CCNA Wireless 200-355 Official Cert Guide (2016)
Chapter 16. Implementing a Wireless Guest Network
This chapter covers the following topics:
![]() Guest Network Overview—This section describes a guest wireless network and how it can be used to segregate guests from other users on a network.
Guest Network Overview—This section describes a guest wireless network and how it can be used to segregate guests from other users on a network.
![]() Configuring a Guest Network—This section covers the process needed to implement a guest wireless LAN.
Configuring a Guest Network—This section covers the process needed to implement a guest wireless LAN.
This chapter covers the following exam topics:
![]() 5.0—Configuration of Client Connectivity
5.0—Configuration of Client Connectivity
![]() 5.1—Identify authentication mechanisms
5.1—Identify authentication mechanisms
![]() 5.1a—LDAP, RADIUS, local authentication, WebAuth, 802.1X, PSK
5.1a—LDAP, RADIUS, local authentication, WebAuth, 802.1X, PSK
![]() 5.2—Configuring WLAN authentication mechanisms on the controller
5.2—Configuring WLAN authentication mechanisms on the controller
![]() 5.2a—WebAuth, 802.1X, PSK
5.2a—WebAuth, 802.1X, PSK
![]() 5.5—Describe wireless guest networking
5.5—Describe wireless guest networking
![]() 5.5a—Anchor controller
5.5a—Anchor controller
![]() 5.5b—Foreign controller
5.5b—Foreign controller
In Chapter 15, “Configuring a WLAN,” you learned how to define and configure a new wireless LAN to support a community of clients that have something in common. You can even configure multiple WLANs to support multiple user communities. In most cases, the WLAN users are trusted at some level because they are a necessary part of your enterprise.
What about guest users, who might not be trusted or integral to your business? Guest users commonly need to access the wireless network as a convenience. This chapter discusses the steps you can take to configure a guest network as an extension to your wireless infrastructure.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz allows you to assess whether you should read this entire chapter thoroughly or jump to the “Exam Preparation Tasks” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 16-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes.”

Table 16-1 “Do I Know This Already?” Section-to-Question Mapping
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. Which one of the following should be used to contain visitors and transient users of a wireless network?
a. WPA2 enterprise
b. Guest WLAN
c. One-time WEP
d. Broadcast SSID
2. Suppose a data WLAN and a guest WLAN are configured on a controller and mapped to two VLANs. Which one of the following is a true statement?
a. The controller can route traffic between the two WLANs.
b. The controller will bridge traffic between the two WLANs.
c. The controller cannot route packets between the two WLANs.
d. The controller can route packets between the two WLANs, but not the two VLANs.
3. To create a guest WLAN, which one of the following must be configured on a wireless controller?
a. A private WLAN
b. A guest mobility group
c. A guest BSS
d. A regular WLAN
4. Which one of the following correctly finishes this sentence? By default, all guest WLANs defined on controllers in an enterprise...
a. are merged into one VLAN and subnet.
b. are connected by CAPWAP tunnels.
c. must be assigned the same WLAN ID number.
d. are isolated from each other.
5. Which one of the following is necessary to merge guest WLANs from multiple controllers onto a common guest WLAN on a controller?
a. RF group
b. Global WLAN
c. Mobility anchor
d. Master controller
e. Prime Infrastructure templates
6. In a wireless guest network, which one of the following statements is correct?
a. A client associates with a guest mobility anchor controller and is tunneled to a guest foreign controller.
b. A client associates with a guest foreign controller and is tunneled to a guest mobility anchor controller.
c. A client associates with a guest mobility anchor and then must reassociate with a guest foreign controller.
d. A client associates with a guest foreign controller and then must reassociate with a guest mobility anchor controller.
7. Which of the following pairs of phrases makes this sentence correct? You can configure _____________ as a ______________ for a guest WLAN.
a. only one controller, mobility anchor
b. multiple controllers, mobility anchor
c. a mobility anchor, foreign controller
d. a foreign controller, mobility anchor
Foundation Topics
Guest Network Overview
Wireless LANs are usually configured to support specific groups of clients or client devices. For example, one WLAN might support wireless users in the Engineering department, even if that department is scattered in several buildings or locations. Other WLANs might support a sales staff, teachers, students, and so on. These examples segment wireless users by function or the need to access certain enterprise resources. Each WLAN might have a different set of security policies from the others.
