Hacking Wireless Networks (2015)
Part I
Building the
Foundation for
Testing Wireless
Networks
Chapter 3
Implementing a Testing
Methodology
In This Chapter
ᮣ Appreciating the importance of formal procedures
ᮣ Finding out what others can easily see
ᮣ Scanning for live systems
ᮣ Enumerating wireless systems to see what’s running
ᮣ Finding and exploiting the security holes
Before you start testing your wireless network for security vulnerabilities, it’s important to have a formal, ordered methodology in place. Ethical hacking is more than just running a wireless-network analyzer and scanning willy-nilly for open ports. There are some formal procedures that should be incorporated into your testing to do it right and get the most of it — these, for example:
ߜ Gathering public information such as domain names and IP addresses that can serve as a good starting point
ߜ Mapping your network to get a general idea of the layout ߜ Scanning your systems to see which devices are active and communicating ߜ Determining what services are running
ߜ Looking for specific vulnerabilities
ߜ Penetrating the system to finish things off
The next few sections discuss these points in greater detail. By planning things out (in the ways we covered in Chapter 2) and having specific goals and methods — even checklists — you’ll know where you’re headed and you’ll know when your testing is complete. It’ll make your job a lot easier, and document the steps you take. Speaking of which . . .
08_597302_ch03.qxd 8/4/05 7:00 PM Page 32
32 Part I: Building the Foundation for Testing Wireless Networks Keep a log of what you do and when. Your logging can be more thorough if you take screen captures with a tool such as SnagIt (available at www.tech smith.com). Such visual samples come in handy when you know you won’t be able to reproduce the same information on your screen again. Logging can be helpful if you need to go back and look at which tests you ran, figure out what worked and what didn’t, or refer to special notes. It’s also just the professional thing to do, and wise in case any problems crop up. For instance, you can show your boss or client what you did and when you did it if he needs to track a potential security intrusion.
When you’re performing any type of information-security testing, it’s important to work methodically and make sure you’re running the right tests on the right systems. This will help ensure you find the greatest number of security weaknesses. A nice side benefit is that it can minimize sloppiness and help keep you from crashing your systems.
Ethically hacking your wireless network requires testing your systems with a pretty specific goal in mind: a more secure network (well, yeah). Getting there involves looking at your wireless systems from many perspectives —
including that of a hacker outside your work area and that of a regular user inside your work area.
Be flexible in your methodology. You must adapt the rules of warfare to your enemy. No security-testing parameters are set in stone. The bad guys are using the latest tools, so you need those tools. They’re breaking in from across the street, so you need to test from across the street. They’re searching for network-configuration information from across the Internet — and you should, too. No two ethical hacks are alike; you may need to adjust your procedures if the need arises.
Determining What Others Know
Hackers start out by poking and prodding their victims’ systems to find weaknesses — and you should, too. Look at your network from an outsider’s perspective; find out what’s available to just about anyone. This is even more important in the wireless realm because we don’t have the added veil of physical security (as we do with our hard-wired systems).
What you should look for
Here’s what you need to search for to get started with your wireless network testing:
08_597302_ch03.qxd 8/4/05 7:00 PM Page 33
Chapter 3: Implementing a Testing Methodology
33
ߜ Radio-signal strength
ߜ Specific SSIDs that are being broadcast
ߜ IP addressing schemes
ߜ Encryption such as WEP or VPN traffic
ߜ Hardware makes and models
ߜ Software versions
Footprinting: Gathering what’s
in the public eye
The first formal step in your ethical-hacking methodology is to perform a high-level network reconnaissance called footprinting. If you’re performing a broader information-security assessment (the sort Kevin covered in HackingFor Dummies), you may want to search for things like employee names, patents and trademarks, or company files. You can gather this information through places such as your organization’s Web site or the U.S. Patent and Trademark Office Web site (at www.uspto.gov), or by using a search engine such as Google (www.google.com). Because wireless networks are more infrastructure-based and localized, publicly available information might not be as prevalent as it is for your other network systems. It still pays to take a gander and see what’s out there.
