Hacking Wireless Networks (2015)
Part I
Building the
Foundation for
Testing Wireless
Networks
Chapter 4
Amassing Your War Chest
In This Chapter
ᮣ Choosing your platform: PDAs versus laptops
ᮣ Choosing your software
ᮣ Using software emulators
ᮣ Choosing transceivers, antennae, and GPS
ᮣ Signal jamming
Acyberwar is being waged. Your perimeter is under siege. What makes the attack especially insidious is that you cannot see your enemy. This isn’t hand-to-hand combat. Your enemy could be 2 miles from your office and still access your network and data. Your access point is your first line of defense in this war. It behooves you, then, to prepare for battle.
One way to prepare for any war is to participate in war games. Real war games allow you to test your equipment, tactics, and operations. In this case, war games allow you to test your wireless networks under normal conditions.
Like the Reservist going off to war, you also must receive adequate training on the latest weapons and tactics. Although the rest of the book focuses on tactics, this chapter focuses on equipment. You need practice with the tools the crackers use for real.
You need some hardware and software, but you have choices about what type of hardware and software you use. This chapter serves as your armory.
If you favor the Windows platform, we have some tools for you. Should you favor Linux, you will find some tools as well. We don’t leave Apple enthusi-asts out; we have something for you, too.
09_597302_ch04.qxd 8/4/05 7:00 PM Page 44
44 Part I: Building the Foundation for Testing Wireless Networks Choosing Your Hardware
What’s your poison? Laptop or personal digital assistant? The two primary hardware platforms for wireless hacking are
ߜ Personal digital assistant (PDA) or personal electronic device (PED) ߜ Portable or laptop
Each platform has its pros and cons. First, a PDA is readily portable so you can easily carry it from place to place. However, you won’t find as many tools for the PDA as you will for other platforms — depending on the operating system you run on your handheld device. If you run the Zaurus operating system, for example, you have more choices for software than you do if you choose the Pocket PC operating system.
One thing is safe to say: You don’t want to run wireless-hacking tools on a desktop. You may want to store NetStumbler files on the desktop, but the desktop is not really portable. The key thing to think about when choosing your hardware is portability. When performing hacking tests, you must be able to walk around your office building or campus, so a desktop is probably not the best choice. However, we know of people who use mini-towers in their cars for wardriving (discussed later in this chapter), but we don’t recommend it!
The personal digital assistant
Because of its portability, a PDA is the perfect platform for wardriving — but not for tasks requiring processing power. You want to get a PDA that uses either the ARM, MIPS, or SH3 processor. We recommend the Hewlett-Packard iPAQ (ARM processor), the Hewlett-Packard Jornada (SH3 processor), or the Casio MIPS for wardriving. These are handy devices since someone was kind enough to develop network discovery software for these platforms.
ARM’s processor technology has been licensed by more than 100 parties, so you should easily find a solution you like. It’s so easy, in fact, that you would better spend your time choosing the right operating system for your needs. We tell you more about operating systems in the software section of this chapter.
The portable or laptop
PDAs are great, but, typically, ethical hackers use laptops. Laptops have dropped dramatically in price the last few years, so they have become more accessible. You don’t need a lot of processing power, but, to paraphrase Tim 09_597302_ch04.qxd 8/4/05 7:00 PM Page 45
Chapter 4: Amassing Your War Chest
45
Allen, more power is better. You can use almost any operating system, including Windows 98, although you will find you get better results when using a newer and supported operating system. In addition to the laptop, you need the following components to get maximum results from your ethical hacking: ߜ Hacking software
ߜ A wireless network interface card (NIC) that can be inserted into your laptop — preferably one with an external antenna jack
ߜ External antenna (directional or omnidirectional) with the proper pigtail cable to connect your external antenna to your wireless NIC
ߜ Portable global positioning system (GPS)
ߜ DC power cable or DC to AC power inverter to power your laptop from your car’s 12-volt DC cigarette lighter plug socket. These are widely available from RadioShack, Kmart, Staples, CompUSA, or Wal-Mart stores.
The next few sections discuss these components in greater detail.
