Hacking Wireless Networks (2015)
Part IV
The Part of Tens
Chapter 17
Ten Wireless Security-Testing
Mistakes
In This Chapter
ᮣ Skipping planning
ᮣ Not involving others
ᮣ Not using a methodology
ᮣ Forgetting to unwind . . . that’s unbind
ᮣ Forgetting to get permission
ᮣ Using the wrong tools
ᮣ Affecting networks through testing
ᮣ Using data improperly
ᮣ Not reporting results and following up
ᮣ Breaking the law
From our experience, ethical hackers tend to make the same mistakes over and over again. Perhaps they learned from each other. We see no reason for you to make these same mistakes. In no particular order, the top ten security testing mistakes are as follows:
Skipping the Planning Process
As we stress in Chapter 2, planning is a tedious but extremely important task.
You must clearly define the boundaries of your work to avoid any conflict or question of misdeed. Despite all attempts at thoroughness and efficiency in your testing, one of the largest factors in determining the success of a security test is the thoroughness of your planning. The planning process is handled far from the tester’s toolbox. It requires a certain level of project 25_597302_ch17.qxd 8/4/05 6:58 PM Page 308
308 Part IV: The Part of Tens
management and communication skills. Your plan is the company’s official declaration of what it wants to accomplish and how it wants to do it.
Remember: Very few people ever arrive at their destinations without first intending to get there.
At a minimum, your plan should specify the following:
ߜ The roles and responsibilities for everyone involved in the ethical hack.
ߜ The level of involvement of each tester and the importance of her participation in the team.
ߜ The schedule for when the testing will take place. Management may prefer that the testing be done when traffic is low, which might translate into late nights, early mornings, or weekends.
Your security defense budget is likely small, so you need to operate with efficiency and creativity to do more with less. So plan carefully and meet the expectation of the plan. Otherwise, in the future, your management or customer may see security testing as an unnecessary cost.
Not Involving Others in Testing
Often the trick to a successful test lies in observing the details. One such detail is the inclusion of other individuals from your organization in the testing process. Talk to your network professionals. Get people involved up-front during planning. They may help you save time or money by providing insight into the network that you might not have.
Ensure that the testing process is closely monitored by others. Involving others during the process may save you reporting time or may save your hide if you’re accused of something you did not do.
Not Using a Methodology
Ethical hacking is different from penetration testing. Ethical hacking is extremely methodical and relies on a method. In Chapter 2, we discuss the concept of the scientific method. You need to adopt or develop a method.
Your method should consist of the following steps: planning, testing, and reporting. The method may consist of best practices, such as Open-Source Security Testing Methodolgy Manual (OSSTMM) and Information System Security Assessment Framework (ISSAF). (For more on these terms, refer to Chapter 2.)
25_597302_ch17.qxd 8/4/05 6:58 PM Page 309
Chapter 17: Ten Wireless Security-Testing Mistakes
309
Although having a testing methodology is important, don’t constrict the creativity of the tester by introducing strict methods that affect the quality of the test. Be flexible and leave some tasks open to interpretation.
Forgetting to Unbind the
NIC When Wardriving
Later on in this chapter, we talk about the legalities of ethical hacking. For now, we want to avoid doing anything that someone might perceive as illegal or unethical. At no time should you connect to any access point that isn’t yours. One of the things you can and should do is ensure that your wireless adapter does not authenticate with an access point you stumble upon. This is called autoconnection or accidental association. Avoiding autoconnection is essential.
Some client adapters are more likely than others to connect with any open access point that comes into range, given enough time to perform a DHCP
transaction.
To avoid autoconnection, sometimes you must simply disable your client adapter’s client utility before setting out on a wardrive. But that may not work. The only foolproof way to prevent autoconnection is to disable all networking protocols, that is, TCP/IP, NetBEUI, NetWare, and other communication protocols on your wardriving computer. Without a networking protocol, the computer cannot communicate. However, even without a networking protocol, the Wi-Fi client adapter still gathers frames and NetStumbler, or Ethereal can display them.
Your local law enforcement organization may interpret the simple act of associating as computer trespass, so you need to ensure you don’t accidentally associate. The solution is simple. All you need do is unbind the TCP/IP protocol from the wireless adapter.
With accidental association, not only do you have a potential legal problem, but you also have a potential wardriving problem as well. Client adapters that autoconnect to an access point sometimes place the SSID of that access point in the SSID field of the wireless adapter’s operating profile. From that point forward, your wardriving program will not log any additional stations with any other SSIDs. This effectively ends your wardrive, even when you drive around different neighborhoods for a long time.