Searching with Google
An excellent tool to get started with this process is Google. In fact, Google is one of our favorite tools for performing security assessments in general. It’s amazing what you can do with it. You can perform a ton of Web and newsgroup queries to search for information about your wireless systems. You can perform keyword searches and more detailed queries (using Google’s advanced tools) to look for network configuration information and more that has been accidentally or intentionally made public on the Internet. This information can give a hacker a leg up on attacking your wireless systems. For example, using advanced queries in Google, you can search for:
ߜ Word-processing documents
ߜ Spreadsheets
ߜ Presentations
ߜ Network diagrams
ߜ Network Stumbler mapping files
ߜ Network-analysis packet files
08_597302_ch03.qxd 8/4/05 7:00 PM Page 34
34 Part I: Building the Foundation for Testing Wireless Networks Foundstone has a neat Google query tool that performs some advanced Google queries that you might not have thought up on your own at www.foundstone.com/resources/freetools.htm
We show you how to put Google to work for you with various tests we’ll outline in later chapters.
Searching Wi-Fi databases
The next area to search for information about your wireless systems is online Wi-Fi databases. These databases contain information such as SSIDs, MAC
addresses, and more on wireless APs that have been discovered by curious outsiders. To get an idea what we’re talking about, browse to the WiGLE database at
www.wigle.net/gps/gps/GPSDB/query/
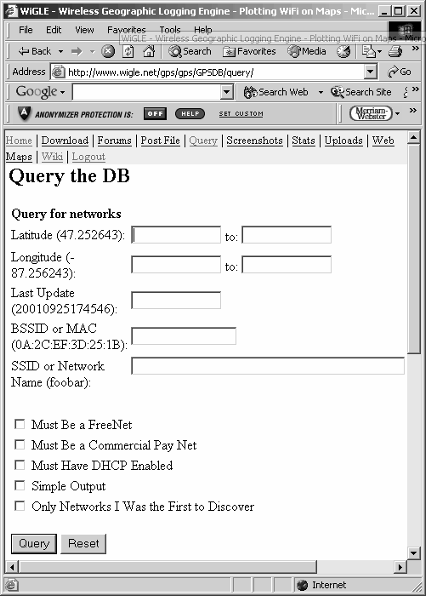
and see if any of your APs are listed. (You’ll have to register if you’re a first-time visitor.) Once in, you can submit various search options as shown in Figure 3-1.
Figure 3-1:
Wireless-
query
options of
the WiGLE
database.
08_597302_ch03.qxd 8/4/05 7:00 PM Page 35
Chapter 3: Implementing a Testing Methodology
35
You can also check to see whether your AP is listed at another wireless lookup site at www.wifimaps.com.
You should also look up your domain name(s) at www.whois.org and your IP
addresses at the American Registry for Internet Numbers (ARIN) site http://
ws.arin.net/cgi-bin/whois.pl. These databases may be providing information about your wireless systems that you’re not aware of or should not be advertising altogether.
Mapping Your Network
When you’re satisfied that you’ve gotten a general view of what the general public can find out about your network without breathing hard, the next step is to create a network map to show how your wireless systems are laid out.
You should do this from both inside and outside your network. That’s necessary because wireless networks have a third dimension — the radio wave dimension — and tossing out all those radio waves allows them to be discovered from either side of your firewall or physical building. This allows you not only to see internal and external configuration information but also to see configuration information specific to wireless radio waves that are transmitted both “inside” and “outside” the network.
Compared to the way a typical wired network does its job, a wireless network opens a whole new dimension. Radio waves are like a virtual “third dimension”
that can (in effect) allow hackers to jump over conventional boundaries.
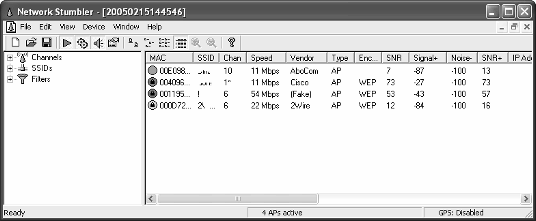
Here are some suggestions for the best tools to help you map your network: ߜ Network Stumbler: The best tool to get started creating both internal and external maps of your wireless APs is Network Stumbler (www.net stumbler.com/downloads). This Windows-based tool allows you to scan the airwaves from outside your building to see what any hacker sitting in the parking lot or driving by can see. You can also run it from inside the confines of your building to look for any additional wireless APs that don’t belong. Figure 3-2 shows the information that Network Stumbler can gather about your wireless network. (Note that the MAC
addresses and SSIDs have been concealed to protect the innocent.) ߜ AiroPeek: A full-blown wireless network analyzer, or sniffer, AiroPeek (www.wildpackets.com/products/airopeek) is another great tool for gathering network map information. We demonstrate its features in later chapters.
