5 Steps to a 5: AP Computer Science Principles 2024 - Sway J.S. 2023
11 Impact of Computing
STEP 4 Review the Knowledge You Need to Score High
IN THIS CHAPTER
Summary: Computing has impacted all aspects of our lives, from communication to shopping to research. It has provided ways to share and innovate. These innovations are sometimes used in unexpected ways, causing unanticipated results. Sometimes these are beneficial, such as the World Wide Web expanding from sharing scientific papers to what it is today. Other times these unforeseen results can have privacy, security, legal, and ethical concerns.
The “digital divide” deals with who does not have access to the Internet and the equity and access issues that result. The recognition and impact of bias in computing innovations is another issue that can be difficult to identify but very important to do. Access to information via the Internet has allowed the “crowd” to become involved in many new ways, including “citizen science” and funding new businesses or emergency relief anywhere.
With all of these opportunities on the Internet, our personally identifiable information (PII) is potentially stored or willingly shared, leaving us vulnerable to issues such as identity theft. We are also exposed to malware of various types that attempts to steal our PII or infect and damage our devices. Authentication and encryption help shield us from these attempts.

Key Ideas
![]() New technologies can have both beneficial and unintended harmful effects, including the presence of bias.
New technologies can have both beneficial and unintended harmful effects, including the presence of bias.
![]() Citizen scientists are able to participate in identification and problem solving.
Citizen scientists are able to participate in identification and problem solving.
![]() The digital divide keeps some people from participating in global and local issues and events.
The digital divide keeps some people from participating in global and local issues and events.
![]() Licensing of people’s work and providing attribution are essential.
Licensing of people’s work and providing attribution are essential.
![]() We need to be aware of and protect information about ourselves online.
We need to be aware of and protect information about ourselves online.
![]() Public key encryption and multifactor authentication are used to protect sensitive information.
Public key encryption and multifactor authentication are used to protect sensitive information.
![]() Malware is software designed to damage your files or capture your sensitive data, such as passwords or confidential information.
Malware is software designed to damage your files or capture your sensitive data, such as passwords or confidential information.
Key Terms
Asymmetric ciphers
Authentication
Bias
Certificate Authority (CA)
Citizen science
Computer virus
Creative Commons Licensing
Crowdfunding
Crowdsourcing
Cybersecurity
Data mining
Decryption
Digital divide
Encryption
Intellectual property
Keylogging
Malware
Multifactor authentication
Open access
Open source
PII (Personally Identifiable Information)
Phishing
Plagiarism
Public key encryption
Rogue access point
Symmetric key encryption
Targeted marketing
Virus
New Ways to Communicate and Interact
Thanks to the Internet and the ease of collaboration and sharing, programs and apps (software applications) can be quickly and easily shared with people worldwide. These can sometimes have a huge impact, positive or negative, on people, and sometimes have additional results not originally foreseen by the software developers. Along with these, advances in programming languages have also spread software development to many other disciplines, such as science and art, resulting in innovation in those fields.
People are wonderfully creative, and there are many computing innovations that have since become widely accepted and a part of our everyday lives. We’ve changed the way we shop with online e-commerce, and our doctors are available to connect with online before we visit their office. We can get where we need to be without getting lost or stuck in traffic. Our food is ready for delivery, sit-down service, or pick-up from restaurants. The list goes on. These apps and websites are just the tools we need to solve problems, make something easier, or are just fun to have and use. There are few limits to the continued creation of new computing innovations! Some of the positive outcomes impacting our lives daily include:
• The World Wide Web, which was originally designed for scientists to share their research. Now we have much of the world’s information within our reach.
• Targeted advertising, which can be helpful for businesses and consumers when looking for a specific item.
• Social media, which has been used to stream events across the globe, sometimes helps to change history. Social media sites and blogs have changed the way many people share information. News of events is shared in “real time,” meaning as events are happening, by people who are attending the event. Videos and stories go “viral,” meaning they quickly get many views and are shared for even more views. These features allow us to have a better understanding of other parts of the world as well as to be entertained. However, remember that certain governments block some or all content from the Internet for their citizens.
NOTE: Questions about specific social media sites will not be on the AP exam.
• Machine learning and data mining help find patterns and identify insights in data, leading to new innovations.
However, with the benefits of having these, there are also potential downsides when computing innovations are used in unintended ways, including:
• People using social media to bully others by posting anonymously and spreading false information. Others then continue to share the falsehood. People also use social media to spread inaccurate information and scams. These are serious negative impacts of the use of the Internet and social media.
• Homes can be robbed when owners post about being away.
• Discrimination can occur based on information gathered through data mining.