25_597302_ch17.qxd 8/4/05 6:58 PM Page 310
310 Part IV: The Part of Tens
If you are a DHCP client, then you can use the Windows ipconfig.exe command to release all current TCP/IP network configurations. Follow these steps:
1. Select Start➪Run.
2. Enter command in the Open dialog box in the Run window.
3. At the command prompt, type ipconfig /release_all.
This releases all IP addresses and sets them to 0.0.0.0. If you want more information about this command, type ipconfig /?.
If you still use Windows 98/98SE or Windows ME, you can use the built-in WINIPCFG.exe. It is easy to use this program, but if you’re not sure, read the help file. If you’re a Linux user, you can use the ipconfig /renew command.
You can get a graphical version of ipconfig by downloading wntipcfg.exe from www.microsoft.com/windows2000/techinfo/reskit/tools/
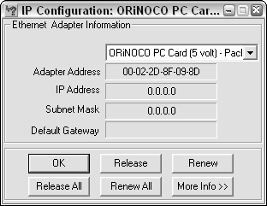
existing/wntipcfg-o.asp. Figure 17-1 shows wntipcfg in action. It’s simple to use: To release all IP addresses and set them to 0.0.0.0, just click the Release All button. For more information about how to use wntipcfg, Microsoft has excellent help on the download page for the care and feeding of the program.
Figure 17-1:
Using
wntipcfg
to release IP
addresses.
If you are going to use MiniStumbler or CENiffer to release the IP addresses, you need to manually change the IP address to an unusable address. To change the IP address in Pocket PC, follow these steps:
1. Choose Start➪Setting➪Network Adapters.
2. Select your wireless card and click Properties.
3. Select the Use Specific IP Address radio button and enter 0.0.0.0 for the IP address, Subnet mask, and Default gateway.
25_597302_ch17.qxd 8/4/05 6:59 PM Page 311
Chapter 17: Ten Wireless Security-Testing Mistakes
311
The only way to prevent autoconnect in Windows XP is to disable the TCP/IP
protocol from the wireless card or adapter before you go wardriving. Without the TCP/IP protocol, your client can connect but not communicate. How you disable networking protocols depends on your operating system. For Windows XP, it’s easy to do:
1. Choose Start➪Control Program.
2. Double-click Network Connections.
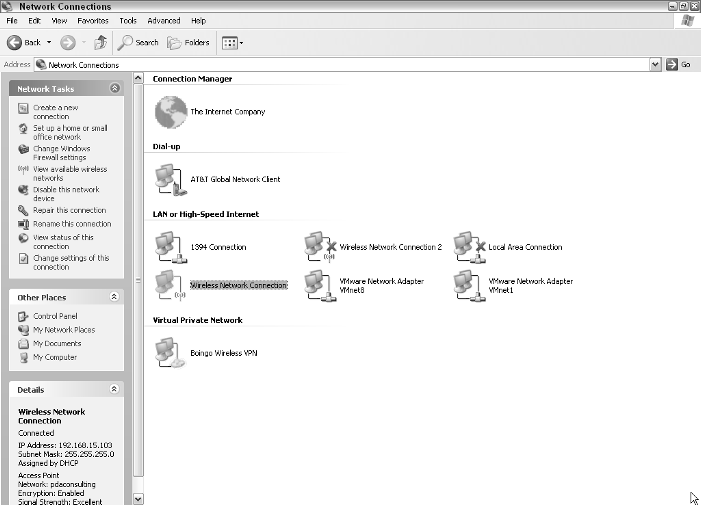
You should see a window similar to the one in Figure 17-2.
3. Highlight the wireless network connection.
4. From the Network Tasks list, select Change Settings of This Connection.
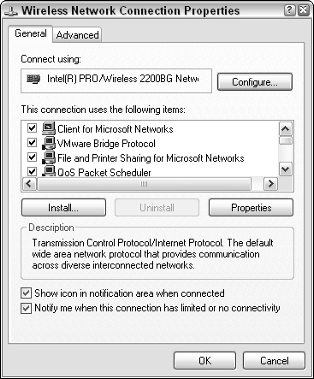
You should see a window like the one shown in Figure 17-3.
5. Scroll down in the list of installed protocols until you see Internet Protocol (TCP/IP). Highlight this item.
6. To the left, you will find a check box. Uncheck the box.
7. Click OK.
8. Restart your computer.
Figure 17-2:
Network
Connections
window.
25_597302_ch17.qxd 8/4/05 6:59 PM Page 312
312 Part IV: The Part of Tens
Figure 17-3:
Wireless
Network
Connection
Properties
window.
When you restart your computer, you can still use your wireless card; that is, the card is not disabled, but the TCP/IP protocol is no longer bound to the card. You cannot use the protocol to send packets.