You might also decide to create WLANs to support different types of wireless devices. For example, one WLAN could be configured to support all medical devices in a hospital that can use only Wi-Fi Protected Access Version 2 (WPA2) with a pre-shared key (PSK). A separate WLAN could be created for users with medical devices that support WPA2 Enterprise, with digital certificates. In these cases, WLANs are created according to the wireless device capabilities.
As a wireless network administrator, you might be asked to provide connectivity for users who do not fall into any convenient category. Guest users are normally temporary visitors who need to access a wireless network to make their work and their time onsite more convenient. Because guests are not regular, trusted employees, you should always try to offer some basic network access while containing and isolating them from the trusted portion of your network.
In Figure 16-1, both guests and engineering staff are able to use the same wireless infrastructure, while the two user groups are kept isolated from each other. The engineering users can communicate directly with the company resources. However, the guest users are commonly placed within a demilitarized zone (DMZ) that has limited access and is secured by a firewall.
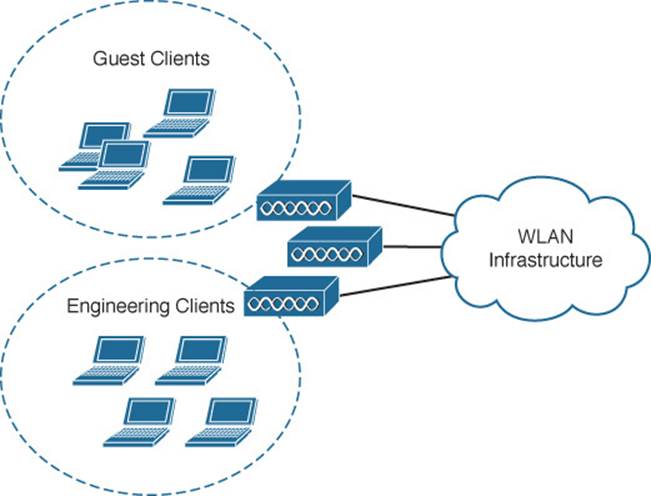
Figure 16-1 Isolating Guest Wireless Users from Other User Groups
Building a guest wireless network might seem like a complex task; however, it is really no different from building any other WLAN that is tailored for a user community. The trick is to provide the appropriate degree of isolation from the rest of the enterprise network.
The guest WLAN can be bound to a guest VLAN that is isolated from other VLANs, as shown in Figure 16-2. Before guest users can access the guest WLAN, they should be authenticated somehow. In addition, before they can access resources on any other WLAN or VLAN, a router or firewall should permit and provide the access.
![]()
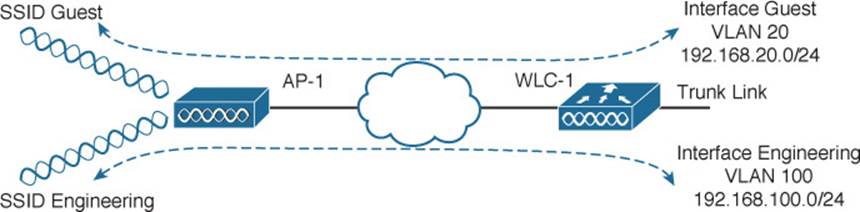
Figure 16-2 Isolation Between a Guest and Other WLANs
In Figure 16-2, the Guest WLAN advertises service set identifier (SSID) Guest and is bound to the controller’s Guest interface on VLAN 20. The same access point (AP) and controller infrastructure has an Engineering WLAN that is bound to the controller’s Engineering interface on VLAN 100.
Because all web browsers on all platforms use HTTP and HTTPS, the web browser is a universal interface for users to be authenticated before granting them wireless access. Cisco wireless LAN controllers (WLCs) support web authentication for this purpose. Users are presented with a web authentication splash page that includes a challenge for credentials.