Advances in computing continue to enable innovations in other fields. 3D printers can print artificial limbs, and research is underway for the printing of tissue and organs. 3D printers can also print homes, providing a low-cost option for homeless populations. These were unexpected benefits of 3D printing stemming from its use in different fields.
Medical files, test results, and x-rays can be digitized and sent to specialists in any part of the world for evaluation. Physicians are able to collaborate with experts located anywhere in the world and can be looking at the same test results at the same time. Simulations are increasingly realistic, allowing surgeons and pilots to develop their skills before people are involved.
Online learning is an education model that would not be possible without the tools of communication available via the Internet. Now you can have classmates from anywhere in the world. You can also attend class if you are in a different location from your teacher. Teachers are able to do a combined lesson with a class elsewhere in the world using video conferencing tools. This can expose students to a global perspective that can impact people’s understanding of each other, their cultures, and the challenges they face, as well as identify things they have in common.
The list can go on and on. Essentially, every other field has used technology for advances in some aspect of their area of interest. The only limitation is our imagination.
Programmers and businesses try to identify potential negative uses, but it is seldom possible to think of all the ways other people could use an innovation. Of course, some of these, such as targeted advertising, could be positive or negative, depending on your perspective.
The World Wide Web (www), an application running under the Internet, makes it easy to share documents, videos, and all types of computing artifacts as well as create interactive sites where others can provide opinions, advice, and suggestions. This has changed the way businesses and organizations operate. Cloud computing is one example. Businesses have also been able to meet remotely and conduct meetings via technology tools such as video conferencing tools. This saves money on travel expenses and can provide flexibility for employees. It also allows meetings, events, school, and connections to continue during quarantines caused by pandemics!
Access to Information
Cloud Computing
Cloud computing offers new ways for people to communicate, making collaboration easier and more efficient. Storing documents in the “cloud” simply means they are stored on a computer server at a location different than where the owner of the files is located. The documents are accessible via an Internet connection to anyone with verified access to it. This provides several benefits, including the ability for multiple people to update one document at the same time. This eliminates the problem of keeping track of multiple versions of the document—a major headache in the past. People could accidentally overwrite other people’s changes or be viewing an out-of-date version.
Another benefit of cloud computing is that people can access the document stored in the cloud from any device, at any time, at any location that has Internet access. This also allows multiple experts to easily evaluate and review documents, leading to better outcomes, whether it’s evaluating a medical condition, a business plan, or a group project for a class.
Digital Divide
Technology has had a major impact on the world, enabling innovation through the sharing of resources and computational artifacts. It also allows us to virtually meet with people from anywhere. It is helping us on the path of becoming a true global society.
While the Internet and the World Wide Web have had a global impact on the ease of sharing and collaborating, it is important to remember that not all areas of the world have the same access. Rural and remote areas often have limited, as in slower, or even no access to the Internet. Other areas do not have the infrastructure to support digital access. There are those who cannot afford the fees to connect to the Internet and the web or buy the devices to do so. Many businesses exist to provide this access, but they may not consider it profitable enough to provide the access in some areas, impacting groups and individuals in cities, suburbs, and rural communities.
While the Internet and the World Wide Web are not “owned” by anyone, each government determines which citizens may have access and which websites they may view. The elimination of “net neutrality” has the potential to create an additional divide where those with the funding have faster and better access to the Internet and the web.
The impact of the digital divide includes access to information, knowledge, markets, and different cultures. Perhaps most importantly, the digital divide impacts the ability for all to have a voice and a chance to hear and be heard in their community and across the globe.
Bias in Computing Innovations
Bias, which is intentional or unintentional prejudice for or against certain groups of people, shows up in computing innovations too. Humans write the algorithms, and our biases can make their way into the algorithms and the data used by innovations without us realizing it. It is a programmer’s responsibility to work to remove bias in algorithms. This is difficult when people are not aware of their own bias. In addition to being at the algorithm level, bias can also be introduced at all levels of the software development process.
Artificial intelligence programs are used more and more in ways such as screening applications of job candidates, determining if a person merits credit to purchase a house, and locating what areas have more crime. When these applications have bias built in, it can be difficult to detect it and then even more so to remove it. The reasoning behind decision-making is where bias gets introduced. The decisions are usually based on profitability potential and aren’t considering fairness. For example, one business used historical hiring information with its applicant screening software. Because more men had been hired previously, the algorithm continued that trend and eliminated far more female candidates. Determining which attributes to consider can introduce bias into your algorithm and result in skewed results, however unintentionally. The introduction of bias is not easily identified early in the process or may not be seen until further into the process when results are received and analyzed. Although it can be difficult, it is important to identify where in the process the bias was introduced and resolve it for a fairer future outcome.
