Citrix XenMobile Mobile Device Management (2014)
Chapter 2. XenMobile Solution Deployment Prerequisites
To ensure the successful deployment of a XenMobile Solution, the system requirements and prerequisites should be met. This chapter will prepare you to configure the preinstallation tasks for the XenMobile Solution. We will also identify the settings, certificates, ports, hardware, and so on, required to build a complete XenMobile Solution. All settings and configurations in this chapter will be done with an assumption of catering to 100 user devices or connections. In this chapter, we will be covering the following topics:
· Network settings
· Licensing
· Certificates
· Ports
· Active Directory settings
· Database requirements
· Server (hardware/hypervisor) sizing requirements
Network settings
All existing as well as post-deployment network settings should be identified in order to properly configure the XenMobile components in your infrastructure. You must gather the following settings before starting the implementation.
· Internal Fully Qualified Domain Name (FQDN)
· Public and private IP address (for existing AD and Exchange servers)
· Subnet mask
· Default gateway
· DNS settings
· Reserve NetScaler Gateway IP addresses
· Reserve App Controller IP address
· Reserve XenMobile DM server IP address
· NTP server IP address
Licensing
You must ensure all licenses are available before proceeding with the installation of XenMobile components. Both XenMobile MDM Edition and NetScaler Gateway require individual licenses to function. After buying the XenMobile Solutions Bundle, you can obtain your licenses by logging on to the Citrix portal.
Further detailed instructions on Licensing can be found at http://www.citrix.com/products/xenmobile/how-it-works/licensing.html.
Tip
The backup of the configuration files contains all uploaded licenses. If you reinstall XenMobile DM or NetScaler Gateway and do not have a configuration backup, you will need the original license files to complete the installation.
Certificates
The certificates ensure that the connection made between two entities is secure and authenticated depending on the environment (for example, LDAP authentication for Microsoft Active Directory services).
When a user device tries to create a secure connection using a web browser, the server sends its certificate to the device. The browser on the device then checks for Certificate Authority (CA) of the device and whether the CA is trusted by the device. In the case that the CA is trusted, the user is granted access to the service. Otherwise, the browser notifies the user that the CA is not trusted with an option to either accept or decline the certificate.
Tip
The wildcard or SAN certificates are supported by XenMobile. Most deployments require only two (external and internal) certificates.
The XenMobile components require certain specific certificates to function properly. A better understanding of the following certificates and their functioning will help you to manage and troubleshoot XenMobile components effectively:
· Server Certificate: The identity of a server (for example, NetScaler Gateway/App Controller/XenMobile DM) is certified by a server certificate.