Web authentication can be handled locally on the WLC for smaller environments through local web authentication (LWA). You can configure LWA in the following modes:
![]() LWA with an internal database on the WLC
LWA with an internal database on the WLC
![]() LWA with an external database on a RADIUS or LDAP server
LWA with an external database on a RADIUS or LDAP server
![]() LWA with an external redirect after authentication
LWA with an external redirect after authentication
![]() LWA with an external splash page redirect, using an internal database on the WLC
LWA with an external splash page redirect, using an internal database on the WLC
When there are many controllers providing web authentication, it makes sense to use LWA with an external database on a RADIUS server, keeping the user database centralized. The next logical progression is to move the web authentication page onto the central server too. This is calledcentral web authentication (CWA).
Scaling the Guest Network
Building a guest WLAN on a single controller is straightforward. The guest WLAN is just like any other WLAN defined on the controller. In larger installations, you might have more than one controller. In that case, each guest WLAN terminates on its own controller, making it difficult to isolate all guest clients in a single DMZ or behind a single firewall.
Recall from Chapter 12, “Understanding Roaming,” that Cisco WLCs can support Layer 3 roaming by automatically building a tunnel between the first controller a client associates with and the controller where the client is currently located. In effect, the client is tunneled from a foreign controller back to the original anchor controller. This same tunneling strategy can be leveraged to funnel guest clients from any controller into a mobility anchor controller where guests share a common IP subnet and security policies.
Where Layer 3 roaming builds controller-to-controller tunnels to follow clients as they move, mobility anchors are configured ahead of time so that guest clients will be tunneled to one or more predetermined anchor controllers. Figure 16-3 illustrates the concept with three WLCs. Each WLC is configured with its own guest WLAN, but only WLC-1 is identified as a mobility anchor. The other two, WLC-2 and WLC-3, become foreign controllers that point to WLC-1 as their mobility anchor controller. Regardless of which controller a guest user joins, the user will be tunneled to the anchor and connected into the guest VLAN. You can also identify several mobility anchors so that guest users can be distributed across them to balance the load.
![]()
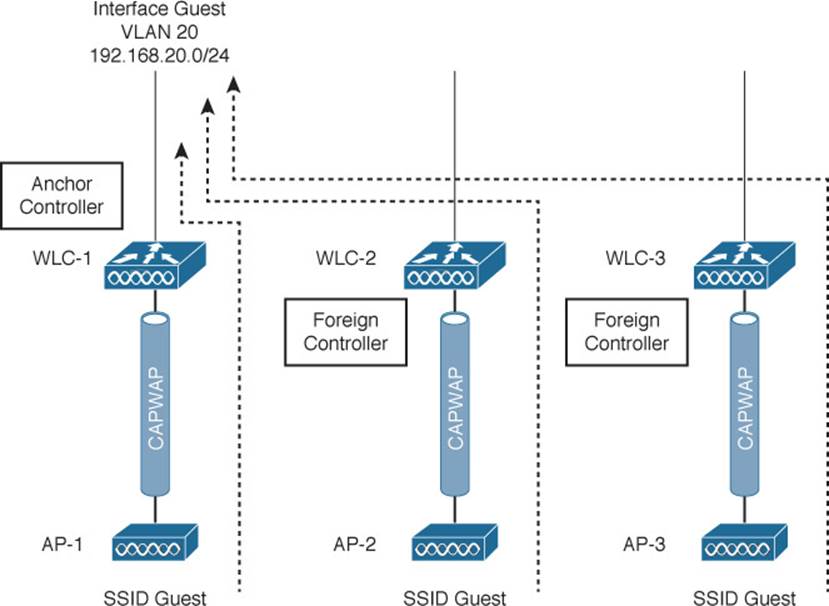
Figure 16-3 Using Mobility Anchors to Consolidate Guest Wireless Clients
Tip
In many implementations, the controller used as a mobility anchor for a guest network does not even have any APs joined to it. Instead, it acts as the final destination for the guest WLANs across an entire enterprise network. Without APs to support, the anchor controller can devote more resources toward handling guest users.
Configuring a Guest Network
You can use the following steps to configure a guest network. As you work through the steps, notice that the guest network requires a dynamic interface, a WLAN, and an authentication method—much like any other WLAN.
Step 1. Create a dynamic interface for the guest WLAN. Under Controller > Interfaces > New, define the dynamic interface, the VLAN ID, and the IP addressing information. Figures 16-4 and 16-5 show an interface named Guest configured for VLAN 20 and the 192.168.20.0/24 subnet.