Hacking Software
To do your job properly, you need a selection of freeware and commercial software. Fortunately, a glut of freeware programs is available, so you don’t need a champagne budget; a beer budget should suffice. In fact, if you are prepared to run more than one operating system, you can get by using only freeware tools. You need the following software to do all the hacking exercises in this book:
ߜ Partitioning or emulation software
ߜ Signal strength–testing software
ߜ Packet analyzer
ߜ Wardriving software
ߜ Password crackers
ߜ Packet injectors
Using software emulators
In a perfect world, all the tools available would work on the same operating system. But in the real world, that’s not the case. Many great tools operate on operating systems that are incompatible with each other. Very few of us, of course, are conversant with multiple operating systems. Also, few of us have 09_597302_ch04.qxd 8/4/05 7:00 PM Page 46
46 Part I: Building the Foundation for Testing Wireless Networks the money to support duplicate hardware and software. So, how can you use all these tools? You need to find a solution that allows you to run more than one operating system on the same machine.
To solve this problem, people often build dual-boot or multi-boot workstations.
You can use a product like Symantec’s PartitionMagic (www.symantec.com/
partitionmagic) to set up partitions for the various operating systems. For more information about setting up and using PartitionMagic, among other things, check out Kate Chase’s Norton All-in-One Desk Reference For Dummies(Wiley). After you set up your partitions, you install the operating systems on the various partitions.
When everything’s installed, you can select the operating system you want to use when you boot the system. Say you’re using NetStumbler on Windows XP
and you decide to use WEPcrack — which is available only on Linux — on the access points you just identified with NetStumbler. You shut down Windows XP, reboot your system, and select the Red Hat Linux operating system. When you want to use Windows XP again, you must do the reverse. This isn’t a bad solution, but flipping back and forth a lot eats up valuable time. And managing your partitions and trying to make the operating systems coexist on the same hardware can be challenging.
Enter software emulators. Software emulators allow you to emulate a guest operating system by running it on top of a host operating system. You can run Linux emulation on a Windows host, and vice versa. To emulate Windows or DOS on a Linux host, you can choose one of the following Windows-based emulators:
ߜ Bochs (http://bochs.sourceforge.net)
ߜ DOSEMU (www.dosemu.org)
ߜ Plex86 (http://savannah.nongnu.org/projects/plex86)
ߜ VMware (www.vmware.com)
ߜ WINE (www.winehq.com)
ߜ Win4Lin (www.netraverse.com)
Alternatively, you can emulate Linux on a Windows host. To do this, choose one of the following Linux-based emulators:
ߜ Cygwin (http://cygwin.com)
ߜ VMware (www.vmware.com)
09_597302_ch04.qxd 8/4/05 7:00 PM Page 47
Chapter 4: Amassing Your War Chest
47
Mac lovers can already run most of the UNIX tools under the Mac OS. To emulate the Windows environment, you can run an emulator like Microsoft Virtual PC (www.microsoft.com/mac/products/virtualpc/virtualpc.
aspx?pid=virtualpc).
To get you going, the next two sections discuss Cygwin and VMware, two excellent examples of emulation software.
Setting up Cygwin
Do you use Windows but have software that only runs on Linux? If so, Cygwin is your answer. Cygwin is a contraction of Cygnus + Windows. It provides a UNIX-like environment consisting of a Windows dynamically linked library (cygwin1.dll). Cygwin is a subsystem that runs on Windows and intercepts and translates UNIX commands. This is transparent to the user. With Cygwin, you can have the experience of running xterm and executing ls commands without ever leaving your safe Windows environment.
First, download Cygwin by going to http://cygwin.com. Installing Cygwin is easy when you follow these steps:
1. On the home page, click the Install or Update Now! (Using setup.exe) link about halfway down the page.
You see a File Download – Security Warning window.
2. Click Run to download Cygwin.
You see the message shown in Figure 4-1.
3. Click Run to run setup.exe.
You see the Cygwin Setup window shown in Figure 4-2.
Figure 4-1:
Security
warning.
4. Click Next.
09_597302_ch04.qxd 8/4/05 7:00 PM Page 48
48 Part I: Building the Foundation for Testing Wireless Networks Figure 4-2:
Cygwin
setup.
5. Select Install from Internet and click Next.
This is the installation type. If you have a CD-ROM with Cygwin, select Install from Local Directory instead.
The Choose Installation Directory dialog box appears, as shown in Figure 4-3.