08_597302_ch03.qxd 8/4/05 7:00 PM Page 36
36 Part I: Building the Foundation for Testing Wireless Networks Figure 3-2:
Network
Stumbler,
showing
various data
on APs
it has
discovered.
ߜ Cheops-ng and QualysGuard: You’ll want to gather not only information transmitted via RF but also any information about the wireless network that’s only accessible via the internal wired network infrastructure. To do this bit of collecting, you can use a tool such as the open-source Cheops-ng (http://cheops-ng.sourceforge.net) or the commercial QualysGuard (www.qualys.com). Using either tool, you can create a network map of the inside of your network, which helps lay out the general IP addressing schemes and internal hostnames. You can also do this sort of mapmaking from outside your network to determine the names, external IP addresses, and registered domain name system (DNS) hostnames of publicly available hosts. Both methods give your wireless network more of a backbone, so to speak.
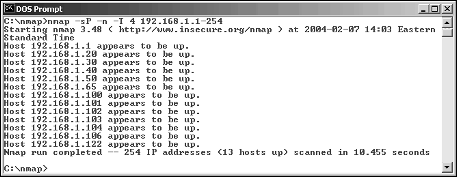
ߜ nmap and fping: The other network mapping utilities in this list often utilize the Internet Control Message Protocol (ICMP) to determine which systems are “alive” on the network. Another way you can do this is by performing a ping sweep of your network, using a utility such as nmap (www.insecure.org/nmap) for Windows computers or a utility such as fping (www.fping.com) for UNIX and Linux. As shown in Figure 3-3, these tools won’t create pretty graphical layouts of your network (that’s the sort of thing you get from the network-mapping programs) but they’re still very beneficial.
Figure 3-3:
nmap ping
sweep,
showing
which
systems are
alive on a
network.
08_597302_ch03.qxd 8/4/05 7:00 PM Page 37
Chapter 3: Implementing a Testing Methodology
37
On the outside looking in
It may seem tricky to try and scan your network
can assign to your test computer and plug in on
from the “outside” — that is, from the public
the “public” side of your firewall or router that is
Internet. This is actually pretty simple. All you
connected directly to the Internet.
need is an available public IP address that you
Note that the utilities we’ve mentioned in this section aren’t necessarily going to be able to decipher which live systems are wireless and which ones are wired. It’s up to you to determine which IP networks, IP addresses, and specific hostnames belong to your wireless devices. (You do have a recent network diagram, don’t you? Just checking.)
Now you know which systems are alive on your network. The next step is to scan wireless systems for more information, such as open ports, hostnames, and more.
Scanning Your Systems
You’ve already gathered the higher-level information about your wireless systems such as SSIDs and IP addresses. You can find out more through a process called enumeration. Enumeration is when you examine a system and make an actual list of all the details you can discover about what it does and how. With enumeration, you can find
ߜ Live wireless hosts (APs and ad-hoc clients)
ߜ RF signal strength
ߜ Whether WEP encryption is enabled
ߜ Which network ports are open on wireless APs and clients Network Stumbler, the friendly network-mapping tool mentioned a bit earlier, can not only find live wireless hosts (APs and ad-hoc clients), but it can also grab more in-depth information — for example, RF signal strength and whether WEP encryption is enabled. No surprise that Network Stumbler is a good tool for enumeration.
