Digital Archaeology (2014)
14. Mobile Device Forensics
Mobile devices (cell phones in particular) are integral to today’s society and can be a crucial part of a forensic case. It is important to have an understanding of what challenges an investigator may face when it comes to mobile devices.
This chapter visits what types of data are stored on most cell phones and where this data can be found. It also reviews what types of tools there are to assist with cell phone forensics, whether they be hardware or software based. Demonstrating a few cell phone forensic tools, this chapter reviews acquisition and analysis of data. The chapter wraps up by looking at a few legal case studies where cell phones were pertinent to the investigation.
Due to the extremely wide variety of devices on the market and the differences in how these devices are acquired, this chapter provides only a review of the techniques for mobile device forensics. It will be less “hands-on,” as it is unlikely that the tools and devices will be available to the average reader.
Challenges of Mobile Device Forensics
There is no greater challenge to a digital investigator than mobile forensics. Mobile devices have much of the same capabilities as a fully functional computer system, such as gaming, photography, messaging, and the ability to send multimedia, but it fits in a pocket.
The ease of use of functionality that mobile applications provide allows for a treasure trove of data for an investigator, but mobile device forensics lacks the tools that are available for computer forensics, and the requirements are often more strenuous. Compare acquiring a Windows machine to a cell phone at a corporation.
The investigator may receive instruction to acquire a computer for forensics. Let’s assume the computer has been shut down or the requestor has properly ensured the machine stay “live” until told otherwise. After receiving the computer, the investigator would be able to do an acquisition using any court-recognized forensic tool (EnCase, iLook, Helix, etc.). If the computer has disk encryption software, the investigator would need the encryption key to decrypt the software or use a module device with a choice of acquisition software. The examiner then acquires the system. After these steps are complete, the investigator has an original copy of the computer that is “bagged and tagged” and a working copy of the computer in which to work from. Simple enough.
When it comes to mobile forensics, there are similar steps in acquisition and analysis, but these come with caveats when analyzing the device. Later we will review some of the steps needed to go through an acquisition of a mobile device, but here are a few things to ponder: What if the mobile device is issued by the company and password protected, but the suspect did not sign a waiver form to state that the mobile device could be analyzed at the company’s discretion? Even worse, what if it was a personal mobile device, but might have company data on it? These are simple questions, but the ramifications of these simple questions need to be addressed before attempting to even begin to examine a mobile device.
How Cell Phones Work
Understanding the process of how cell phones work will help you understand where data can be found during an investigation. Cell phones are full-duplex devices, which means two people can speak at the same time. A half-duplex device, such as a walkie-talkie or CB radio, allows only one person to speak at a time. And while half-duplex devices have an estimated communication distance of one to five miles, a cell phone user can speak to someone across the globe, as long as the battery stays alive. The magic that allows this distance for a cell phone user is cellular towers and a well-crafted network.
Cellular Towers
A major cell phone carrier receives a certain amount of frequencies to use. These frequencies are split up between the cells, which are usually ten square miles in area. Since both the cell phones and cell phone towers utilize a low bandwidth, the cell phone frequencies can be reutilized within a nonadjacent cell, causing no interference. Referring to Figure 14.1, a cell phone user in Cell One can be on the same frequency as that of a user in Cell Two, but not that of Cell Three.