Figure 4-3:
Choosing
the
installation
directory.
6. Choose the installation directory options based on your needs and setup and then click Next.
After installation, this is the Cygwin root directory. Leave the default or click Browse to select another location. You can decide whether to make Cygwin available to all users or just to you. In addition, you can decide whether you want DOS or UNIX file types.
09_597302_ch04.qxd 8/4/05 7:00 PM Page 49
Chapter 4: Amassing Your War Chest
49
The ^M character
Ever see a ^M character at the end of your text
binary format rather than ASCII. DOS file lines
files? Yes? Well, this likely means that someone
end with a newline and a carriage return while
transferred the file from UNIX to Windows using
UNIX file lines end with the newline only.
7. Select a location in which to store the installation files. Then click Next.
Unless you have a compelling reason for not doing it, use the default. If you must put the installation files somewhere else, click Browse and select the location.
8. Select the type of Internet connection you have. Click Next.
We suggest that when you aren’t sure what to select here, use the default. If you’re doing this from your home office, then Direct Connection should work. If you’re at work, you might have a proxy server. If you have a proxy server, it’s perhaps best to talk to your system administrator.
9. Select a download site from the scroll box. Click Next.
You may have to try a few download sites before you find one that works for you. Peter tried several times to find a site. Either it would not start the download and required him to select a new site or it got halfway through the download and quit. You must persevere. Cygwin is worth it.
The Select Packages window appears, as shown in Figure 4-4.
Figure 4-4:
Selecting
the pack-
ages to
install.
09_597302_ch04.qxd 8/4/05 7:00 PM Page 50
50 Part I: Building the Foundation for Testing Wireless Networks 10. Select the packages you want to install. Click Next.
If you want them all, click Default beside the word All under Category.
The word Default appears next to many categories. Clicking this word more than once produces a range of results: Click it once, and it changes to Install. Click again, and it’s Reinstall. Click it again, and it’s Uninstall.
Click one last time, and you are back at Default. We suggest you select Install. Installing everything takes up approximately 1 gigabyte. If you don’t have the available space, select only those categories you think you will need.
If you choose to install everything, it can take a long time. Obviously, how long depends on the bandwidth of your connection to the Internet.
It also depends on the speed of your processor. But trust us, when you install everything, it takes time, so prepare yourself for a long wait.
Should you choose not to install a package at this time, you can always do so at a later time. Rerun the setup.exe program and install those programs you now want.
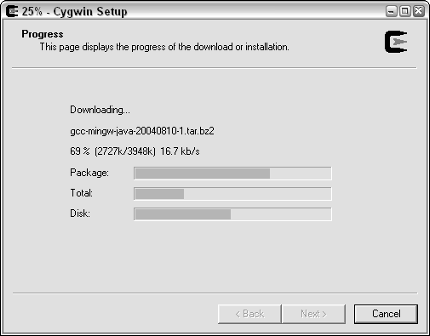
While Cygwin installs, the progress window shown in Figure 4-5 tracks your progress as it downloads the various components.
When the setup is complete, you see the window shown in Figure 4-6.
Figure 4-5:
Cygwin
down-
loading.
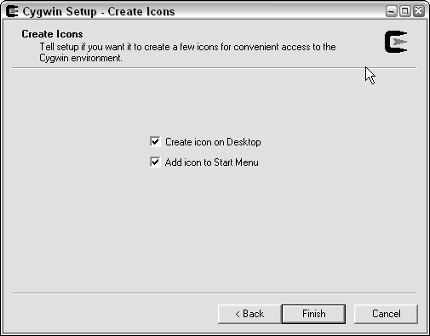
11. If you want to create desktop or Start menu icons, select (or deselect) the appropriate options. Click Finish.
That’s it. You are now the proud owner of Cygwin.
09_597302_ch04.qxd 8/4/05 7:00 PM Page 51
Chapter 4: Amassing Your War Chest
51
Figure 4-6:
Creating
desktop and
Start menu
icons.