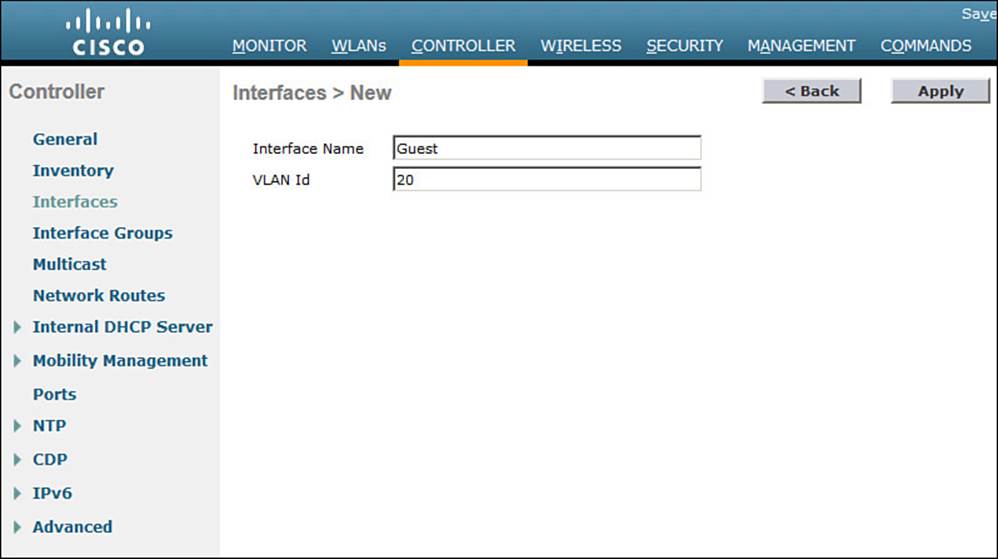
Figure 16-4 Creating a Controller Interface for a Guest WLAN
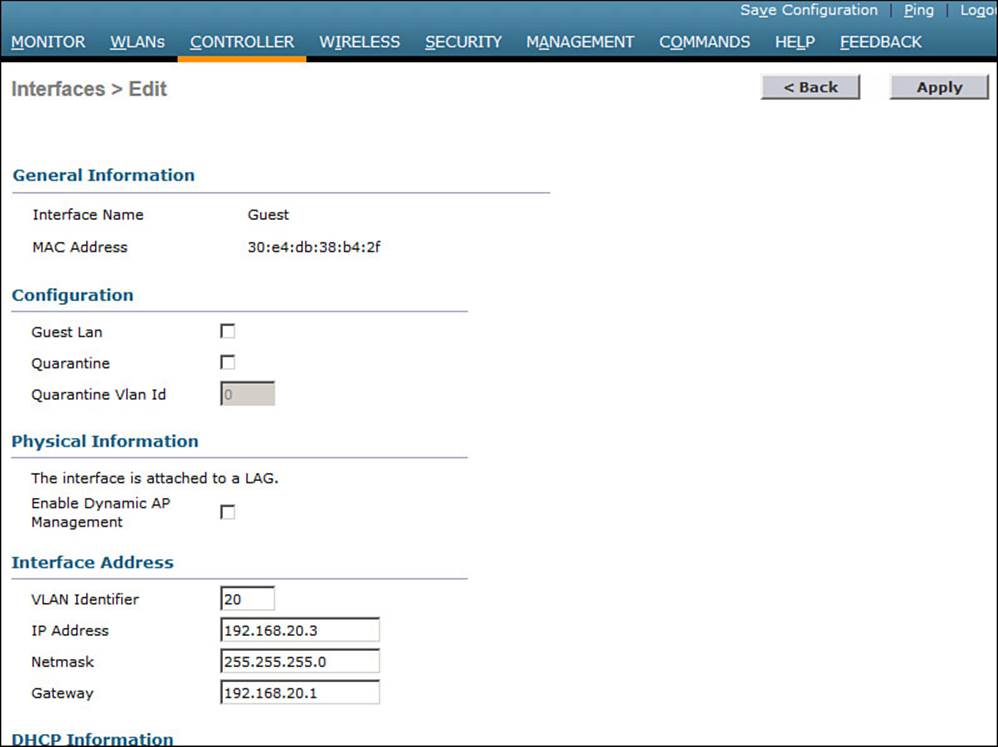
Figure 16-5 Configuring IP Address Information on the Guest Interface
Step 2. Create the guest WLAN.