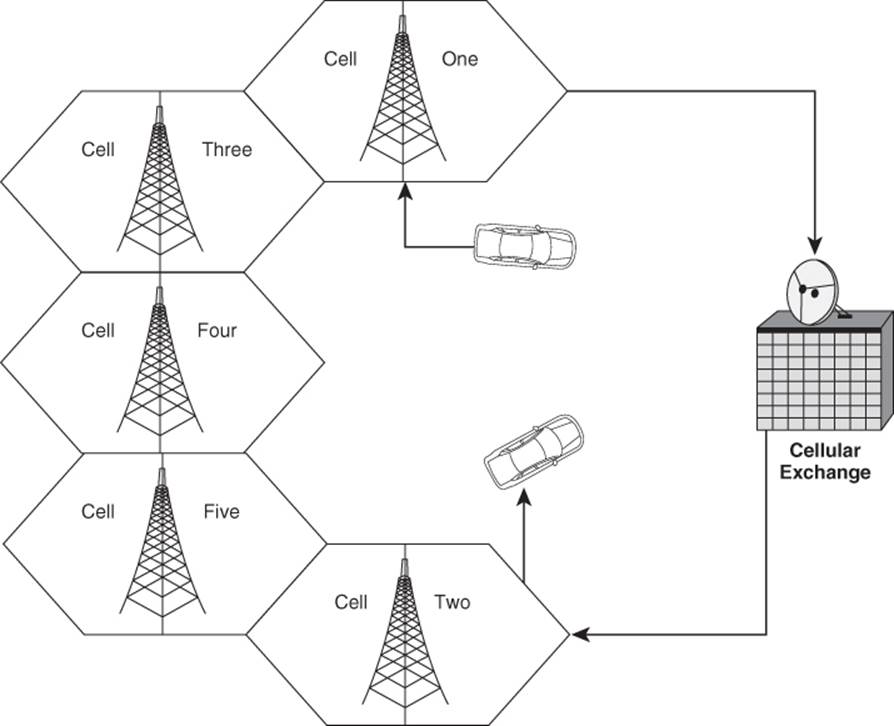
Figure 14.1 Cellular network layout
When a cell phone caller dials a person who is utilizing a landline, the process is simple. The cell phone call goes to the base tower, which is then sent to a receiver, which is then transmitted to a landline. Making a call to a cell phone from a cell phone is basically the same principle. The caller makes a cell phone call, which is picked up by the base tower closest to them, which goes to the receiver, to the landline system, and then to the receiver on the cell phone tower that is closest to the receiving cell phone. From there, the signal is transmitted to the tower and subsequently relayed to the target cell phone.
A cell phone call is held by the tower closest to the person making a call (the closer to the tower, the stronger the signal). As the caller moves out of range, the signal deteriorates, and the next closest tower, which provided a weaker signal at the onset of the call, becomes the strongest and picks up the call as a “hand-off.”
The Base Transceiver Station is the radio transceiver that communicates with the phones. The Base Station Controller manages the transceiver equipment and performs channel assignment. The Mobile Switching Center (MSC) is the switching system for the network. It manages communication in the network and interfaces with the public switch phone network.
The MSC should be one of the main focal points of a digital investigator. The MSC has databases that allow it to process data over the network. These databases are the Home Location Register (HLR) and the Visitor Location Register (VLR).
The HLR is a key database for subscriber data and service information, while the VLR is a database for mobile phones roaming outside of their service area. These databases provide account information, such as data about the subscriber (e.g., billing address), subscribed services, and the location update last registered with the network. This data is maintained in the HLR and used by the MSC to route calls and messages and to generate usage records called call detail records.
Cellular Networks
There are multiple types of mobile phone networks, but we’ll only review the three most important types: Code Division Multiple Access (CDMA), Time Division Multiple Access (TDMA), and Global System for Mobile Communications (GSM; GSMA 2012). Other types of networks include Advanced Mobile Phone System (AMPS), Integrated Digital Enhanced Network (iDEN), and Universal Mobile Telecommunications System (UMTS).
CDMA is a technology designed by Qualcomm that transmits multiple signals spread across an entire bandwidth. As each signal reaches its destination, it gets decoded at the receiving end. The key part to CDMA is that it shares bandwidth with other CDMA users, utilizing a shared frequency spectrum, but it is based on a code. Instead of focusing on different frequencies, CDMA focuses on these codes to distinguish between stations, or users. The receiving tower knows what one mobile user’s code and channel is and can differentiate between other mobile users. It is the same concept as “the cocktail effect.” While at a social gathering, there are many people speaking all at once. Instead of missing your conversation from all the others occurring at the same time, you know which conversation to listen for, just like the base tower receiver would.
TDMA is very similar to CDMA in that it utilizes a spectrum sharing technology, but it is based on time. The spectrum is broken into three time slots, which allow multiple users to communicate without interruption. Utilizing the example from before, there would be one person speaking at the cocktail party at a time. They would then stop to allow another person to speak, and so on.
TDMA technology is incorporated into the more advanced GSM technology. GSM is currently the world’s most widely used technology. One of the reasons for this popularity is that GSM network sharing essentially eradicates most roaming for cell phone users. Another huge advantage for GSM is that the mobile devices utilize a SIM card, which we will discuss later in the chapter.
Triangulation (Trilateration)
Thanks to the Pythagorean theorem, a cell phone can be triangulated in close proximity using cell tower triangulation, or it can be located using a more focused approach like GPS. The Global Positioning System (GPS) is used to track cell phone locations, and most current models have built-in GPS capability. According to the National Coordination Office for Space-Based Positioning, Navigation, and Timing (2012), there are 31 operational GPS satellites, of which 24 are assured to be activated at any given time.