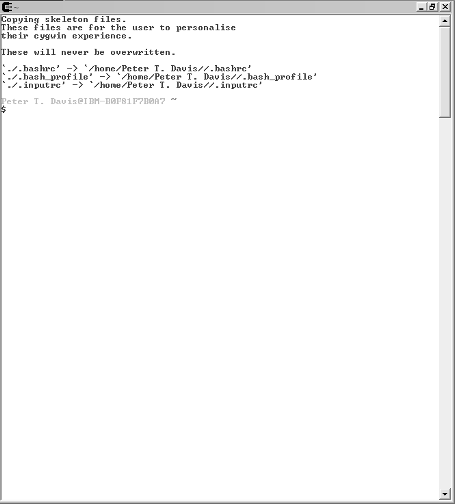
Go to your desktop and double-click the Cygwin icon. Cygwin starts, and you should see a window like the one shown in Figure 4-7.
Figure 4-7:
Cygwin
window.
09_597302_ch04.qxd 8/4/05 7:00 PM Page 52
52 Part I: Building the Foundation for Testing Wireless Networks Cygwin presents you with a command prompt. This is a bash shell. The Cygwin user is the same as the Windows user. If you want to see what Cygwin has mounted for you, in addition to the contents of the c:/cygwin directory you created, type df at the prompt. The c:/cygwin directory is the root directory.
You have the opportunity to try some of the UNIX tools in later chapters. But just to get started, type uname –a at the prompt. Try an ls -al command.
Ever cursed Windows because you couldn’t easily find out what processes are executing? Well, you just have to execute the ps –aWl command. (You might want to pipe (>) the output to a file.) If you’re not familiar with UNIX
commands, then you need to get a good UNIX book. Why not start with UNIX
For Dummies, 5th Edition, by John Levine and Margaret Levine Young (Wiley)?
Cygwin has a couple of drawbacks:
ߜ You have to use the UNIX version it gives you.
ߜ You cannot run other operating systems.
That’s a pretty short list considering that Cygwin is free (it is distributed under the GNU Public License). However, should you feel flush, you can move up to VMware.
Setting up VMware
VMware allows you to run simultaneous operating systems. The VM in VMware stands for virtual machine. You install a host operating system, such as Windows XP, and then install VMware Workstation on top of it. Then you install the guest operating system in VMware. The virtual machine is similar to your real machine: You can power it on and off, and it boots up just like the real thing. As a guest operating system, VMware allows you to install anything that runs on the Intel x86 architecture. This means you can install Solaris x86, Windows 2003 Server, Red Hat Linux, SUSE Linux, or any other operating system you choose. Still need to test Windows 98 programs? Use VMware. The only thing stopping you from running every operating system known to man is disk space and real memory.
You can download VMware from www.vmware.com. It takes up approximately 21MB.
Hover your cursor over the Products link at the top of the page and select the VMware Workstation link from the resulting drop-down list. If you click the red Buy Now button at the top, you go to the VMware Store, where you find out that VMware Workstation for Windows costs $189. After you use the software for a while, you’ll agree this is a good price. (You can get a 30-day trial if you are not convinced.)
After you download VMware, it installs like any Windows application. Just follow the installation wizard.
09_597302_ch04.qxd 8/4/05 7:00 PM Page 53
Chapter 4: Amassing Your War Chest
53
During the download process, you might see a warning message to disable AutoRun. VMware doesn’t like the CD-ROM AutoRun feature. (From a security standpoint, you shouldn’t either.) Agreeing with VMware and disabling AutoRun is a good idea.
When the installation is complete, you need to reboot your machine. Now you are ready to add some guests or virtual machines. Installing new machines is easy:
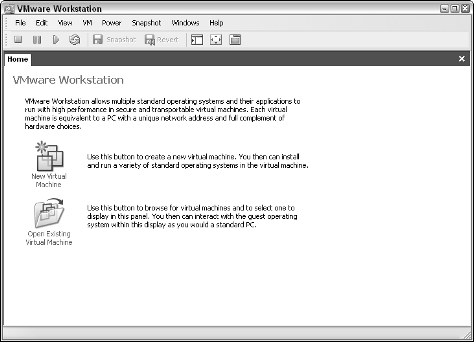
1. Start VMware.
You see a window like the one shown in Figure 4-8.
Figure 4-8:
VMware
Workstation
opening
window.
2. Click the New Virtual Machine icon.
This starts the process of creating your first virtual machine. The New Virtual Machine wizard appears.
3. Click Next.
4. Select Typical and click Next.
The Select a Guest Operating System window appears.