You can also get a little more in-depth goodies by using a port scanner such as nmap or SuperScan to poke and prod the network, looking to find out what network ports are open on your wireless APs and clients. You can find SuperScan at
08_597302_ch03.qxd 8/4/05 7:00 PM Page 38
38 Part I: Building the Foundation for Testing Wireless Networks www.foundstone.com/resources/proddesc/superscan.htm
Check your software licenses — even on free software — to make sure you’re abiding by their restrictions. Many licenses state that the software cannot be used for commercial purposes. If you’re doing your own internal testing, that might be okay, but testing wireless networks for paying clients is likely a no-no with this type of license limitation.
This port-scanning information helps create an even more detailed picture of what’s available on your wireless network. No wonder hackers love it. This information gives them just what they need to try to exploit a ton of potential vulnerabilities on your systems. Table 3-1 outlines the ports that we often find open and vulnerable to attack, so be on special lookout for these.
Table 3-1
Commonly Hacked Wireless Network Ports
Port Numbers
Service
Protocols
20
FTP data (File Transfer Protocol)
TCP
21 FTP
control
TCP
22
SSH
TCP
23
Telnet
TCP
25
SMTP (Simple Mail Transfer Protocol)
TCP
53
DNS (Domain Name System)
UDP
80
HTTP (HyperText Transfer Protocol)
TCP
110
POP3 (Post Office Protocol version 3)
TCP
135
RPC/DCE end point mapper for
TCP, UDP
Microsoft networks
137, 138, 139
NetBIOS over TCP/IP
TCP, UDP
161
SNMP (Simple Network
TCP, UDP
Management Protocol)
443
HTTPS (HTTP over SSL)
TCP
512, 513, 514
Berkeley r commands (such as rsh,
TCP
rexec, and rlogin)
1433
Microsoft SQL Server
TCP, UDP
1434
Microsoft SQL Monitor
TCP, UDP
3389
Windows Terminal Server
TCP
08_597302_ch03.qxd 8/4/05 7:00 PM Page 39
Chapter 3: Implementing a Testing Methodology
39
Determining More about What’s Running
Performing port scans on your wireless network can snag a good amount of detail about how your system is set up and how it works — and knowledge is power. This power can be used to help you or used to harm you. But guess what? Once you know which ports are open, you (or somebody who isn’t you) can find out even more details about the configuration of your wireless systems. Again, we’re thinking like a hacker here — building a picture of what’s available to be hacked.
By connecting to the open ports on your live systems, you can obtain even more in-depth enumeration information, such as:
ߜ Acceptable usage policies and login warnings (or lack thereof) on banner pages
ߜ Software and firmware versions (returned via banners or error messages) ߜ Operating-system versions (returned via banners, errors, or unique protocol fingerprints)
ߜ Configurations of your operating system and applications If by connecting to open ports you end up discovering a ton of exploitable information about your APs, workstations, and servers, don’t panic. Many of your wireless systems may not be public-facing, so the likelihood of you having a lot of wireless devices with public IP addresses is low — at least it should be. However, you may have wireless hotspots or wireless-based servers that must be kept publicly accessible. These systems are usually reachable by an attacker — even through firewalls or other protective measures — and obtaining configuration information from them is not very difficult. This accessibility may entail some unavoidable vulnerability — a necessary evil if you want your network to do actual, useful work (what a concept).
Regardless, keep in mind that all this information can be used against you; eternal vigilance is the price of productivity. That leads us to performing an actual vulnerability assessment where you discover true vulnerabilities that can be exploited, which findings are false-positives, and which issues don’t really matter.
Performing a Vulnerability Assessment
Now that you’ve found potential “windows” into your wireless network, the next step is to see whether any bigger vulnerabilities exist. In essence, you connect to the wireless systems and make a discreet, methodical attempt to 08_597302_ch03.qxd 8/4/05 7:00 PM Page 40
40 Part I: Building the Foundation for Testing Wireless Networks see what can be found from a hacker’s point of view. You may be able to gather more information, capture data out of thin air with a sniffer, or determine that a specific patch is missing.
Remember not to discount what you’ve already found simply because you’re just now getting to the formal “vulnerability assessment” portion of the testing. Even without poking and prodding your wireless systems further, you may already have discovered some juicy vulnerabilities (such as default SSIDs, WEP not being enabled, and critical servers being accessible through the wireless network).
You can look for these vulnerabilities in two ways: manually and automatically. The next two sections discuss these two methods in greater detail.