Crowdsourcing
Crowdsourcing allows people to share information and ask the “crowd”—anyone who accesses the site—for feedback, to help solve problems, find employment, or for funding. Another use of crowdsourcing is when scientists share data and ask nonscientists, or “citizen scientists,” to look for and report on patterns or other interesting features of the data or to “donate” computer time during periods of time their machine is inactive. This helps to “scale up” processing capability at little to no cost to the organization seeking the resources. This helps researchers collect data at multiple locations and expand the time period for collecting data. When the research team has too few members to collect all the data they need or does not have an adequate budget to visit all the locations that could provide data, citizen scientists can bridge the gaps. The research teams can likely produce better insights because of the availability of additional data.

Examples of “citizen” science include monitoring monarch butterfly and bird migrations, recording plastics that wash up on beaches worldwide, and classifying galaxies! People are also willing to write documentation, identify photos, and provide all types of assistance. These collaborative efforts help people and society as a whole with discoveries and advances in many fields. As stated earlier, people with different backgrounds look at solving problems in different ways, often because they don’t know something “shouldn’t be possible.” For example, back in 2011, gamers played an online puzzle called Foldit that researchers set up for help folding proteins. Researchers had been working on it for over a decade and the group in the gaming world solved it in three weeks. The gaming community didn’t work with preconceived ideas of how proteins should or should not work. Instead, they tried everything! This led to advances in medical research and treatments.
Crowdfunding helps inventors, individuals, and businesses fund their ventures with a little bit of money from many sources. The Internet has made it possible now to see easily what new innovations or events people are trying to raise money for from anywhere in the world.
Legal and Ethical Concerns
Anything a person creates, including any computational artifacts created with a computer, is the intellectual property of that person. The Internet makes it easy for people to share their creations with the world. Unfortunately, it also makes it easy for others to take their work and use it without permission or payment. This is plagiarism and has resulted in people getting a grade of zero on an assignment, failing a class, losing a job, or facing legal issues along with the embarrassment that goes with it. Material created by someone else that you use in any way should always be cited. Fortunately, there are ways to deal with the permissions needed to protect and share your intellectual property.
Over the years, there have been many examples of illegal downloads and sharing of music, games, and videos. Peer-to-peer networks exist that are used to illegally share files of all types. “Mashups” where people combine content created by others is a copyright concern, especially if they earn money from doing so. Many of these have resulted in lawsuits challenging whether someone’s intellectual property is changed enough that someone does not have to compensate them for using it.
As mentioned earlier in this chapter, algorithms with bias in them can have both legal and ethical issues. Devices that continually monitor and collect data, such as a voice-activated device we install or video cameras used for facial recognition posted in our communities, can have legal and/or ethical issues. Even when people have approved access to information, choosing to use that access in legal and ethical ways matters. Often digital innovations become accepted with widespread use before legal implications can be determined. There always seems to be something in the news where someone shared, used, or sold information for unethical purposes. These instances cause the legal system to then create laws regarding such use. Often the damage is already done before that can happen. On the other side of the coin, censorship of digital information by government, businesses, or individuals is also harmful and raises ethical, if not legal, concerns.
Creative Commons
Creative Commons provides a way for creators of software, images, music, videos, and any computational artifact to share their creations with stipulations for sharing and permission from the author clearly indicated. Creative Commons provides six levels of licensing that the owner/creator decides for their work. These levels include no restrictions on use, use with and without attribution, the ability to modify with and without attribution, and whether someone other than the original author can sell it.
Digital data is easy to find, copy, and paste, so ensuring you have written permission from the creator or owner is important. Just as it is easy to find many computer artifacts on the web, it is also very easy for people to search for their artifacts to see if someone is using them without permission. If you use something without permission, be prepared for official consequences, including a fine and orders to remove it, among other potential legal actions.
Open-Source Software
Not only do we have access to data but to software as well. “Open source” software is software that is freely shared, updated, and supported by anyone who wants to do so. The availability of this software for everyone has greatly expanded people’s abilities to participate in a variety of tasks that many would not have been able to participate in otherwise. Allowing many to develop the software ensures a better product with ideas and solutions to problems from many perspectives. It also is generally a less error-prone product because of all the people testing the software.
Of course, there are also concerns if someone takes code from these openly available programs and either uses it with additional code they wrote, markets it in some way claiming it as their own, or inserts malware into the open-source code, thereby impacting everyone who then downloads it. The malware would be quickly found and corrected due to the many people constantly working and communicating about the code but still impacts those who downloaded it.
Open Access
The sharing of huge amounts of public data by organizations, such as the U.S. government, provides the opportunity for anyone to search for information or to help solve problems. In addition, the availability of open databases in a variety of fields—including science, entertainment, sports, and business—has benefited people everywhere. People identify issues and opportunities, leading to new facets and products for research, production, and sales.
