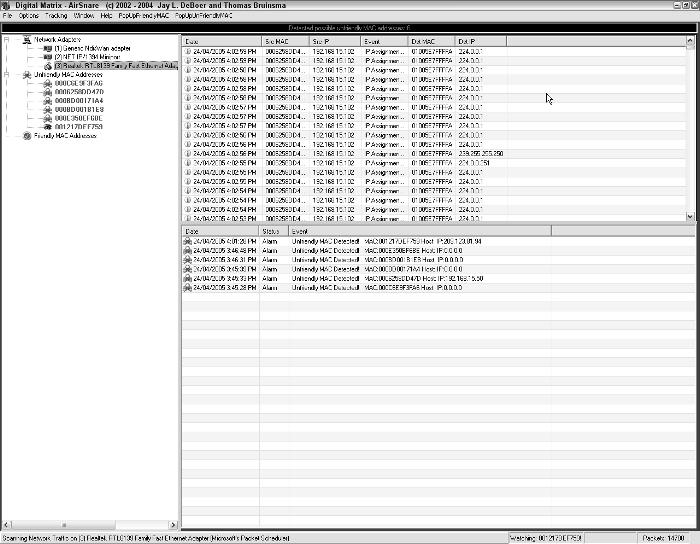
Figure 15-2 shows AirSnare running. You can see that it identified some
“unfriendly MAC addresses.”
You can find AirSnare at www.majorgeeks.com/download4091.html.
Figure 15-2:
AirSnare
finding
intruders.
22_597302_ch15.qxd 8/4/05 7:11 PM Page 297
Chapter 15: Authenticating Users
297
Use the right EAP
As you saw there are several versions of EAP. Which one do you use? You should select one that is non-proprietary. Also, make sure your solution provides protection from a variety of network attacks, including man-in-the-middle, authentication forging, weak-IV attacks (AirSnort), packet forgery (replay attacks), and dictionary attacks. Obviously, your solution should support a variety of user- and password-database types, support password expiration and change, and be flexible, easy to deploy, and easy to manage.
Setting up a WDMZ
You must treat any wireless segment as untrusted — and because it’s an untrusted segment, you must protect yourself. Generally we accomplish this through the use of a security method called a wireless demilitarized zone or WDMZ. The term DMZ has its roots in geopolitics: It is the “no man’s land”
between North and South Korea. Take a stroll in the DMZ, and both sides will take a shot at you. With WDMZs, we won’t shoot you, but we won’t trust you.
You should add a wireless DMZ or screened wireless network between the internal network (that is, your intranet) and the external network (the Internet). This DMZ is where you put your access point, authentication server, Web server, and external DNS server. You use an authentication server to regulate traffic between the untrusted network (the Internet) and the trusted network (the intranet). With wireless, we compartmentalize our networks or segregate our access points — and have a trusted way into the internal network. Bottom line: You should segregate wireless stations onto one or more separate network segments and prevent any direct, unau-thenticated communication with other devices on the wired portion of the network. By compartmentalizing, we can isolate risks and apply controls to mitigate or eliminate the risk.
In summary, you must not allow anyone to place an access point behind your firewall. Place the access point on a segment that the firewall filters.
Using the Auditor Collection
In this book, we showed you a lot of tools. In Chapter 8, we mentioned the Auditor Collection. You can find the Auditor Collection at http://new.
remote-exploit.org/index.php/Auditor_main. The Auditor Collection is an ISO image of Knoppix that includes over 300 tools. It is a “must-have”
22_597302_ch15.qxd 8/4/05 7:11 PM Page 298
298 Part III: Advanced Wi-Fi Hacks
for anyone doing ethical hacking in an organization — especially the wireless variety. It provides the most useful Linux, wireless, ethical-hacking tools.
Fortunately it’s really easy to use.
Auditor installs itself and a complete Linux 2.4.9 kernel on a RAM disk — and executes in RAM. Auditor has complete PC Card support and is ideally run on a laptop computer. You can mount a hard drive or floppy drive and save logs and reports.
Using the Auditor CD-ROM is as easy as the following steps.
1. Open your laptop CD-ROM bay. Then power down Windows or Linux or whatever operating system you are using.
2. Insert the Auditor CD-ROM into the drive and close it.
3. Power up the computer and watch Auditor boot.
If this is the first time you have used Auditor, interrupt the boot process and enter the BIOS set-up program. Make sure that your system will boot from the CD-ROM before it tries the hard drive. Obviously the exact method for doing this depends on your hardware manufacturer and the BIOS you’re using, but follow the on-screen instructions to enter the setup program. When you’re done, you won’t need to do this again.
You see an Auditor splash screen with license and credit information.
4. Should Auditor pause temporarily at a boot: prompt, select the appropriate screen resolution; then hit Enter or Return.
Eventually you see the Auditor desktop, as shown in Figure 15-3: a picture of a centurion.
In the lower-left portion of the window, you see a K with a gear. This is the KDE manager icon.
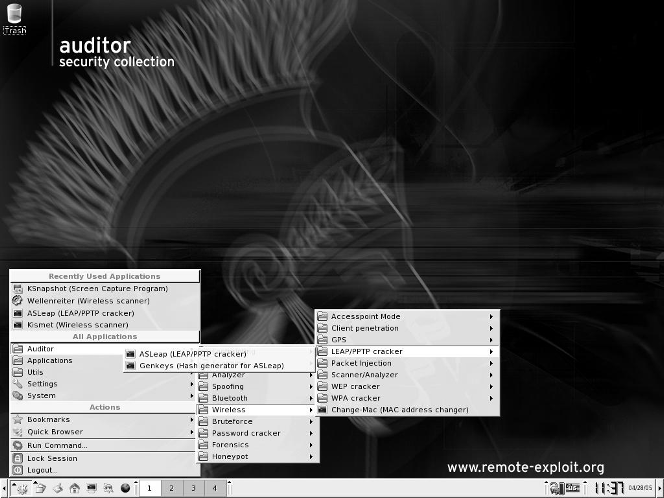
5. Click the KDE manager icon.
A menu pops up.
6. From the menu, select Auditor➪Wireless➪LEAP/PPTP cracker➪
ASLeap (LEAP/PPTP cracker), as shown in Figure 15-4.
This is Auditor’s ASleap tool. The window shown in Figure 15-1 opens.
Take some time and explore all the programs available with the Auditor CD-ROM. Whenever you want to use Auditor, just put the disk in the drive and turn on the power. When you’re finished with Auditor, shut down, remove the Auditor CD-ROM, and reboot. Your system will boot whatever operating system it gets from your hard drive (assuming you have set it up that way).
Now you have a handful of wireless networking ethical-hacking tools. So you have no excuse. Dedicate a laptop to ethical hacking and get cracking.
22_597302_ch15.qxd 8/4/05 7:11 PM Page 299
Chapter 15: Authenticating Users
299
Figure 15-3:
Auditor
desktop.
KDE Manager icon
Figure 15-4:
LEAP
crackers.
22_597302_ch15.qxd 8/4/05 7:11 PM Page 300
300 Part III: Advanced Wi-Fi Hacks

23_597302_pt04.qxd 8/4/05 7:11 PM Page 301