To locate a cell phone’s exact location, GPS communicates with three satellites near the phone’s position, which is determined by the cell phone’s GPS receiver. The satellites form three circles, and where they intersect is where the phone is located.
A cell phone is triangulated by cell phone towers, rather than satellites (Cloudetal 2011). Just as satellites can triangulate a mobile device, three cell phone towers communicate with a cell phone to determine its location. The first tower calculates the distance to the phone using the strength of the signal. We can draw a circle along which the phone can exist anywhere along the periphery (Figure 14.2). With the first tower, we estimate the distance from the tower to the cell phone at one mile.
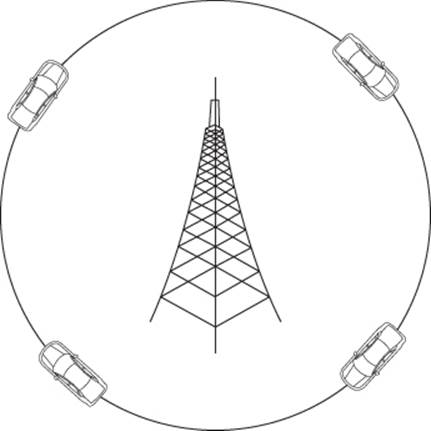
Figure 14.2 Triangulation distance (1 mile)
A second tower calculates distance on the basis of signal strength and comes up with a distance of one and a half miles. Where the distances overlap between the first and second towers, we have a likely position for the cell phone. This narrows the position of the cell phone down to two possible locations (Figure 14.3).
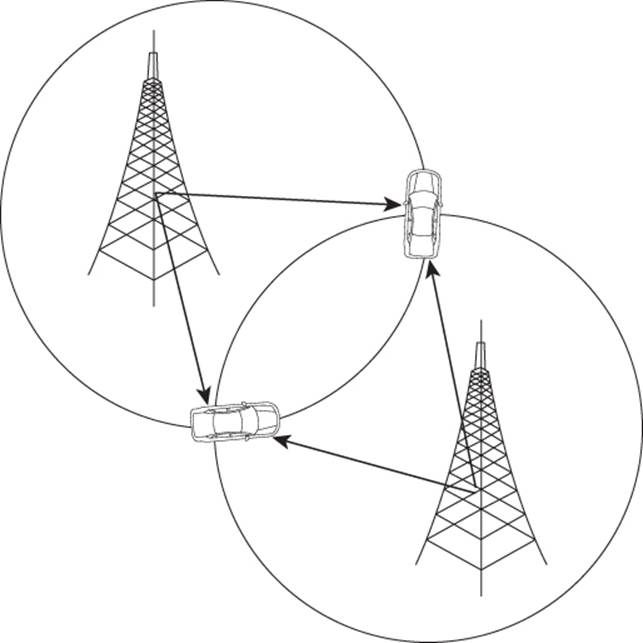
Figure 14.3 Triangulation distance with a second tower (1.5 miles)
Now a third tower is used to calculate distance. This time the signal strength tells the towers the cell phone is 1.7 miles away. The circle for the third tower is drawn and the location is locked down (Figure 14.4).
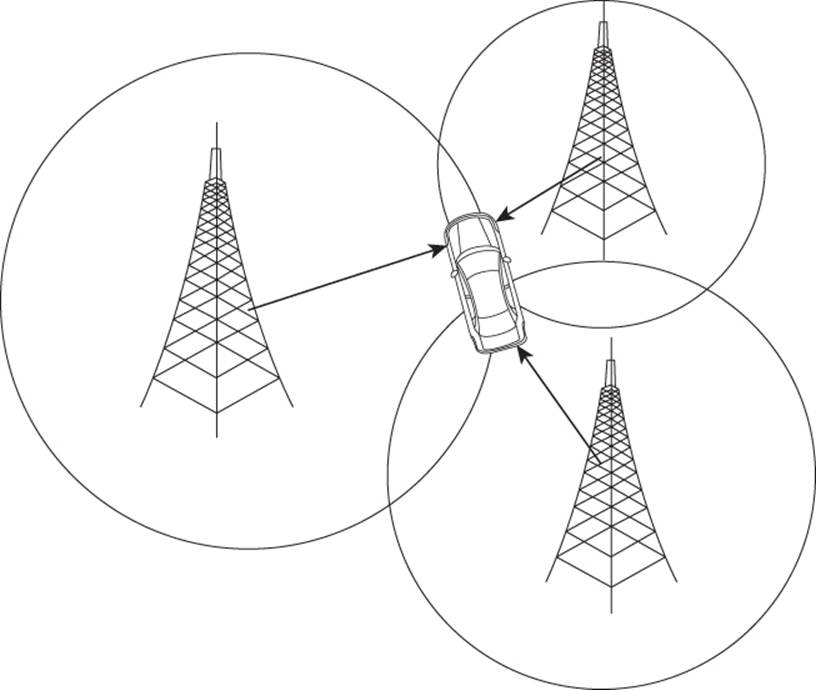
Figure 14.4 Triangulation distance with a third tower (1.7 miles)
When a tower sends a ping to a cell phone, the distance can be calculated by the lag time it takes to get a ping back from the cell phone. This is similar to how bats use echoes to determine their distance from nearby objects.