All three of these, Creative Commons, open source, and open access, have provided wide access to digital information. The world’s information is accessible—or at least a great deal of it is. But this also reminds us of the digital divide, as many people do not have a device and Internet access to retrieve and contribute to this worldwide source.
Search Trends and Analytics
Social media sites as well as search engines publish what the most frequent searches and posts are about. Our browsers keep a list of our most frequently visited sites on their home page to help us out. The search engines are able to identify when more people than usual are watching a video or searching for a topic. Companies use this information to predict trends and then use their information about related topics to share with those searching and researching. Similarly, analytics identify trends for marketing purposes and help businesses determine what and where customers are searching for their products and their competitors’ products, how long an item sits in a virtual shopping cart, and when people buy.
Data Mining
Data mining is a field of study that analyzes large datasets. Companies may use the results to determine when to offer a discount for specific products. Machine learning is a subset of data mining. Machine learning uses algorithms to analyze data and predict behavior and is used in Artificial Intelligence (AI). Companies then use this information to target ads or products to you based on your prior searches or purchasing behavior. It can also be used for a potential fraud alert if your bank detects unusual activity on your account. The machine has “learned” your usual patterns and issues an alert if something is different. If the software used is able to predict more accurately over time, then it is considered machine learning.
Science and business have both benefited from these new sources of information. Data mining has been able to predict when someone will need a new battery for a pacemaker or drop out of a research study so those leading the project can work more closely with the person to try and prevent it. The medical field is working to identify risk factors for diseases to help those at risk make changes to reduce their chance of contracting the disease. For the business world, retaining employees is important to keep knowledge and the company’s investment in training the employee in-house. The use of computers to evaluate job candidates has resulted in a higher retention rate.
Personally Identifiable Information (PII)
Any information that identifies you is considered Personally Identifiable Information (PII). It includes data such as your address, age, or social security number. It also includes data about you, such as your medical or financial information. One category many people don’t consider is biometric data. If you use your fingerprint to log into your computer, that is biometric data. Retina scans and facial scans can also be stored online. Websites, apps, and networks also track our location.
As with most things, having your PII online has pros and cons. One positive is that creating an account with a website and filling in personal information that will be saved is useful for future purchases. It saves us time and typos by not having to key in the same information each time. Our PII information is also used by websites to show us certain information or related topics based on our prior visits. Again, this can be helpful or feel invasive or creepy. These sites track how long you were on their site, what you viewed, perhaps placed in a shopping cart, actually purchased, or removed without purchasing. This information is used to entice us with additional ads or an offer of a lower price.
Our devices also track our locations. You’ve probably received a text or e-mail asking about your experience at a store, restaurant, or other venue and asking you to post on social media. (Sometimes I get them when I only walked by a business and never went in!)
All of this data about us is in many different places. A little may be on one website, and some different information may be on another. Since many companies sell the data about us, either notifying us in the very fine print or not at all, this opens the door to all this information being available. As we’ve discussed throughout the course, software exists to sift through data looking for patterns and similarities. Our information can end up being pieced together.
Further, as listed earlier in this chapter, the government, some research sites, and nonprofit organizations provide open access to large databases about many topics. This is great for research and information that would not be available otherwise. Our personal information should not be identifiable and should be only available aggregated with thousands or millions of other records. This means summarizing, removing some aspects, and masking the data findings at such a high level that no individual or group should be identified. However, done incorrectly, individual information can and has been identifiable. It is surprising how one small identifiable piece of data, such as a zip code, can be used with other legally available public sources of data on the web to identify a person. All too often, this invasion of privacy is either posted or shared in ways unknown to those impacted.
Always remember that once data is on the web, it is difficult if not impossible to delete. As soon as you press Send on an e-mail or social media post, it is out of your control and can be forwarded or altered with your name attached to it. Students have been denied or had college admission and scholarships rescinded because of their social media posts. Adults have lost jobs due to their social media posts. People will make assumptions about you based on your posts. You will change as a person over the years, but since data is permanent, be cautious now.
We should always watch and check over our PII because it is our identity, and once stolen, it can impact finances or career and involves a long process to clear up. People can also use it for criminal activities.
Privacy
Digital footprints and fingerprints are the trail of little pieces of data we leave behind as a sign of our presence as we go through our daily lives. Some of the ways our data is collected occurs via:
• GPS coordinates embedded in photographs and apps showing our location
• Financial transactions such as viewing, comparing, and making purchases
• Websites visited
• Cell phones pinging off towers
• Key card access to locations
Many people willingly provide personal information to sites to gain access or privileges, whether it’s through sports teams, shopping, or restaurants. Their data is stored and may be sold with or without their knowledge or permission. While the perks of being a frequent customer can be nice, if your information is compromised or used against you, such as your house being robbed because you posted you were out to dinner, the benefit is clearly not worth it.