5. Select the OS you want to install.
You have a choice of the following:
• Microsoft Windows
• Linux
• Novell Netware
• Sun Solaris
• Other
09_597302_ch04.qxd 8/4/05 7:00 PM Page 54
54 Part I: Building the Foundation for Testing Wireless Networks If you select Other, you can install FreeBSD. Many good tools run on BSD.
If you select Linux, you can select a Linux version from the drop-down box.
6. Select the version you have and click Next.
7. Type a name for your guest in the Virtual Machine Name box. Then click Next.
You can create any name you want, so pick one that is meaningful to you. Also, decide where you want to store the image. Leave the default unless you have a compelling reason not to do so.
8. Select the Network Type. Click Next.
We suggest that you select Use Bridged Networking because it allows you to talk to your host operating system.
9. Specify Disk Capacity.
Virtual machines have virtual disks. You can pick any size you want as long as you have the available space. We recommend you leave the default of 4GB and leave the two other boxes deselected.
10. Click Finish.
However, you are not quite finished because you don’t have a system image.
You should see the window shown in Figure 4-9.
Figure 4-9:
Red Hat
Linux tab.
You now have a big choice. You can start the VM and install Red Hat Linux from a CD-ROM, or you can point to an ISO image. For this exercise, we’ll do the latter.
09_597302_ch04.qxd 8/4/05 7:00 PM Page 55
Chapter 4: Amassing Your War Chest
55
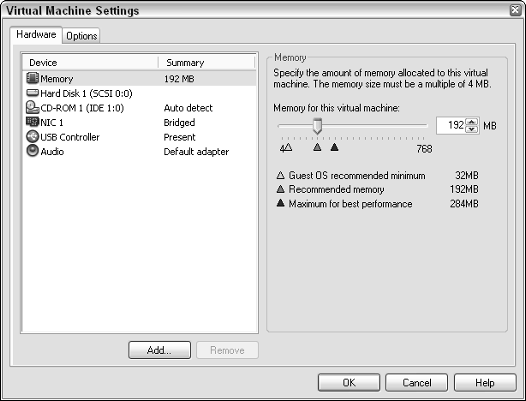
11. From the Commands panel, click Edit Virtual Machine Settings.
VMware presents the window shown in Figure 4-10.
12. Click CD-ROM.
If you want to install the operating system from a CD, then skip to Step 14.
Figure 4-10:
Virtual
Machine
settings.
13. From the right-hand pane, select Use ISO image.
14. Click the Browse button and find your ISO image. Click OK.
15. Click Start This Virtual Machine from the left-hand pane.
When you do this, you see a familiar display: The VM goes through the POST routine, does a memory check, and then boots itself.
Cygwin and VMware are wonderful tools, but you need to install them on your system; they won’t run any other way. If you don’t want to install software on your system, you can use products like Knoppix and WarLinux that boot from a diskette or a CD.
Linux distributions on CD
The following solutions are different from the partitioning and emulation solutions discussed above. What makes them different is that you don’t need to install them on your system: They boot and run completely from a CD.
Knoppix, for instance, runs from a CD based on the Linux 2.6. x kernel. It is a free and Open Source GNU/Linux distribution. You don’t need to install 09_597302_ch04.qxd 8/4/05 7:00 PM Page 56
56 Part I: Building the Foundation for Testing Wireless Networks anything on a hard disk; it’s not necessary. Knoppix has automatic hardware detection and support for many graphics cards, sound cards, SCSI and USB
devices, and other peripherals. It includes recent Linux software, the K Desktop Environment (KDE), and programs such as OpenOffice, Abiword, The Gimp (GNU Image Manipulation Program), the Konqueror browser, the Mozilla browser, the Apache Web server, PHP, MySQL database, and many more quality open-source programs. Knoppix offers more than 900 installed software packages with over 2,000 executable user programs, utilities, and games.
You can download Knoppix (it is approximately 700 MB) or you can buy it from a CD distributor. Knoppix is available for download from www.knoppix.
net/get.php. It’s also included on a DVD in Knoppix For Dummies by Paul Sery (Wiley).