Select WLAN > New to define a new WLAN, and then enter the profile name and SSID. In Figure 16-6, the controller has been configured with a second WLAN (ID 2) that uses SSID Guest.
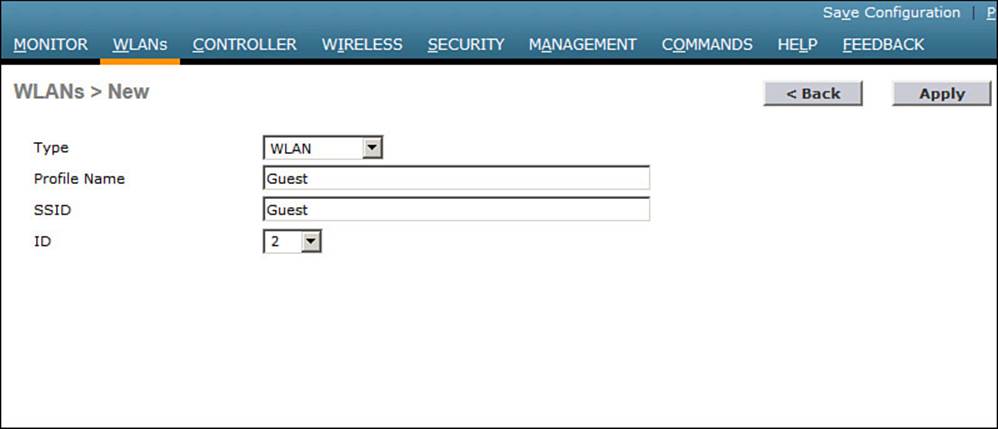
Figure 16-6 Creating a Guest WLAN
Step 3. Bind the guest WLAN to the guest WLAN interface.
On the General tab of the WLAN, select the guest controller interface to be used. In Figure 16-7, the Guest WLAN is configured to use the Guest dynamic interface. The dynamic interface does not matter on the foreign controller, as traffic is sent to the anchor and its dynamic interface. If PSK authentication is used, only the foreign controller needs the PSK configuration. If external RADIUS authentication is used, only the anchor controller needs the RADIUS configuration. All other WLAN parameters must be identical on the anchor and foreign controllers; otherwise, the two controllers will conclude that their WLANs are different and so no tunneling should occur.
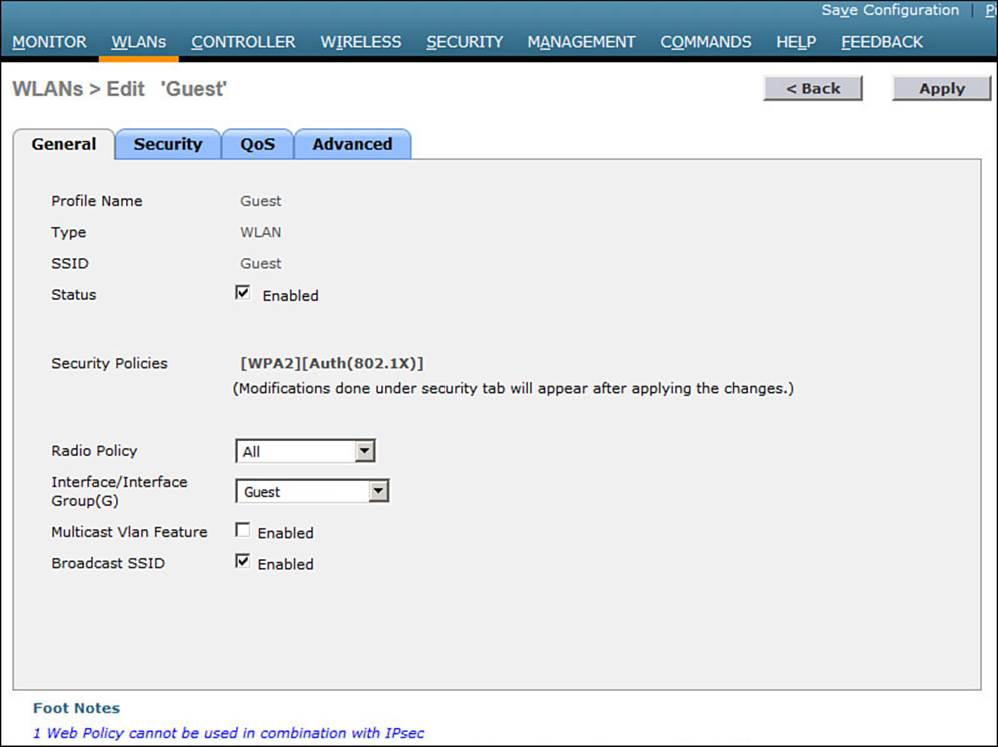
Figure 16-7 Assigning a Dynamic Interface to the Guest WLAN
Step 4. Configure the wireless security method.