Sometimes the information is used at a personal level, such as businesses sending special offers to people who visit their stores a certain number of times. Targeted advertising can be useful when you are searching for something, like that perfect gift. However, the downside is that you may only be shown items the algorithm thinks you would like and you may never see other items. This limits your access to other products and information and impacts those potential businesses. These raise privacy and potential security concerns if identifying information about us is still available in the local datasets.
There are ways to search in anonymous mode to prevent this tracking. Many web browsers now have “incognito” or “private” modes so that web searches and file downloads are not recorded in the web history. Some web browsers attest that they do not track and retain your search data. There are also ways to be more anonymous to avoid tracking by websites, such as blocking cookies, installing add-ons to prevent them from tracking your device, and using proxy servers, among other techniques. These are constantly evolving as other software is developed to get around them.
It is a constant challenge, because sometimes by accident, and sometimes on purpose, all the data that has been collected about us is released to those who should not have it or to the world at large. When this involves medical information; financial information, such as credit card numbers; and personal information including social security numbers—it puts our safety, personal and digital, at risk. Once it is online, it is essentially impossible to remove data. Tools such as the Internet archive “The Wayback Machine” can show social media posts that have been deleted. It’s never really gone. Backups and screenshots by unknown people mean it can resurface at any time.
Any technology used to harm people is highly unethical and potentially illegal. Internet troll factories attempt to spread misinformation and interfere with many facets of our lives, including tampering with elections and adding racial elements to news and nonrelated events. Organizations or external sources scrape websites for our personal data and sell it to others or release it without our knowledge. Always be cautious and aware that with all the good the Internet provides, others will attempt to manipulate us using the same tools we use in our everyday lives.
Protecting Our Data
Many aspects of our lives are much easier today because of the easy access to all sorts of sites and information that the Internet provides. This can range from shopping, entertainment, and sports sites to price comparisons. We can research health symptoms and medical treatment and find vetted sources for research. We can also find online classes taught by instructors anywhere in the world, as well as illegal sites and transactions as we pick up viruses and other malware along the way.
The Internet has created a way for easy access to worldwide audiences. Providers of goods and services can directly access their customers, eliminating the importance of all types of “middlemen” from brick-and-mortar stores to publishers and music distributors to radio-dispatched taxis. This has changed the way we shop, get our entertainment, schedule a ride, and even obtain financing for projects. But this also raises security, privacy, and ethical concerns related to many aspects and uses of the Internet. Cybersecurity has a global impact because now anyone from anywhere can attempt to gain unauthorized entry to someone else’s computer, data, servers, or network.
Security
The security of our data deals with the ability to prevent unauthorized individuals from gaining access to it and preventing those who can view our data from changing it. Strong passwords help block those trying to gain unauthorized access. That is one reason many sites have increased their password requirements to contain components such as:
• A capital letter
• A number
• A special character
• A specified minimum length
• Cannot be the same or almost the same as a previous password
• Cannot be the same as the user ID
Multifactor authentication is another layer that is increasingly used. For example, if someone tries to reset your password, they cannot do it without the second layer of authentication. Sometimes this involves answering questions based on information only you would know, confirming via another account or your cell phone that you are attempting this action, or using a feature of inherence, such as your fingerprint scan.
We trust the companies that maintain our personal information, including social security number and financial information like credit card numbers, to keep it secure. As the news often reports, many companies have had their security defenses breached and customer data stolen. The data often is sold to those planning to use unsuspecting users’ identities to open accounts and make purchases. Always check your accounts often!
Cybersecurity
Cybersecurity protects our electronic devices and networks from attacks and unauthorized use. These attacks can come in many forms and can have a major impact on those affected. Many of them come into a network or device through e-mail. An unsuspecting person clicks on a link that downloads a computer virus or other form of malware (the term “malware” comes from “malicious software”). Different types of attacks cause different problems. Data may be damaged or the device may be used to further spread the malware.
Phishing attacks create e-mail and/or websites that look a legitimate hoping to induce a person to click on the malicious link. These sites often prompt a user for their password, credit card number, or other sensitive data under the guise of a valid transaction. The password or other personal information is then used and/or sold for illegal use. This is called social engineering when people are tricked into providing information such as passwords or clicking a link that appears legitimate. We are the weakest link in the steps designed to protect our devices and information.