Knoppix is not the only distribution of Linux that fits on a CD. Consider also using one of the following Linux CD distributions:
ߜ Cool Linux CD: http://sourceforge.net/project/showfiles.
php?group_id=55396&release_id=123430
ߜ DSL (Damn Small Linux): www.damnsmalllinux.org
ߜ GNU/Debian Linux: www.debian.org
ߜ SLAX: http://slax.linux-live.org
ߜ WarLinux: http://sourceforge.net/projects/warlinux
WarLinux is a special Linux distribution made for wardrivers. It is available on either a disk or bootable CD. The developer of WarLinux intended systems administrators to use it to audit and evaluate their wireless network installations.
Stumbling tools
In the methodology Kevin describes in his book, Hacking For Dummies (Wiley), and in the OSSTMM and ISSAF methods discussed in Chapter 2, the first step in ethical hacking is the same: reconnaissance. The best type of tool for reconnaissance is wardriving software. Programs like NetStumbler and Kismet help you find access points. Refer to Chapters 9 and 10 for more on the various stumbling tools.
You got the sniffers?
Stumbling tools help you find the access points, but that’s not enough. You need to peek into the transmitted frames. If the frames are unencrypted, of course, then this is an easy task. But when the frames are encrypted, you 09_597302_ch04.qxd 8/4/05 7:00 PM Page 57
Chapter 4: Amassing Your War Chest
57
The origin of the word sniffer
The term sniffer came from a product called
products had the same thing happen to them —
Sniffer that was manufactured and marketed by
Aspirin, Kleenex, and Zipper — and they’ll tell
a company named Data General. Unfortunately
you this is not a good thing.) Still, you might hear
for Data General, the name of their product these products referred to as network analyzers, has become the generic name for this type of
data analyzers, protocol analyzers, packet ana-
software. (Ask the various companies whose
lyzers, data line monitors, or network monitors.
need to decrypt the frame before you can look at it. This type of decryption software is generally called a sniffer.
Many freeware and commercial sniffer products are floating around out there.
Some run on Windows, and others run on Linux. Two of the more popular sniffers are Ethereal and AiroPeek, which we cover in Chapter 8.
Picking Your Transceiver
Wireless Networks For Dummies (Wiley) provides information on the various form factors for your clients. You have lots of options to choose from. Picking your wireless network interface card or transceiver depends on the operating system you choose. When NetStumbler and Kismet first came out, there were two chipsets for wireless NICs: Hermes and Prism2. As a general rule, if you decide to use NetStumbler, you want a card based on the Hermes chipset.
Kismet, on the other hand, works best with a Prism2 (Intersil) card. If you are prepared to do a kernel modification, then Hermes cards will work with Kismet.
Determining your chipset
Don’t know whether you have a Prism2 chipset or a Hermes chipset? The following PC Card manufacturers use the Prism2 chipset:
ߜ 3Com
ߜ Farallon
ߜ Addtron
ߜ GemTek
ߜ AiroNet
ߜ Intel
ߜ Bromax
ߜ LeArtery Solutions
ߜ Compaq WL100
ߜ Linksys
ߜ D-Link
ߜ Netgear
![]()
![]()
09_597302_ch04.qxd 8/4/05 7:00 PM Page 58
58 Part I: Building the Foundation for Testing Wireless Networks ߜ Nokia
ߜ SMC
ߜ Nortel
ߜ Symbol
ߜ Samsung
ߜ Z-Com
ߜ Senao
ߜ Zoom Technologies
ߜ Siemens
Further, if you have a Prism2 chipset, you may see a computer with antenna icon in the System Tray, as shown in Figure 4-11.
Prism2 icon
Figure 4-11:
Prism2 icon.
The following PC Card manufacturers use the Hermes (Lucent) chipset: ߜ 1stWave
ߜ Compaq WL110
ߜ Agere/ORiNOCO/
ߜ Dell
Proxim
ߜ ELSA
ߜ Alvarion
ߜ Enterasys
ߜ Apple
ߜ HP
ߜ ARtem
ߜ IBM
ߜ Avaya
ߜ SONY
ߜ Buffalo
ߜ Toshiba
ߜ Cabletron
Much like the Prism2 chipset, if you have a Hermes (Lucent) chipset, you will see an icon in the System Tray, as shown in Figure 4-12.
Hermes icon
Figure 4-12:
Hermes
icon.