Data Storage on Cell Phones
There is a plethora of data that can be found on a mobile device, but you have to know where to look. The phone could contain pieces of physical hardware that retain this data, and not knowing the internals could cause future problems. The investigator must understand that there is pertinent data in identification numbers that may or may not be easily seen inside the phone, and there are data chips that allow network communications to occur. We’ll go over some of the more important data areas, but the investigator should obtain all information about a particular mobile device by searching the manufacturer’s Web site.
Memory
The Subscriber Identity Module (SIM) card is very important to understand as it not only stores vital information about the cell phone, the user, and some pertinent data but also encrypts transmissions and identifies the cell phone to the network (Kayne 2012). About the only thing a cell phone can do without a SIM card is make 911 calls. This should be noted, as it will come into play if you acquire a SIMless cell phone with forensic tools.
Most cell phones use either mini-SIM cards, which are 25 mm by 15 mm (0.98 in by 0.59 in), or micro-SIM cards, which are even smaller at 15 mm by 12 mm (0.59 in by 0.47 in) (Figure 14.5). The SIM card sits underneath most batteries on mobile devices that operate on GSM.

Figure 14.5 SIM card
Some of the information that is stored on a SIM card is the user’s cell phone number, Simple Message Service (SMS) texts, and address book. What is unique about this technology is that a user can take the SIM card out and put it into another device, thereby transferring most of the phone’s data as well as the service of the carrier. The app data on that mobile device does not transfer, so unfortunately, Angry Birds does not automatically port over to the new phone.
What is very important to a digital forensic investigator is the personal identification number (PIN). Once a PIN is input into the device, it will lock the SIM card so that no one will be able to utilize the phone or get data from it without knowing the PIN. There is also a pin unlock key (PUK) that is used in GSM devices. The PUK becomes important to an individual who is unsuccessful at entering the PIN after three consecutive tries. Once three unsuccessful tries are attempted, the SIM card will lock and will require the service provider to provide the PUK to unlock the SIM card. The service provider will ask for the Integrated Circuit Chip Identifier (ICCID) located on the SIM for verification before it provides the PUK.
It is critical to know that if an individual attempts ten unsuccessful tries at unlocking a PIN, one of two things will happen: The SIM becomes permanently blocked, or if the device is corporate owned and managed by an enterprise server, the cell phone might be configured to be overwritten. It should also be noted that within the cellular configuration settings, an automatic wipe after ten attempts can be set by the owner.
While the SIM has some storage capability (128KB in some instances), it is not the only storage on a cell phone. There is both read-only memory (ROM) and random access memory (RAM). The ROM will hold the operating system (OS) of the device, while the RAM is volatile and can disappear without proper power. Just as in traditional computer forensics, if the investigator wants to acquire the memory of the operating system, it is best that the system have a power source. This can be a major issue with cell phones because there are many types and many different power requirements to contend with.
While this chapter will not go into great detail about operating systems on cell phones, be aware that the OS in ROM that an investigator would expect may not be the one that is there. For example, just because a cell phone appears to be a Droid does not mean it will be configured with an Android OS. This is because an OS can be replaced on a cell phone.
Device Info
Not only can the SIM and ICCID number be found printed on the cell phone label, but there is other useful information about the phone as well. There is both the electronic serial number (ESN) and the mobile equipment identifier (MEID), and the International Mobile Equipment Identity (IMEI). The ESN and MEID numbers are specific to each CDMA phone, and they are the unique identifiers to the CDMA network. The IMEI number is specific to GSM phones. These numbers can be thought of as a mobile device’s “social security” number.