Computer viruses are like human viruses. They attach themselves to, or are part of, an infected file. There are many types that can damage, delete, or steal your files and use your system to spread to other devices. Viruses spread by being embedded in or attaching to a legitimate program to infect your system. They can then begin to run their code on your computing device. Do not click on files in an e-mail from people you do not know, or even from someone you know, if you are not expecting an attachment. Someone else’s system may have been compromised and is propagating the virus by sending out infected messages to everyone in the address book on the infected device. That is a common way viruses are spread. Many websites offering free downloads of games or movies often contain malware. Nothing is really free—there is always a cost of some sort.
Keylogging software is a form of malware that captures every keystroke and transmits it to whomever planted it. They then run software to sift through the keylogger file attempting to identify passwords or other personal information you’ve entered.
Access points are used to create wireless networks. Public networks such as those at restaurants, stores, and hotels don’t require a password to join the network. People can run software on the same open network to intercept your signals and sift through the data looking for passwords. Rogue access points are when someone sets up an access point that is not managed by that organization on their secure network. Anyone on that network could then have their signal intercepted, data captured, or potentially modified. Additionally, someone external to your organization could access your secure network through the rogue access point.
The solution for computer malware is to use antivirus software, firewalls, and caution when downloading or opening files from an unknown or unexpected source. As much as developers try to avoid this, computing systems have errors and design flaws. These vulnerabilities are exploited by those wishing to compromise a system for some type of gain or just to see if they can. Keep current with installing updates for your antivirus software and your operating system. These updates correct errors that are or could be exploited, so they are very important.
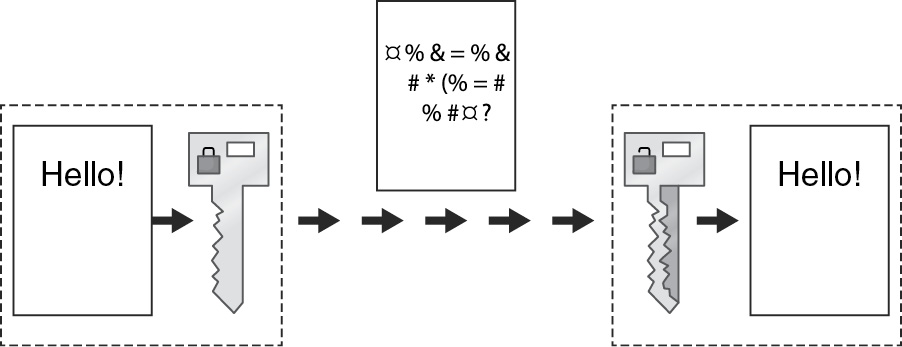
Cryptography
Cryptography is the writing of secret codes. It has been used for thousands of years and is the reason we are able to have secured online shopping and keep our data in “cloud” accounts secured with our passwords today. Encryption is converting a message to a coded format. Deciphering the encrypted message is called decryption. Security also relates to encrypting data before it is transmitted to ensure it remains secure if it is intercepted during transmission. The location you sent the data to would decrypt the data for it to then be used as needed.
Ciphers are coded messages, and all ciphers have two parts:
• Key: allows the creation of secret messages
• Algorithm: the set of steps used to transpose the message to be unreadable to anyone but the person who holds the key
Julius Caesar is credited with the Caesar cipher, one of the first ciphers, which is a secret code system. It shifted letters over three spaces and took 800 years to be broken. It is a “symmetric cipher,” which means that the same key is used to encrypt and decrypt the message.
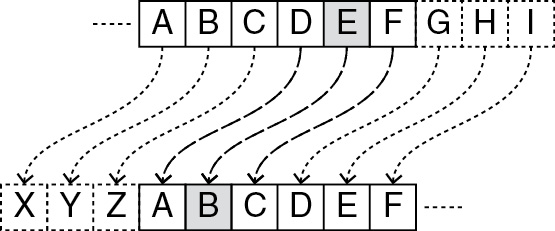
Public Key Encryption
Today’s algorithms use asymmetric keys, meaning two keys will be needed, one to encrypt and the other to decrypt the message. Public key encryption uses open standards, meaning the algorithms used are published and available to everyone and are discussed by experts and interested parties and known by all. The key is what keeps information secret until the person it is intended for decrypts it. In this case, the public key is used to encrypt data and is published to anyone. Messages are then decrypted using a private key. The sender does not need the private key to encrypt the message; only the recipient of the message needs it. This is considered a one-way function. That means the function is easy in one direction and difficult in the other. This algorithm creates such large numbers for the key that a brute-force attack, which is checking each possible solution, cannot break the code. In other words, a solution exists, but our current-day computers do not have adequate resources, memory, or time to solve it.

NOTE: The cryptography algorithms are based on mathematical functions, and these are not covered on the AP exam.