On the Security tab, you can select the Layer 2 tab to choose a wireless security scheme to be used on the WLAN. In Figure 16-8, open authentication will be used because the None method has been selected.
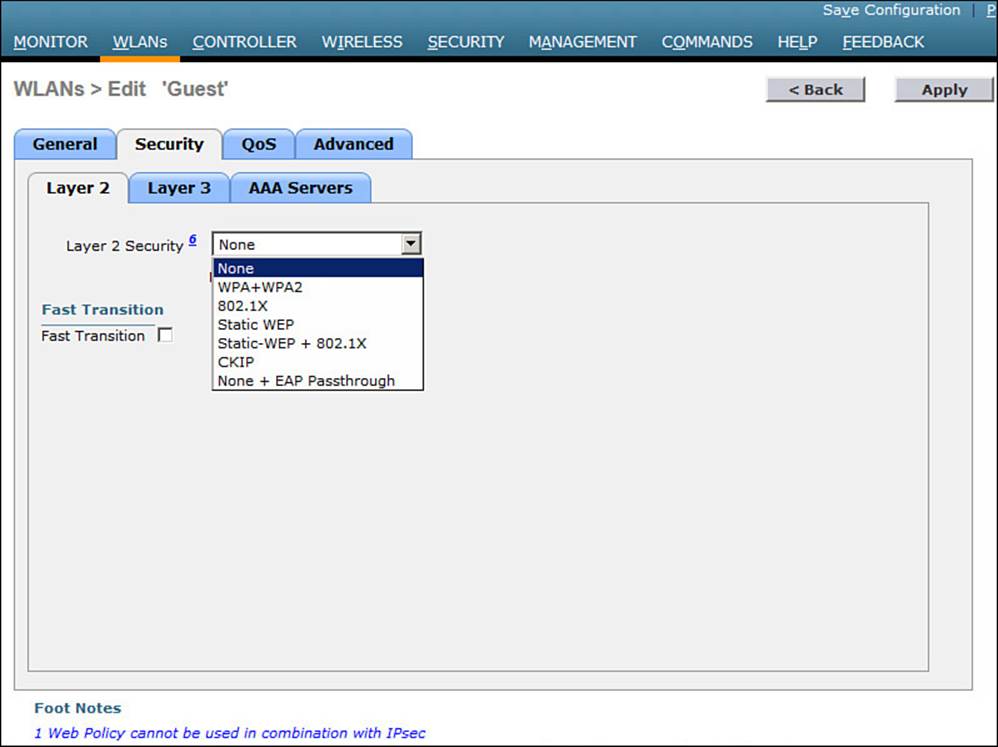
Figure 16-8 Selecting Open Authentication for the Guest WLAN
Step 5. Configure web authentication.
Select the Security > Layer 3 tab, then choose Layer 3 Security type Web Policy, as shown in Figure 16-9. When the Authentication radio button is selected (the default), web authentication will be performed locally on the WLC. You will also need to define local usernames that will be used when guest users authenticate.