Enabling and disabling networking protocols is a lot of work, so we recommend getting a dedicated machine for your ethical hacking.
Failing to Get Written Permission to Test
Performing security tests of any kind against any network without explicit written permission from the appropriate authority is not a good thing. Here are some reasons why:
ߜ When you undertake an ethical hack, you may perform some actions that are similar, if not identical, to those carried out by a real attacker.
Without documentation, how can anyone tell the ethical hackers from the not-so-ethical ones?
ߜ Your testing may result in the compromise of the network.
ߜ You shouldn’t do Denial-of-Service tests without explicit permission.
Most organizations frown on you bringing down the system and preventing people from doing their work.
ߜ Even when you have an agreement, your client or boss may not accept, for instance, that you may uncover classified information or gain access to internal resources.
25_597302_ch17.qxd 8/4/05 6:59 PM Page 313
Chapter 17: Ten Wireless Security-Testing Mistakes
313
For these reasons, you should always obtain clear authorization from the appropriate authority to perform your ethical hack. Notice the use of the word appropriate in the prior sentence. It is very important that the right person has given permission to you. You should obtain authorization from someone who has the authority to approve your work.
Regardless of whether you work for the company or you are an external consultant, make sure the approval is printed on company letterhead and signed by the responsible person. If you are an external consultant, make sure you have a signed contract.
One last thought on Denial-of-Service testing. As a rule, security assessment methodologies such as OSSTMM or ISSAF do not require the tester to try a Denial-of-Service exploit. The tester should only use gathered evidence to provide a proper review of security processes and systems. So, unless you have a compelling reason to do so, you should not perform Denial-of-Service tests.
Failing to Equip Yourself
with the Proper Tools
Just like any other professional or tradesperson, you rely heavily on your tools. You must make sure your tools are kept tuned and ready to go. You should know where the tools came from, how the tools work, and test them in a restricted test area before using the tools for an ethical hack. You should not use a new or unfamiliar tool on a production system or network. Don’t trust your providence to unsigned tools. If the developer signed the software with a GPG (www.gnupg.org) or other signature, you should verify the signature by using the correct key. Otherwise, you cannot be sure the program is not a Trojan horse itself.
Authors frequently update their software to fix security and other problems.
So ensure you’re using the latest version of your tools. For example, you can download the Kismet development code by typing the following at the command prompt:
svn co http://www.kismetwireless.net/code/trunk kismet-devel This command fetches the latest development version for you.
To protect yourself, your information, and your network, you should use dedicated equipment for your testing. Sending e-mail and performing other administrative or personal tasks on your testing machine is just asking for 25_597302_ch17.qxd 8/4/05 6:59 PM Page 314
314 Part IV: The Part of Tens
trouble. You don’t want a virus or Trojan horse on a system you use for security testing. Do these tasks on another machine. When you have access to absolutely only one machine, use different boot partitions. (Consider using Symantec’s PartitionMagic, which we cover in Chapter 4.) This guarantees the integrity of your testing machine.
Another action you can take to protect the integrity of the machine is to make sure it is fully patched. Install the latest patches for the operating system and any applications installed on the tester’s machine. To keep the cruel and unforgiving world at bay, implement a host-based firewall and antivirus software.
Ensure that your team has licenses for all the commercial tools you use. If you decide to use freeware or open-source tools, make sure the agreement or license allows you to do so. Some of the developers of free software don’t want you using their software for commercial gain. So make sure all your tools are legal, updated, and fully licensed.
Over-Penetrating Live Networks
Ethical hacking follows no steadfast rules, but there are some commonsense rules to consider. One is don’t test until you negatively impact networks or systems. Hopefully, you are testing at times that won’t impact clients of the network, so perhaps this is not an issue. Always stay professional and you should not have any ethical problems such as negatively impacting your target.
Using Data Improperly
You can share the data from your ethical hack with like-minded people and your boss or customer, you can show it to anyone who can change things for the better, and you can use it for education, but don’t use the data for personal gain.
Don’t use anything you learn to embarrass anyone — especially your boss.
Failing to Report Results or Follow Up
The reporting phase is as important as the testing itself. Professionals know that reporting is critical and takes time. Remember to include enough time in your budget for the reporting process. Writing a great report requires a great 25_597302_ch17.qxd 8/4/05 6:59 PM Page 315
Chapter 17: Ten Wireless Security-Testing Mistakes
315
deal of effort. Peter has found that writing and getting agreement to a formal report, takes three times as long as the work itself. It really doesn’t matter how good your work is if you cannot tell the story well.