To find information for your Hermes chipset, visit www.hpl.hp.com/personal/
Jean_Tourrilhes/Linux/Wireless.html and look for “orinoco.”
09_597302_ch04.qxd 8/4/05 7:00 PM Page 59
Chapter 4: Amassing Your War Chest
59
Buying a wireless NIC
When purchasing a wireless NIC, look for one that supports an external antenna. Figure 4-13 depicts an ORiNOCO card with an external antenna connector on the top. In this figure, the built-in antenna is the black plastic part on the end.
External antenna connector
Figure 4-13:
ORiNOCO
Gold Classic
card.
The ORiNOCO Gold Classic card from either Agere or Lucent is a popular card with wireless hackers because it has an external antenna connector and works with both Kismet and NetStumbler. Take care when buying new ORiNOCO cards. ORiNOCO is now owned by Proxim, which came out with an ORiNOCO card not based on the Hermes chipset. The Hermes card is still available, but it is usually sold as the ORiNOCO Gold Classic.
You can find a somewhat dated but useful comparison of the wireless cards and their chipsets at Seattle Wireless: www.seattlewireless.net/index.
cgi/HardwareComparison.
Extending Your Range
Antennae are generally optional, but if you want to test the boundary of your wireless signal, they are a must. Many companies that sell PC wireless NIC
cards also sell antennae. But many of these cards do not come equipped with a jack to plug in the antenna. Many people have resorted to modifying these PC cards to add jacks or soldering wires to the built-in antennas of their cards. Check out eBay for examples.
09_597302_ch04.qxd 8/4/05 7:00 PM Page 60
60 Part I: Building the Foundation for Testing Wireless Networks Other people are building antennas from everything from Pringles cans to PVC pipe. Peter has a tomato juice “cantenna” (see Figure 4-14). You can build your own or buy one starting at $39.95. Cantenna (www.cantenna.com) and Hugh Pepper (http://home.comcast.net/~hughpep) offer cantennae for sale. These are mainly directional designs, more commonly know as yagi-style antennas. They focus the 2.4 GHz wave, usually through a condenser (the can), to an element (a piece of copper) specifically placed in the antenna.
This is why they are also called wave guides. The depicted antenna provides 16 dBi gain.
Figure 4-14:
Wave guide
cantenna.
Directional antennae are good for aiming at buildings across the street or pointing to the top of a very tall building, but they are not really good for wardriving. For wardriving, you want to get yourself an omnidirectional antenna like the one shown in Figure 4-15. Peter bought this 5 dBi antenna, which has a magnetic base that can be attached to a car or cart, on eBay for $5.95(!). At that price, you should buy several and give them as gifts.
09_597302_ch04.qxd 8/4/05 7:00 PM Page 61
Chapter 4: Amassing Your War Chest
61
Directional vs. omnidirectional antennas
We have actually had a great deal of success
With an omni, the signal strength gets stronger
using directional antennas — as opposed to
only as you get closer, but you can never be
using omni antennas — for wardriving. If the
sure from which direction the signal is coming
directional antenna (or cantenna in this case) is
without actually traveling in several directions
aimed forward toward the front of the car, sig-
to track the signal strength. A directional
nals in front of you are often acquired much ear-
antenna provides direction as well as signal
lier than they are when using the omni antenna.
strength when trying to locate a specific target.
The cantenna can then be moved left or right,
An omni can show a larger number of signals at
peaking the signal and pointing out the exact
one time than a directional antenna, but with
origin or location of the wireless access point
lower signal strength than the directional
or errant signal being tracked.
antenna provides.
Figure 4-15:
Omni-
directional
antenna.
09_597302_ch04.qxd 8/4/05 7:00 PM Page 62
62 Part I: Building the Foundation for Testing Wireless Networks For more information on antennae, we encourage you to check out Wireless Networks For Dummies (Wiley). That book outlines in depth the different types of antennae. You’ll even find links for building your own wave guide antenna like that shown in Figure 4-16. That book provides information on RF
mathematics so you can interpret what dBi means.
Using GPS
While driving in an unfamiliar place, Peter’s family often asks, Where are we?
Until he got his global positioning system (GPS), he couldn’t always answer the question with great precision. As an answer, “somewhere between the Colorado border and El Paso” doesn’t cut it, especially when you get close to restricted government areas. Now, with GPS, he can tell you the exact latitude and longitude. That GPS device can help with your wireless hacking efforts as well.