· Root Certificate: The root certificate identifies and verifies the CA that signed the server certificates.
Apple Push Notification Service certificates
The Apple Push Notification Service (APNS) is a mobile notification service created by Apple. APNS uses push technology through an accredited and encrypted IP connection to forward notifications over persistent connections from application servers such as XenMobile to iOS devices such as the iPhone, iPad, and iPod Touch. An APNS certificate is a provisioned security certificate obtained through Apple Push Certificates Portal, which can be found at https://identity.apple.com/pushcert/. The APNS certificate can be obtained by enrolling for an Apple ID, which will allow you to upload certificates and further download Apple-signed APNS certificates.
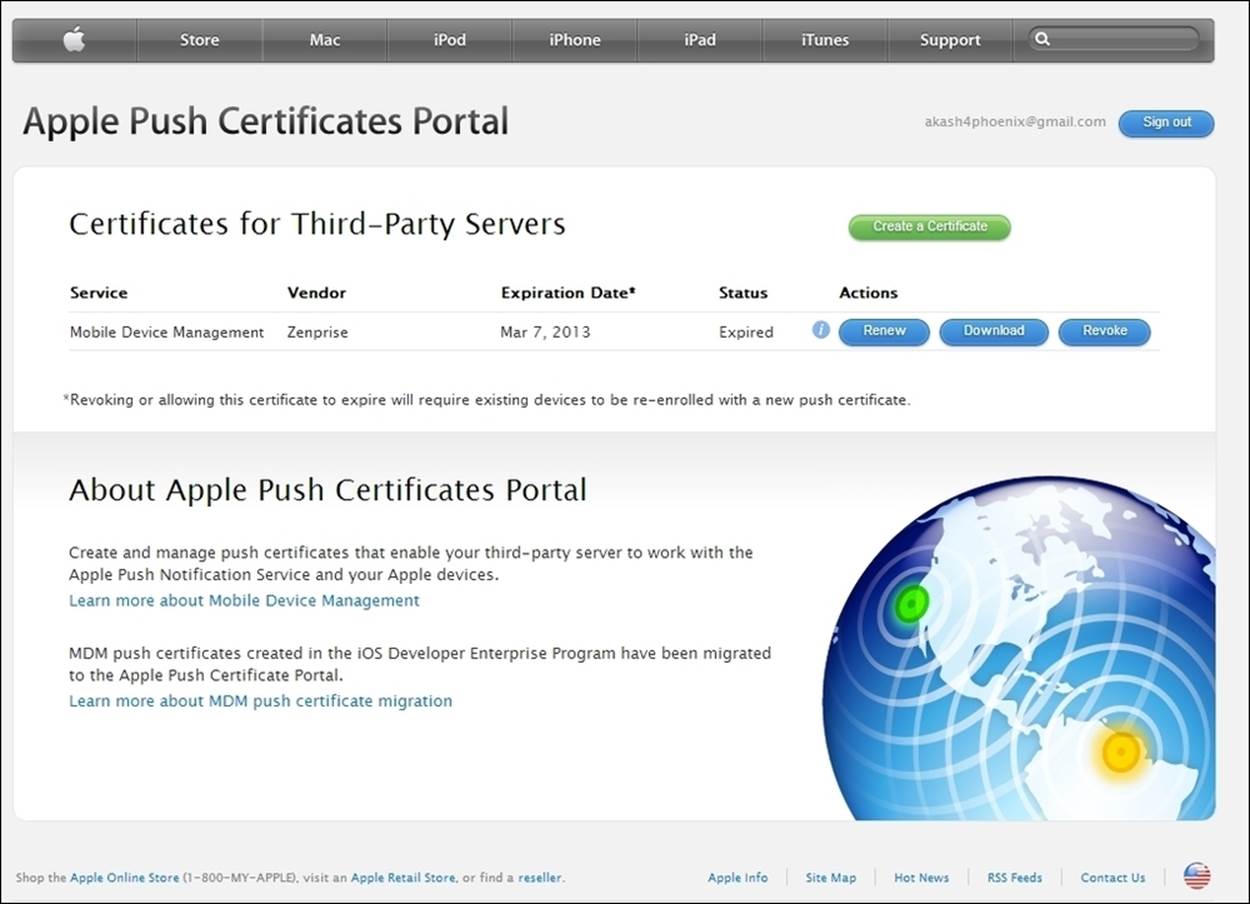
Security Assertion Markup Language certificates
The Security Assertion Markup Language (SAML) services integrate with XenMobile components and identity providers, enabling authentication capabilities that are not dependant on Active Directory services.
The following table shows the certificate format and type supported by each XenMobile component:
|
Component |
Certificate format |
Certificate type required |
Location |
|
NetScaler® Gateway |
PEM (BASE64) |
· Server · root |
External |
|
App Controller |
PEM or PFX (PKCS#12) |
· Server · SAML · root |
Internal |
|
StoreFront |
PFX (PKCS#12) |
· Server · root |
Internal |
|
XenMobile™ DM |
P12 format (PKCS#12) |
· APNS · Server |
External |
Opening ports
Ports act as communication endpoints, allowing applications to successfully communicate with the XenMobile components. You must ensure the relevant ports are opened on your firewall. The following table defines the ports that you need to open.
|
Port |
Description |
|
21 |
FTP services. |
|
25 |
SMTP services. |
|
53 |
DNS. |
|
80 |
HTTP requests. |
|
443 |
HTTPS requests. |
|
123 |
Network Time Protocol (NTP) services. |
|
389/636/3268 |
LDAP requests. |
|
1433 |
SQL server database requests. |
|
1494 |
Provides a connection between Windows-based applications in the internal network by using the ICA protocol. Citrix recommends keeping this port open. |
|
1812 |
RADIUS connection. |
|
2598 |
Provides a connection between Windows-based applications in the internal network by using session reliability. Citrix recommends keeping this port open. |
|
2195 |
Outbound APNS requests to gateway.push.apple.com for iOS Notifications and Policy deployment. |
|
2196 |
Outbound APNS requests to feedback.push.apple.com for iOS notifications and policy deployment. |
|
5223 |
Outbound APNS requests from iOS devices on Wi-Fi networks. |
|
9080 |
HTTP requests from NetScaler to XNC. |
|
9443 |
HTTPS requests from NetScaler to XNC. |
|
8443 |
iOS device's enrollment requests. |
Active Directory settings
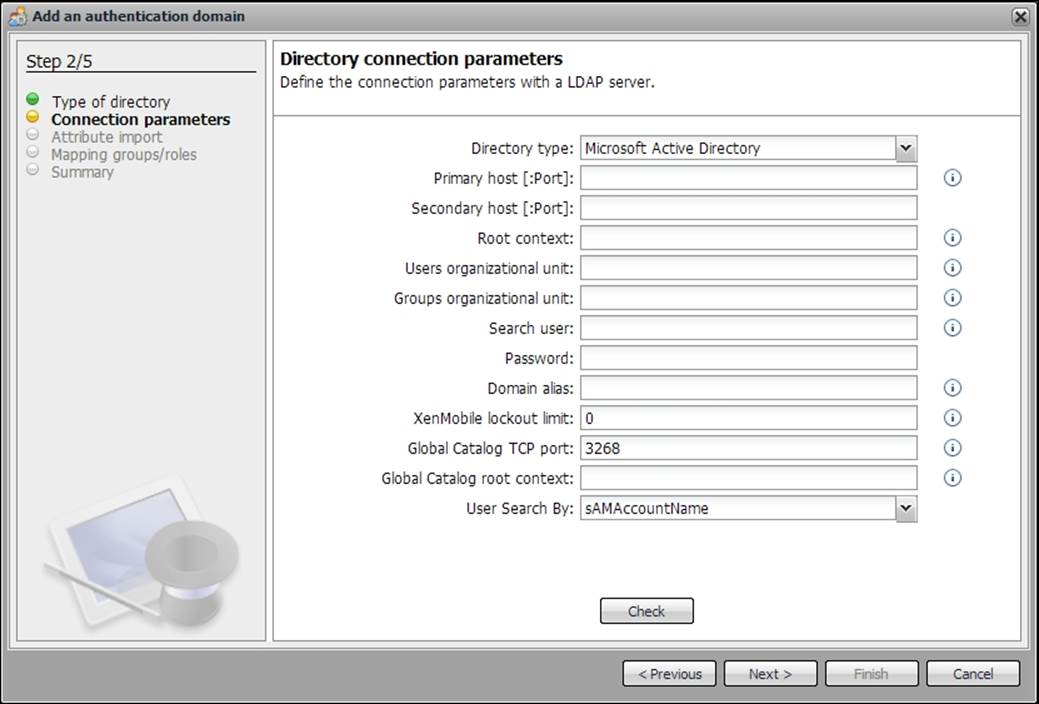
XenMobile components, when integrated with Active Directory, allow access to users, groups, and other objects existing in the infrastructure. Ensure that you gather the following Active Directory settings before installing the XenMobile components:
· Primary DNS server IP address
· LDAP ports