Also, report the risk vulnerabilities you’ve discovered promptly. Don’t wait until someone exploits the vulnerability or until you report your findings.
Your company or customer would have a difficult time proving due diligence if you knew about the vulnerability but did not report it. In these circumstances, not only should you report these items to your boss or customer, but you must also present them with a practical solution.
Before you start writing your report, plan the activities you need to prepare and submit the report. Plan to share your findings with all those with an interest, such as network administrators and your sponsor. You should also plan to share a draft with people. These steps take time.
Your report is one way for you to show the completeness and rigor of your testing methodology. Your peers can review your methods, your findings, your analysis, and your conclusions and decide whether you came to the correct conclusions based on what you report. Some thoughts on reporting: ߜ Reports should include the following sections:
• Executive Summary
• In Scope Statement
• Out of Scope Statement
• Objectives
• Nature of the Testing
• Analysis
• Summary of Findings
• Vulnerability Summary
• Countermeasure(s) to Control the Vulnerability
• Conclusion
• Supporting Documentation
ߜ Reports should include all assumptions regarding the network or system under review.
ߜ Reports should include all unknowns, and they should be clearly marked as unknowns.
ߜ Reports should state clearly all states of security found, not only failed security measures.
25_597302_ch17.qxd 8/4/05 6:59 PM Page 316
316 Part IV: The Part of Tens
ߜ Reports should be based on the established deliverable.
ߜ Reports must use only qualitative metrics for gauging risks based on industry-accepted methods.
ߜ Reports should include practical solutions toward discovered flaws.
Many organizations make the major mistake of not following up swiftly. It’s one thing to identify vulnerabilities; it’s another thing altogether to fix the problem.
If you don’t intend to fix the problems promptly, then don’t bother with the assessment. You are definitely in a worse legal position if you don’t fix known problems than if you don’t know about the problems. In this case, ignorance is bliss — or judicious.
Failing to follow up on the findings of the testers has a negative effect on the testers as well: It’s demoralizing. Nothing is worse than doing your job and doing it well and discovering that nobody notices or cares. Because you have placed a lot of trust in your ethical hackers, not valuing their work might not be such a good tactic.
Finally, if you don’t follow up without delay, you also risk wasting the money you spent on the test itself. Most information technology environments are extremely dynamic; you may have to repeat the tests if you don’t follow up straightaway.
Breaking the Law
You get in your car and drive around the neighborhood. But you’re not running errands. Instead, you’re using your laptop with Windows XP, NetStumbler, an omnidirectional antenna, an ORiNOCO Wi-Fi card, and your Pharos GPS
device to collect status information and the location of wireless networks. As you drive, NetStumbler records open networks it finds. After you finish driving around the neighborhood, you map the location of open and closed networks and upload the map to the Internet. Given this scenario, the following questions arise:
ߜ Is this illegal? Conceivably, this is trespass and illegal access.
ߜ Is this unethical or unprofessional? Technology is not bound to ethics.
It is the application and use or abuse of technology that brings the question of ethics in.
25_597302_ch17.qxd 8/4/05 6:59 PM Page 317
Chapter 17: Ten Wireless Security-Testing Mistakes
317
ߜ Is wardriving harmless fun or a computer crime? Like hacking itself, the answers are not black and white. There are shades of gray or incon-spicuous ethical shades to wardriving that most people don’t really understand. Wardriving in and of itself is quite innocuous, legal, and benign. It is what you do with the information that is important.
In 2004, news programs on many U.S. television stations carried stories about wardriving. In these stories, a local security “expert” shows the reporter how easy it is to connect to a wireless access point. In one particular segment, a Minneapolis-St. Paul TV station showed the “expert” actually sending something to print on the compromised network. One would think that at best that such activity is unethical, if not illegal. However, the legality of wardriving is untested. Regardless of whether wardriving is legal, as a professional, you should avoid any perception that you are taking part in illegal or unethical behavior. Remember that if you are doing the ethical hacking on behalf of your company, then your behavior reflects on the company.
Grove Enterprises Inc. (www.grove-ent.com/LLawbook.html) has published some information on the legal aspects of wardriving on its Web site.
There are some really interesting and intriguing facts on the site. Most Americans are ill-informed of the pertinent laws. The laws in some states are so archaic or vague that the police could probably arrest you simply for listening to the radio.
Many states are trying to repeal or amend monitoring laws. For instance, New Jersey and Kentucky have amended their laws, and ethical hackers in those states have little fear of prosecution. On the other hand, in California, monitoring cordless telephone calls is illegal. But the common-law landscape is ever-changing. The laws at any time are no more than a snapshot. Lawmakers pass new laws every day, while discarding or amending old ones. This is inevitable. So what can you do? You need to keep as informed as you can about your local laws to be completely safe.