Manual assessment
The first way — manual assessment — is the most time-consuming, but it’s essential. Manually assessing vulnerabilities can be difficult at first, but it does get easier with experience. We call this assessment manual, but it often involves various semiautomatic security tools that don’t just perform a run-of-the-mill robo-assessment but need your guiding hand now and then. Knowing how wireless networks and their associated operating systems and software work — knowing what’s right and what stands out as a potential problem —
can really help out your manual assessments. Be sure to check out Peter’s book Wireless Networks For Dummies (as well as the other Linux and Windows For Dummies titles from Wiley) to learn more about these systems. Chey Cobb’s book Network Security For Dummies is also a great resource to give you a handle on a wide variety of information-security concepts. Manual vulnerability-assessment techniques are a must — and we’ll outline various ways to do them in various chapters throughout this book.
Automatic assessment
The second way of looking for vulnerabilities is to use an automated tool such as the open source Nessus (www.nessus.org) or the commercial LANguard Network Security Scanner (www.gfi.com/lannetscan) or QualysGuard.
These tools can automate the vulnerability-assessment process by scanning live systems and determining whether vulnerabilities (actual or potential) exist. These tools take a lot of the legwork out of vulnerability assessment, giving you more time to spend catching up on e-mails or watching Seinfeld re-runs. We can’t imagine performing automated ethical-hacking tests without these tools.
08_597302_ch03.qxd 8/4/05 7:00 PM Page 41
Chapter 3: Implementing a Testing Methodology
41
There are many excellent wireless-hacking tools that you won’t have to spend a dime on. They work great for running specific tests — but when it comes time to take a broader look at vulnerabilities, these commercial tools prove their worth. When you’re delicately probing the operating systems and applications running on your wireless network, you definitely get what you pay for.
Finding more information
After you or your tools find suspected vulnerabilities, there are various wireless security vulnerability resources you can peruse to find out more information on the issues you find. A good place to start is your wireless vendor’s Web site. Look in the Support or Knowledgebase section of the Web site for known problems and available security patches. You can also peruse the following vulnerability databases for in-depth details on specific vulnerabilities, how they can be exploited, and possible fixes:
ߜ US-CERT Vulnerability Notes Database (www.kb.cert.org/vuls) ߜ NIST ICAT Metabase (http://icat.nist.gov/icat.cfm)
ߜ Common Vulnerabilities and Exposures (http://cve.mitre.org/cve) Another good way to get more information on specific security issues is to do a Google Web and groups search. Here you can often find other Web sites, message boards, and newsgroups where people have posted problems and (hey, let’s be optimistic) solutions about your particular issue.
Penetrating the System
After you map your network, see which systems are running what, and find specific vulnerabilities, there’s one more phase in your ethical-hacking methodology — if you choose to pursue it. This is the system-penetration phase: actually getting in. This is the true test of what systems and information can actually be compromised on your wireless network and the ultimate goal of malicious hackers.
Penetrating your wireless systems simply means acting as if you were completely unauthorized to access the resources on your wireless network —
and trying to get in anyway. Sure, you’ve already been able to connect to your network “as an outsider” thus far, but this is where you take it all the way —
by joining the wireless network, connecting to various systems, and doing things such as
08_597302_ch03.qxd 8/4/05 7:00 PM Page 42
42 Part I: Building the Foundation for Testing Wireless Networks ߜ Logging in to the network
ߜ Browsing the Internet
ߜ Sending and receiving e-mails
ߜ Changing AP configuration settings
ߜ Capturing network data using a sniffer such as ethereal (www.ethereal.
com) or AiroPeek
ߜ Mapping to network drives
ߜ Editing, copying, and deleting files — just be careful which ones!
The hackers are doing these things, so it may make sense to try them yourself so you can get a true view of what’s possible on your network.
If you choose to penetrate your systems, proceed with caution — and work slowly and carefully to minimize any disruptions you may create!
In Parts II and III of this book, we outline how you can perform the tests we’ve described in this ethical-hacking methodology so you can start putting these procedures to work for you!
09_597302_ch04.qxd 8/4/05 7:00 PM Page 43