· Root context (for example, DC=TEAMXCHANGE ,DC=IN)
· Domain alias
· LDAP user ID and password
Tip
It's always recommended to have a separate user created in Active Directory for LDAP usage.
The following screenshot consists of the Active Directory settings:
Database requirements
The XenMobile DM installer contains the PostgreSQL (Postgres) database server bundles within it. XenMobile also supports Microsoft SQL server. Citrix suggests using Postgres only for test deployments. XenMobile supports the following databases to manage its repository:
· Microsoft SQL Server 2005
· Microsoft SQL Server 2008
· Microsoft SQL Server 2008 R2
· Microsoft SQL Server 2012
The service account should have Administrator rights and Creator, Owner, and Read/Write permissions.
Tip
Refer to Microsoft SQL Server Documentation for System Requirements and prerequisites
Server sizing requirements for hardware/hypervisor
Each XenMobile component has dependencies on the type of hardware or hypervisor required to set up. The sizing of XenMobile components depends on the number and type of devices to be enrolled on the Device Manager server. The following configuration will help you decide on the sizing aspects of the XenMobile components for 100 devices.
Citrix® NetScaler® Gateway
The NetScaler Gateway is available in the following three models depending on the deployment scenario chosen:
· NetScaler SDX: It's a hardware platform on which virtual instances of NetScaler or NetScaler Gateway can be installed and can handle up to 60,000 user connections
· NetScaler MPX: It's a physical appliance capable of handling up to 7,000 user connections
· NetScaler VPX: It's a virtual instance of the NetScaler Gateway that can be installed on a Windows Hyper-V or VMware ESX server and is capable of handling up to 870 user connections as recommended by Citrix
In this book, we will be deploying the NetScaler VPX solution for managing user devices.
XenMobile™ Device Manager
The Device Manager server is Windows-based and its system requirements are as follows:
· Windows server requirements:
· Microsoft Windows Server 2012 64-bit Standard or Enterprise Edition
· Microsoft Windows Server 2008 R2 Standard or Enterprise Edition
· Java requirements:
· Oracle Java SE 7 JDK (JDK Download Edition) with Version 11 and above
· Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 7
· Hardware requirements:
· Physical or Virtual Host Machine
· Intel Xeon 3 Ghz or AMD Opteron-1.8 Ghz server class
· 4 GB RAM minimum
· 500 MB minimum disk space
· 2 Core or 2v CPU
App Controller
The App Controller virtual instance can be installed either on XenServer 5.6 SP1 or above, Microsoft Hyper-V 2012, or VMware ESXi 4.0 or above. The App Controller server virtual machine requires the following minimum system configurations:
· Memory: 4 GB
· Virtual CPU: 2 VCPUs
· Disk Space: 50 GB
· Virtual Network Interface: 1
Summary
As discussed in this chapter, we have identified the mandatory system requirements and prerequisites that need to be met before the deployment phase of the XenMobile components. In the next chapter, we will get started with installation of the NetScaler VPX Solution and its configuration.
All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.