Citrix XenMobile Mobile Device Management (2014)
Chapter 9. Deploying Policies
Policies are used to manage devices that are enrolled with the XenMobile Device Manager. By applying a policy, a XenMobile administrator can decide how enrolled devices will work once connected to the corporate network. In XenMobile, there are policies that manage which application needs to be installed and implement security policies on these devices. It also gives the option to deploy policies on individual groups as required. Once a policy has been implemented, the admin can push a package to the selected devices and track the deployment status to ensure a successful policy deployment.
Through XenMobile Policies, admins can enforce Passcode policies to lock devices after a certain period of inactivity to ensure the device is not misused. Sometimes users tend to uninstall the device agent, to prevent such activities; XenMobile can restrict users from uninstalling the XenMobile agent.
In this chapter, we will learn the following topics:
· XenMobile policies
· Passcode policy creation for iOS devices
· Device-jailbroken-detection policy
· Application access policy
XenMobile™ policies
A policy controls how an enrolled device functions, for example, locking a device to a specific Wi-Fi connection or pushing e-mail configurations and deciding the level of access to be allotted to the owner of the device. Policies can manage e-mail, Wi-Fi, GPRS, certificates, and other configurations on end-user devices.
Tip
MDM clients can only leverage features available on a device but cannot add any new feature on a device.
XenMobile has distributed policies into the following two major categories on its Device Manager console:
· MDM Policies: They control device-based configurations (e-mail, VPN, encryption, and so on) depending on individual device platforms (iOS, Android, Symbian, Windows, and others). In addition to this, MDM Policies also manage tunnels, which can be used to secure applications and their contents residing on the device. A remote support tunnel can be created to enable Remote Support services for end-user devices.
· App Policies: They manage the content residing on the enrolled devices and provide application access policies to blacklist-/whitelist-specific apps on devices, depending on their respective platforms.
Creating the passcode policy
Passcode policies, also known as Password policies, when deployed on devices, ensure that the end user enters the specific password in order to unlock the device. We need to perform the following steps to deploy a passcode policy on an iOS device:
1. Log on to the XenMobile Device Manager console.
2. Navigate to Policies and click on iOS.
3. Select Configurations and in the right pane click on New Configurations; now select Passcode.
4. Under the General tab, specify the Identifier (the profile name for the policy).
5. Enter a desired Display Name for the policy, for example, Passcode Policy.
6. Click on the Policy tab and select Require a code on the device.
7. Now, check the box besides Allow simple values. This allows the user to enter a simple passcode, which may consist of only alphabetic characters or numbers.
8. Select the value for Minimum length of codes. For simplicity, we will keep it to 4 and click on Create.
Once this policy is deployed, the user will be prompted to choose a password to set the passcode policy.
The device-jailbroken detection policy
There can be instances where a user brings in a device that is jailbroken or rooted (a software/hardware-exploited device with root access). These devices can be a security risk; hence, blocking these devices is a must. In this section, we will create a policy to detect such devices:
1. Navigate to the Policies tab and select Global.
2. Click on Automated Actions and then on New.
3. Enter a Name for the policy, for example, Jailbreak Policy.
4. Select Event as the Trigger Type.
5. In Event, select Device jailbroken.
6. Select Notify as the Action, or as desired.
7. Choose the Jailbroken Device template and click on Create.
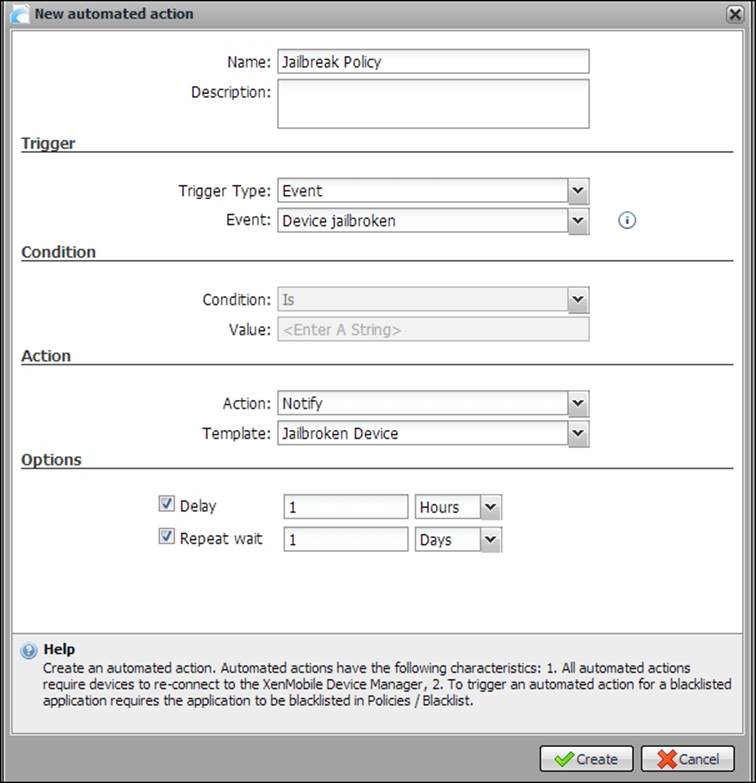
Once we deploy this policy, any jailbroken device that connects to the XenMobile Device Manager server will be notified to the Admin and the user for further actions. We can also choose other actions for this policy, which may be a selective wipe or a complete wipe.
The Application Access Policy
1. Application Access Policy determines how an app installed on an end user device will be treated when enrolled with the XenMobile Device Manager server. A policy can be used to suggest, mandate, or forbid an app on enrolled devices. In this section, we will create a policy to restrict the usage of the Facebook app on end-user devices. To do so, perform the following steps:
2. Navigate to Policies | App Policies.
3. Select Global and click on Application Access Policies.
4. Click on New Application Access Policy.
5. Enter a Name for the policy, for example, Facebook Restriction Policy.
6. Select the Access Policy as Forbidden.
7. Choose the OS type as Android and click on New app.
8. Under App Name, enter the name of the app, for example, Facebook and click on Create.
Tip
We can also enter the App Package Name for the application, which is the bundle identifier for the application. This will provide greater accuracy, for example, com.facebook.katana, for Facebook. Try using the application ApkSpy on PCs to get the Bundle Identifiers for apks.
9. Click on Create on the policy window.
Once the policy has been deployed, it will restrict enrolled devices from accessing the desired app such as Facebook, or the desired app on the enrolled devices as shown in our example.
Summary
In this chapter, we have covered a few common policies available in the XenMobile Device Manager. We have learned how to create a passcode policy and the identified jailbroken or rooted device section. We have also covered how to restrict unsecure applications from being accessed on an enrolled device.
In the next chapter, we will learn how to troubleshoot issues while installing and managing the XenMobile components, and managing enrolled mobile devices.
All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.