Securing the Internet
The Internet is based on a “trust” model. This means that digital certificates can be purchased from Certificate Authorities (CAs), which identify trusted sites. They issue certificates that businesses, organizations, and individuals load to their websites. The certificates verify to web browsers that the encryption keys belong to the business, thereby enabling online purchases and the sending and receiving of secure documents.

NOTE: The details of how CAs work is not on the AP exam.
Always check your personal permissions on your social media accounts, permissions you grant websites for information they can collect about you, and what they can do with it. More visibility is being provided about this, but it will probably never be truly transparent. Regularly check your settings because a site may do an update that changes your settings or the intent you had with your settings. Do what you can to protect the privacy of your information.
![]() Review Questions
Review Questions
Concepts
1. When access to the Internet is unequal based on geographic or socioeconomic reasons, it’s referred to as the
(A) Internet divide.
(B) wealthy divide.
(C) distance divide.
(D) digital divide.
2. What is an example of sharing images and allowing individuals to scan them for certain features?
(A) Heuristics
(B) Moore’s law
(C) Citizen science
(D) Contaminated research
3. What is the name for programming code that is available to anyone to use or modify?
(A) Licensed software
(B) Open-source software
(C) Compiled software
(D) Open access software
4. What has Creative Commons provided?
(A) Free use of other people’s work
(B) Ways to share other people’s creations without their knowledge
(C) Licensing options by the owners of artifacts
(D) Cooperative copyright arbitration
5. The ability to retrieve previously published data and research rather than each organization paying for or collecting their own data to analyze is an example of?
(A) Creative Commons licensing
(B) Free access rights
(C) Open access
(D) Open source
6. People trading personal information for perks from companies is an example of which of the following?
(A) The use of proxy servers
(B) Privacy concerns
(C) Legal issues
(D) Authentication exposure
7. What is the term for showing someone information based on their prior searches and purchases?
(A) Targeted advertising
(B) Open-source marketing
(C) Open access marketing
(D) Aggregation of data
8. Granting access after clearing at least two steps of authentication, such as a password and code sent to your cell phone, is called
(A) compound authentication.
(B) complex authentication.
(C) frequency analysis authentication.
(D) multifactor authentication.
9. What is one way that does NOT prevent password-cracking programs from easily identifying your password?
(A) Using a mixture of upper and lowercase letters
(B) Using special characters as part of your password
(C) Making it easy to remember so you do not have to write it down
(D) Using former pet names that hackers could never know
10. Using social engineering to trick users into providing their personal information is called
(A) keylogging.
(B) phishing.
(C) pharming.
(D) spearing.
Application of Concepts
11. Schools that provide each student with a computing device for school and home use but that do not ensure all students have equally reliable and fast Internet access are contributing to the
(A) digital divide.
(B) equity influence issue.
(C) Internet gap.
(D) preference issues.
12. Many forms that collect personal information do not include responses for all ethnicities. This is an example of
(A) bias.
(B) partiality.
(C) subjectivity.
(D) predisposition.
13. Using an app to notify many people about child abductions, such as an Amber alert, is an example of
(A) compliance.
(B) consensus building.
(C) crowdsourcing.
(D) open sourcing.
14. A business’s website tracks items that are viewed by visitors to its site. Which question cannot be answered by tracking this data?
(A) Which items will sell during each season in different parts of the world
(B) The trending colors that could be popular in the next year
(C) The income range of prospective customers
(D) How many of each item to produce
15. Which of the following is an example of plagiarism?
1. Writing about an idea you read about
2. Making minor changes to wording in a paragraph
3. Retyping text rather than copying and pasting it into a document
(A) 1 and 2
(B) 1 and 3
(C) 2 and 3
(D) All of the above
16. What is a symmetric key used for?
(A) Sending and receiving information from the web
(B) Encrypting data
(C) Decrypting data
(D) Encrypting and decrypting data
17. Cryptography today uses which of the following?
(A) Published algorithms available to all
(B) Algorithms known by only a few members of the IETF governing organization
(C) The Caesar cipher
(D) Undecidable algorithms
18. Computer viruses can replicate after infecting a computer. How are they transmitted?
(A) By attaching to a valid program or file
(B) By visiting a website that is infected
(C) By clicking on a link that takes you to a counterfeit website designed to look like a legitimate one
(D) By being on the same network as an infected device
![]() Answers and Explanations
Answers and Explanations
1. D—The digital divide refers to unequal access to the Internet based on geographic or socioeconomic reasons.
2. C—Sharing images and allowing individuals to scan them for certain features is an example of citizen science.
3. B—Open-source software is available to anyone to use or modify.
4. C—Creative Commons allows owners to designate licensing options for their digital creations.
5. C—Open access provides access to scholarly articles, data, and research without any restrictions.
6. B—People trading personal information for perks from companies is an example of a privacy concern.
7. A—Targeted advertising is showing someone information based on their prior searches and purchases.
8. D—Multifactor authentication requires the user to clear at least two levels of protection before gaining access.
9. D—Using former pet names will not prevent your password from being compromised. Posts on social media and name programs can work in combination to identify your password.