The ESN of a cell phone is a unique number that is used by the switching office to check the validity of the call (Mobiledia 2012). An MEID holds the same functionality as does an ESN for identifying the cell phone to the CDMA network, but it doesn’t have the limitations of ESN. In 2005, there was a shortage of ESN numbers because ESN is based on 32 bits, with only 4 billion unique numbers. The MEID utilizes 56 bits, and that gives millions of times as many unique numbers as ESN.
Another way to retrieve the MEID is to key in *#06# on the mobile device. If the device is a Motorola phone, the MEID can be retrieved by the sequence #, *, Menu, and then the right arrow key. If the mobile device is an iPhone, just go to Settings, General, and About. The MEID is a hexadecimal number and can be readily found by viewing the first digits that begin with A–F.
IMEI is similar to the MEID number in that it will identify the mobile device to the network. This number can be utilized to have the device blocked should it be lost or stolen. This number is printed in the battery compartment (Figure 14.6).

Figure 14.6 IMEI number
The IMEI number has a total of 15 numeric digits and has a few different purposes. The first eight digits are the Type Allocation Code (TAC). These numbers indicate the phone’s model and where it was made. The next sequence of six digits is the serial number of the device. The last digit is the checksum number.
Before moving on to discuss forensic methodology of acquiring cell phones, it goes without saying that that all information that is found on a device label can be tampered with. A nefarious individual can remove the label, alter it with a permanent marker, or just scratch the information off the phone, making it hard to find the correct information.
There are many other ways to find out what the device is or to whom it belongs. Just as with computer forensics, an investigator has to utilize all tools available and search for information. Some of the information can be retrieved by looking at the power cord of the device, which may be specific to a particular model of a phone. An obvious search around the general area may reveal other peripherals that attach to the device, including computer systems that can be forensically searched. As a last resort, utilizing the cell phone’s number in a reverse-lookup on the internet may reveal the owner.
Acquisition and Storage
During acquisition of the cell phone (if powered on), the investigator must notate the phone’s date and time while being able to compare that time to another clock. The USNO navy clock is an accurate option (http://tycho.usno.navy.mil/).
It is also suggested that the investigator take notes on all device information available that is easily viewable while it is powered on. If the device is powered off, then the phone’s battery source can be removed to view all device info.
While there are multiple tools, both free and off-the-shelf products, this chapter focuses on products that can be purchased. The main reason we focus on these off-the-shelf products is that they have been tested, and there is no need to go through a full-blown validation process (although in-house testing is still recommended). The risk of having evidence declared inadmissible by the court might possibly be increased by utilizing free tools if the evidence cannot be validated. The standards of evidence authentication defined in Daubert v. Merrel Dow Pharmaceuticals (1933) most certainly apply to evidence extracted from mobile devices.
Hardware
One advantage we now have as investigators is the plethora of hardware-based tools available for mobile device acquisitions. One of the challenges is keeping the phone from being able to communicate over the mobile network during the investigation. After a mobile device is seized in a search incident to arrest (SITA), if it is powered on and communicating on the mobile network, there exists the possibility that it might be remotely tampered with or even wiped. There are many signal-jamming hardware devices available, and we review a few more popular devices.
Faraday Enclosures
As can be ascertained, the Faraday name is relational to keeping unwanted signals, or interference, out of an enclosure (Faraday Cage 2012). The Faraday bag, which is a radio frequency isolation device, is very similar in design to that of a freezer bag, but much more secure (Figure 14.7). One aspect of the Faraday bag that cannot be viewed in Figure 14.7 is that there are two sealing strips to ensure the bag completely prohibits communication.

Figure 14.7 Paraben’s Faraday bag
It is important to note that the incident responder that secures the mobile device should ensure that there is a power source to attach to the mobile phone before putting it in a Faraday bag. The reason for this overzealous behavior is that with the mobile device powered on, it will continue to attempt to communicate with the cell towers. If the mobile device is powered on and does not have a battery pack connected to it, if it has no possible connection, the battery will drain much quicker than a phone that can communicate with a cell tower.
While having a Faraday bag is nice, it will not guarantee that the device will not make communication with a cell tower if there is any opening on the bag. A good example of this is when the mobile device is examined. If the investigator opens the bag ever so slightly to connect a data cable to the mobile device, then the cable can act as a strong antenna.
Prior to inserting the mobile device into a Faraday bag, the incident responder can put a portable charging device on the mobile phone. There are multiple instant charging devices available like Cellboost, Turbocharge, and Energizer. The premise behind these chargers is to give emergency power to the mobile user (incident responder) prior to the mobile device losing all of its charge. These instant charging devices are very similar to plugging the device into an AC outlet, but the phone works on more of an emergency mode.