Using your GPS system with your wardriving software can give you more information. Remember, the hacker’s primary law is more information is better. When you have to cover a large area in a short amount of time, the GPS is essential. Otherwise, you may not find the access point again.
To use GPS with wardriving software, you get the GPS unit to output GPS
coordinates to the computer’s serial port. When you find a wireless access point, Kismet and NetStumbler log the exact coordinates (down to a few feet) of the effective range.
Make sure you get a serial or USB cable to connect to your workstation when you buy your GPS device. If you are going to use the serial cable, ensure that you have a serial port; otherwise you’ll need a serial-to-USB adapter. The standard protocol for GPS is NMEA (National Marine Electronics Association), which dumps your coordinates every 2 seconds to a serial port via a special cable at 9600,8,N,1. If you use a Garmin GPS, you can use the Garmin format.
The Garmin eTrex Venture is nice for its size and cost (about $150). The Garmin reports every second, compared to every 2 seconds for the NMEA standard. However, Kismet supports only the NMEA format.
GPS units start at $100 and can run into the thousands. Peter purchased Microsoft Maps & Streets 2005 with GPS for about $129. The GPS (shown in Figure 4-16) labeled Microsoft is actually manufactured by Pharos, a well-known GPS vendor.
If you buy the Microsoft MapPoint software, you can take your output from NetStumbler and dump it right into StumbVerter (www.michiganwireless.
org/tools/Stumbverter), which plots it on a map for you. You can then take your output, massage it, and import it into your Maps & Streets GPS
device. We show you how to do this in Chapter 10. Table 4-1 lists some common mapping applications and their support for wardriving.
09_597302_ch04.qxd 8/4/05 7:00 PM Page 63
Chapter 4: Amassing Your War Chest
63
Figure 4-16:
USB GPS
device.
Table 4-1
Mapping Software
Developer and
GPS Interface
Import “Pushpins”?
NetStumbler
Software
Support?
Support
DeLorme Street
Yes
Yes
WiMap
Atlas USA
DeLorme Yes
Yes
PERL
script
TopoUSA
DeLorme Yes
Yes
PERL
script
XMap
Microsoft Yes
Yes
StumbVerter
MapPoint
Microsoft Yes
Yes
PERL
script
Streets
and Trips
Signal Jamming
You can buy a transmitter and jam a signal, but jamming happens accidentally as well. Real crackers may jam your signals to deny service to your legitimate clients. The following can affect your signal:
09_597302_ch04.qxd 8/4/05 7:00 PM Page 64
64 Part I: Building the Foundation for Testing Wireless Networks A brief history of jamming
Deliberate radio jamming goes back to the
betting person would lose. The first recorded
beginning of the last century. A betting person
instance of jamming occurred during the
would probably wager that radio jamming America’s Cup yacht races. Someone was trying was first done by the military somewhere. That
to get a competitive leg up, not a military edge.
ߜ Cordless phones can cause narrowband interference, which may mean you need to eliminate the source.
ߜ Bluetooth devices and microwave ovens can cause all-band interference, which may mean you need to change the technology or eliminate the source.
ߜ Lightning can charge the air, which may mean you need to ground and protect your equipment.
So, random interference can result in denial of service, but someone can do it intentionally as well by using one of two types of RF jamming devices: ߜ RF generators are rather expensive devices. You can get RF generators from companies like HP (www.hp.com) and Anritsu (www.anritsu.com).
ߜ Power signal generators (PSGs) are not as pricey. They are used to test antennae, cables, and connectors. You can get PSGs from YDI (www.ydi.com) and Tektronix (www.tek.com).
A variety of jammers are complete, standalone systems consisting of appropriate antennae, energy sources, and modulation electronics, such as techniques generators. But what causes interference is the effective radiated power (ERP). You can use the jammer to disrupt the operation of electromagnetic systems in either receiving or transmitting modes to reduce or deny the use of portions of the electromagnetic spectrum.
You may want to test your wireless network to discover how susceptible it is to signal jamming from outside your organization. If you plan to run mission-critical applications over wireless networks, then you need to know whether others can cause unplanned network outages.

10_597302_pt02.qxd 8/4/05 6:56 PM Page 65