In the meantime, the current monitoring laws break down into three categories:
ߜ Outright bans on monitoring by everyone: Outright bans on monitoring exist in Florida, Indiana, Kentucky, Michigan, Minnesota, and New York. Usually, the laws make allowances for people like amateur radio operators, journalists, and law enforcement personnel.
ߜ Outright bans on monitoring by criminals: South Dakota and Rhode Island prohibit criminals they list in the acts from having scanners.
ߜ Bans on illegal use of discovered information: California, Minnesota, Nebraska, New Jersey, New York, Oklahoma, Vermont, and West Virginia fall in this category. In simple terms, their laws forbid the improper use (not the listening to) of information.
25_597302_ch17.qxd 8/4/05 6:59 PM Page 318
318 Part IV: The Part of Tens
Let the master answer
A key doctrine in the law of agency is respon-
connect to an access point while performing an
deat superior, which is Latin for “let the master ethical hack for your employer in the name of the
answer.” This doctrine provides that a principal
employer, your employer has responsibility for
(your employer) is responsible for the actions of
your actions. So if you cause harm, the injured
his/her/its agent (you) in the “course of employ-
party may hold your employer accountable. Hey,
ment.” Thus, when you, acting as an agent, enough legalese. We only play lawyers on TV.
Although North Dakota prohibits possession of a radio that will both transmit and receive police frequencies, other states do not appear currently to have laws restricting radio listening. To protect yourself, you should also familiarize yourself with the Electronic Communications Privacy Act (ECPA) and any state statutes that support the ECPA.
New Hampshire has an interesting approach to wardriving. House Bill 495
effectively legalizes many forms of wardriving. Legal eagles have interpreted this law to mean that any unsecured wireless network in the state of New Hampshire is fair game. Therefore, if wireless network administrators in New Hampshire want to prosecute people for hacking into their wireless net works, they need to have taken action to secure their networks. Not surprisingly, the Electronic Freedom Frontier (www.eff.org) feels that the New Hampshire law is a step in the right direction.
Warchalking, a seemingly innocuous activity, may actually run afoul of the law, and not just because warchalkers are tempting others to break laws.
Your jurisdiction may have laws against graffiti or marking sidewalks.
Also, some states prohibit having or watching screens like TVs and computers while you’re driving.
The one thing we, as “pseudo-legals,” know is that there are no cut-and-dried answers to these legal questions. As with any questionable activity, subtle nuances rule the day. However, simply driving around a city searching for the existence of wireless networks, with no ulterior motives, is most likely legal.
Courts haven’t exhaustively tested the concept, but the common assumption is that simply discovering open wireless networks is legal.
But if you search for an open network in order to steal Internet access or commit computer crimes, then the wardriving you performed was done in a malicious manner, and most courts will treat it as such. What is certainly illegal is connecting to and using networks without the network owner’s 25_597302_ch17.qxd 8/4/05 6:59 PM Page 319
Chapter 17: Ten Wireless Security-Testing Mistakes
319
permission, what most people call “breaking into a network.” Existing laws, which vary from state to state, already cover “cybercrime,” such as using a neighbor’s wireless network for downloading child pornography or broadcasting spam. As we mention in Chapter 2, charges against individuals so far have related to other crimes, such as violations of the CAN-SPAM Act of 2003, and not to the wardriving activities in and of themselves. In Toronto, for example, a man piggybacked on a wireless connection to download child pornography. The man was not charged with theft of services by the ISP, but with the more vile crime of possession of child pornography.
So you must demonstrate the required propriety when engaging in ethical hacking. Here are some simple rules to follow as an ethical hacker: ߜ Don’t touch.
ߜ Don’t look.
ߜ Don’t play through.
ߜ Don’t violate your security policy.
ߜ Don’t operate beyond your agreement.
ߜ Don’t operate beyond the scope of the original work unless you have an official, signed-and-approved request.
In other words, you should not examine the contents of a network; add, delete, or change anything on the network; or use the network’s resources.
Follow the ecological advice given to hikers and “take only pictures and leave only footprints.” Act responsibly, do the right thing, and don’t trespass onto private Wi-Fi networks.
In conclusion, the law hasn’t entirely caught up with networking as a whole, much less the peripheral issues of ethical hacking. So, obey the law as it exists today and don’t engage in activity that is unethical. Public perception is extremely important.
25_597302_ch17.qxd 8/4/05 6:59 PM Page 320
320 Part IV: The Part of Tens
26_597302_ch18.qxd 8/4/05 7:27 PM Page 321