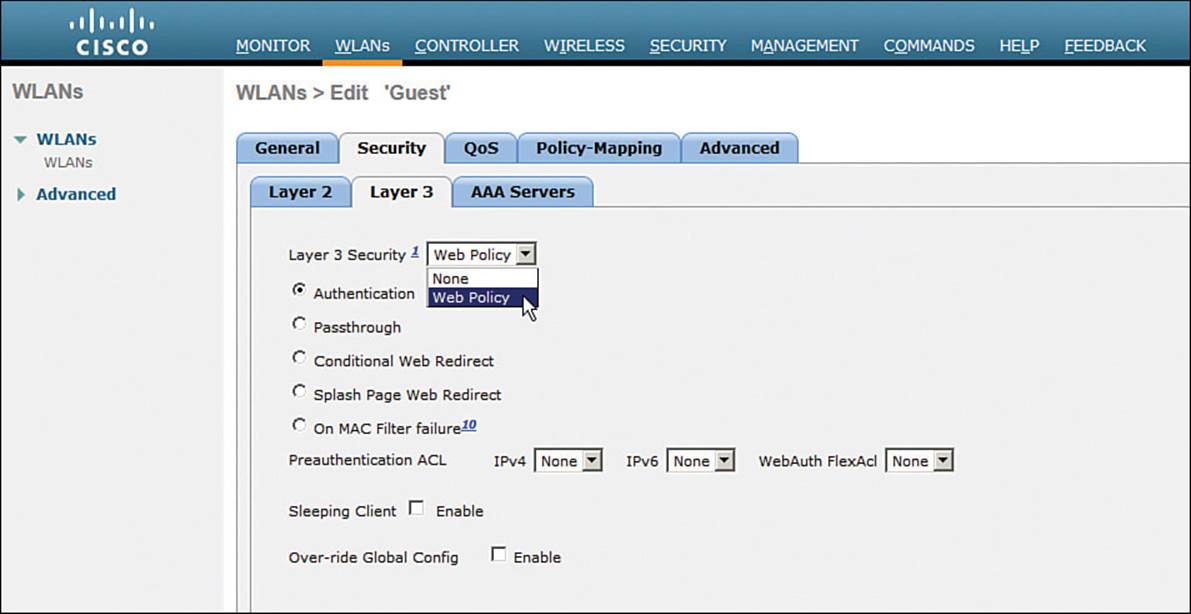
Figure 16-9 Selecting Web Authentication for the Guest WLAN
Be sure to visit the QoS and Advanced tabs to complete the guest WLAN configuration.
Step 6. Configure mobility anchors (for larger networks).
If your network consists of multiple controllers, you should configure guest WLANs on each one where guest users might connect. Be sure to configure them consistently. Then identify one controller that will serve as a mobility anchor for all guest users hosted by other controllers. All of the foreign controllers (the ones you are configuring) should be configured in the same mobility group to allow roaming, as described in Chapter 12, “Understanding Roaming.” The anchor controller does not need to be in the same mobility group because no roaming is expected between APs on the foreign controller and APs on the anchor. In fact, it is common practice to purposely configure the anchor in a different mobility group to prevent any risk of roaming.
Be aware that even the anchor controller must be configured with an anchor controller (itself) so that it will accept guest wireless tunnels from the foreign guest controllers. Select the WLANs tab to display the list of WLANs. At the far-right end of the guest WLAN entry, right-click the blue triangle, and then select Mobility Anchors from the drop-down menu, as shown in Figure 16-10.