10. B—Phishing attacks use techniques such as sending e-mail with a link to a website that looks exactly like a legitimate organization but is bogus. Users provide their password, which is then captured and used on the real website to impersonate you.
11. A—The digital divide is when different levels of access to the Internet impact certain groups.
12. A—This is an example of bias in the data collection process that leads to inaccurate data for decision-making.
13. C—Using information from many people is an example of crowdsourcing.
14. C—The data tracked can provide reasonable information about everything except a potential customer’s income level.
15. D—All of the examples are instances of plagiarism. Ideas must be cited as well as text that is only minimally changed and content you copy either by retyping or pasting into a document.
16. D—A symmetric key is used for both encrypting and decrypting data.
17. A—Cryptography today uses published algorithms available to all. The key used for decryption is private.
18. A—Viruses are transmitted through embedding them in a document or program. Once the document or program is on a new computer, the virus can start running and replicating.
Rapid Review
Advances in technology have enabled the development of new and innovative creations and solutions in many fields. These advances have changed the way people interact with each other, in both positive and negative ways.
There are many ways to communicate, including e-mail, texting, and social media sites. These sites have also been instrumental in sharing information with a much wider audience and faster than could have been previously reached through nontechnology-related methods. One issue to watch for and test for is bias being included in data collected for a specified purpose. We must remain aware of the digital divide that separates those with access to the Internet from those who without—whether it’s due to being in a more remote location or lack of funds to pay for Internet service or devices. In addition, some governments monitor and block certain users and sites on the Internet, usually those critical of the country’s leadership.
Technological advances have also enabled easy and real-time collaboration to create documents. Having datasets online and accessible to the public helps share information and provides everyone with the ability to search, or “mine,” it for trends and patterns. This could lead to the identification of new issues and opportunities and advances in a variety of fields, including medicine, entertainment, sports, and business.
The use of “citizen scientists” to aid in research and storing or processing digital data is an example of crowdsourcing. Citizen scientists are useful to research teams that have limited time, funding, or members to collect the wide variety or volume of data needed for better analysis and problem-solving.
Plagiarism is easy to commit using the Internet by copying and pasting information without citing the owner of the information. However, it is equally easy to test for plagiarism. Always cite your sources for work and ideas that are not your own. The development of the Creative Commons licensing levels helps people share their creations and allow their reuse for specific uses with a wider audience. The tracking of their use and enforcement can be difficult and leads to issues about intellectual property and copyright. Illegal sharing of digital files is one of the downsides of new technologies and is usually done through peer-to-peer networks. Open-source software and open access to research and other data are legitimate ways to access other people’s work.
The unauthorized use or sharing of our personal data is also a major concern that impacts all of us. Combining data to remove the ability to identify an individual’s personal data will remain a concern since it is dependent on the abilities of the person or team doing the aggregating to fully understand and implement a complete masking process. Similarly, the tracking of people through their apps, photos, and browsing history is a privacy and security concern. Tied in with this, advertisers use targeted ads based on places we go and sites we visit. People often willingly provide this PII to receive benefits such as discount coupons.
Cybersecurity has become a critical field since the Internet was not designed to be a secure system. While antivirus software and firewalls can prevent many types of malware, hackers often trick people into clicking on unsafe sites or documents using phishing techniques. Hackers also use keyloggers to attempt to gain unauthorized access and create malware to spread viruses and worms. Multifactor authentication uses a variety of ways, including strong passwords, codes sent to a secure device or account, or use of a unique feature such as a fingerprint, to verify that you are the person trying to access your account. Cryptography is a field that deals with ensuring that data is secured via encryption methods before being transmitted across the Internet.
The current technique is public key encryption, which uses an asymmetric system, meaning one key is used to encrypt data and another is used to decrypt it. The key is divided into a public and a private part. The public keys are openly published and available to anyone. The algorithm uses the public key to encrypt, and the receiver decrypts with their private part of the key. This makes it impossible to decrypt because it takes too much memory or time to process. As advances in computer processing power are made, this method may become possible to break, but for now, our data and financial transactions on the Internet are secure.
The Internet is based on a “trust” model, which means that Certificates of Authority (CAs) are issued that ensure the public keys shared by sites we want to do secure processing with are legitimate. If we are buying a product online, our web browsers can trust that the company site is the correct one based on their CA, and we can proceed with our credit card or other transaction.
All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2025 All site design rights belong to S.Y.A.