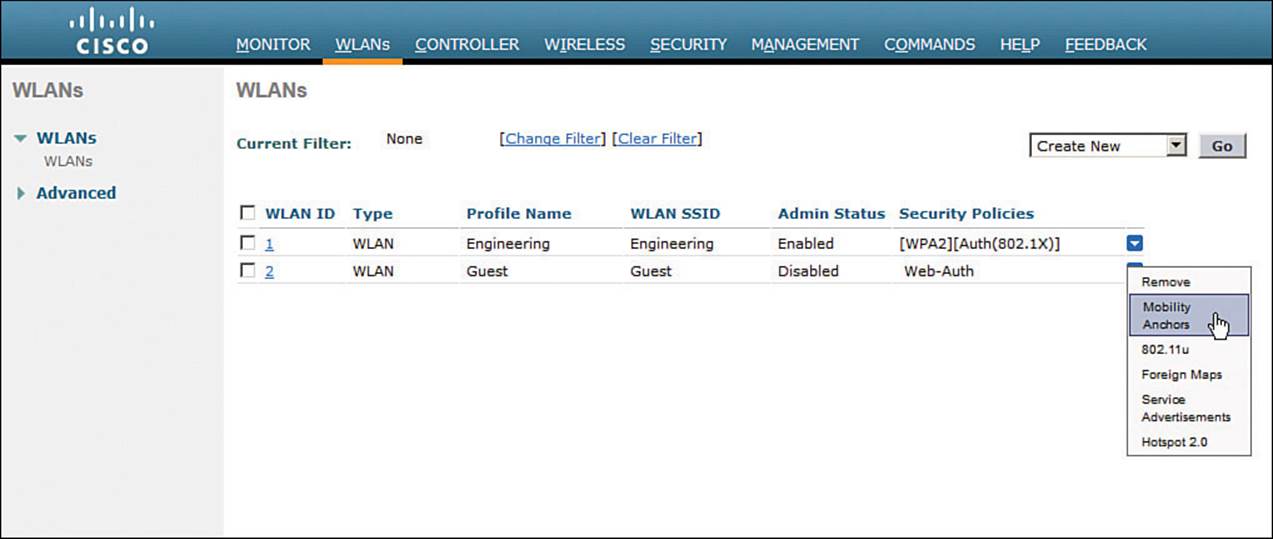
Figure 16-10 Displaying Mobility Anchors for a Guest WLAN
From the Switch IP Address (Anchor) drop-down menu, select the anchor controller from the list of controllers that are members of the mobility group. The local entry that is displayed in the list of switch IP addresses represents the controller you are configuring. Click theMobility Anchor Create button as shown in Figure 16-11. Once the foreign and anchor controllers know about their new relationship, they will display the status of their mobility tunnel. You should see the control and data paths listed as “up.”
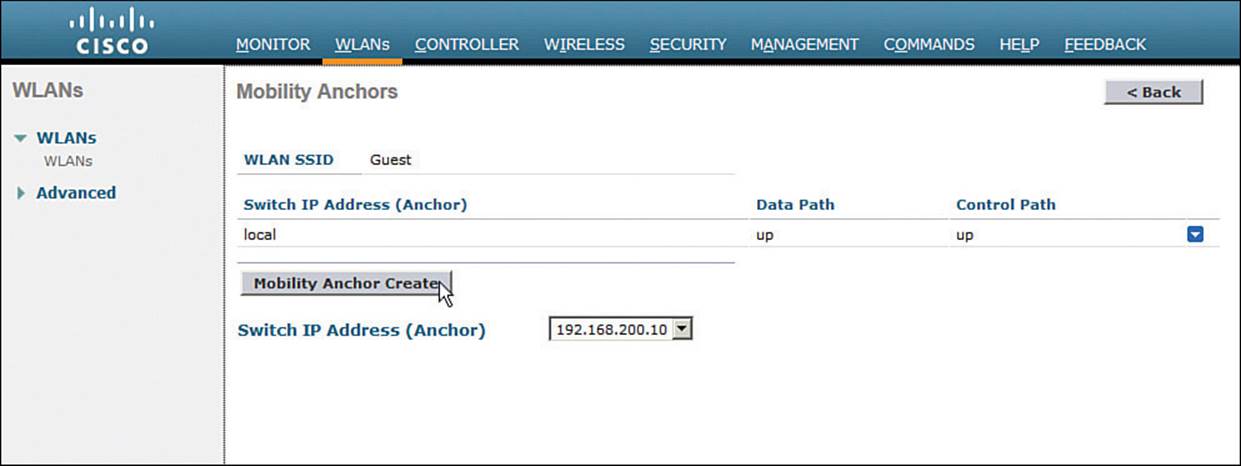
Figure 16-11 Identifying a Mobility Anchor for a Guest WLAN
Exam Preparation Tasks
As mentioned in the section, “How to Use This Book,” in the Introduction, you have a couple of choices for exam preparation: the exercises here, Chapter 21, “Final Review,” and the exam simulation questions on the DVD.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topic icon in the outer margin of the page. Table 16-2 lists a reference of these key topics and the page numbers on which each is found.
![]()

Table 16-2 Key Topics for Chapter 16
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
central web authentication (CWA)
guest WLAN
local web authentication (LWA)
mobility anchor
All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.