The way to get around the dilemma of not being able to do analysis work on the mobile device securely is by utilizing a Faraday pouch or a Faraday box. Paraben’s StrongHold Pouch is one device that an investigator can utilize. Using this pouch, the investigator first inserts the powered-on mobile device into the secure enclosure. The investigator then inserts the mobile device’s data cable, which then connects to a shielded data connector inside the pouch. There is a connection on the back of the pouch that allows the investigator to connect the mobile device to a computer system.
Should the incident responder team need an enclosure that prohibits network signals and can hold multiple personnel, the next logical device would be a Faraday tent. This tent is very similar in concept to either a Faraday bag or a pouch; it is just more grandeur in scale. As working in these enclosures can become extremely hot, some of these tents include signal shielding for ventilation. What is practical about these signal enclosures is that they are portable and come in a variety of sizes. Some of them come in either single- or dual-layer protection.
Changing Phone Settings to Block Communication
While it is almost always a bad idea for an investigator to change any settings on a mobile device they are examining, sometimes utilizing the operating system to perform forensic work may be a necessary evil. However, if any changes are made to a suspect device (mobile or otherwise), the investigator must document in great detail every step taken.
Setting a phone to airplane mode is one way to keep the device from communicating with the network. This setting prohibits the sending or receiving of text messages, e-mails, and phone calls and was intended to prevent communication during flight. This setting is common on most cell phones today.
Again, extreme care should be taken when making any device setting changes, and they need to be notated.
Screen Capture Devices
Screen capture devices document an investigator’s every move. They can be very handy at times, especially when there is a need for a video log of all activities that are completed on a mobile device. There are multiple providers of screen capture devices. Two of these are Paraben’s Project-A-Phone and the Eclipse screen capture device.
It is best if these pieces of hardware are used within a Faraday enclosure. If that is not possible, on a GSM phone, the investigator will need to determine whether to remove a SIM card so that no data transmission to the cell network occurs.
As stated earlier, when doing work with digital forensics there is a need to have extremely well-written notes to depict what work was done and how it was completed. Phone projection devices satisfy those requirements. These devices create case files, hash the video file, and also allow case notes to be added during examination into the software.
Image Extraction Devices
Cellebrite has proven to be one of the more popular mobile forensic companies around, providing products that focus on acquiring physical (bitwise) as well as logical images. Two of the flagship products that Cellebrite has to offer are the ever-popular Universal Forensic Extraction Device (UFED) and the Chinex device. Both devices also have the ability to obtain deleted data because of their physical extraction abilities.
The UFED device works on more than 1,600 different mobile devices. It captures all available mobile data (address book, SMS messages, pictures, videos, and call logs). The mobile device connects to the UFED by one of multiple available data cables, Bluetooth, or infrared. Once the device is recognized by the UFED, the investigator has the choice of which data retrieval options to pursue. Extracted data can be stored on an SD Card, a USB storage device, or the investigator’s computer.
One of the more prominent features of the UFED device is that it has the ability to clone SIM cards. This is a very useful feature for an investigator when there is no SIM card present in the phone or when the examiner does not want the mobile device to communicate with the GSM cell network.
As discussed earlier in the chapter, another problem investigators experience in the field is a locked PIN on a mobile device they are examining. With UFED, the investigator can choose to extract a password instead of extracting phone data, cloning the SIM card, or using any other UFED feature. It must be noted that there is a completely different process that an investigator would go through when extracting passwords from a cell phone. After choosing the Extract Passcode option and continuing through the UFED menu for the type of device being worked on, the investigator can determine if the passcode is extracted to a USB device, SD Card, PC, or Display. The display option allows the investigator to view the passcode on the UFED device.
The Chinex device is an add-on device that plugs into the UFED. Like the UFED device, Chinex is geared toward the extraction of physical and logical images, but it is centered on Chinese chipset (MTK and Spreadtrum)-based devices. The Chinex device can perform extractions on thousands of different mobile devices.
Software
After the investigator has extracted the data, it can be viewed in reporting software. Reporting software has many different analysis features built in, including viewing the data in hexadecimal mode. The report view contains information about the acquisition from the mobile device, along with MD5 hashes of the data. For example, it would indicate whether the picture that was captured from the mobile device has a hash value associated with that specific file.
There are many different mobile device software tools available to an examiner, like Paraben’s mobile Device Seizure or BlackLight from BlackBag technologies, and they all perform different functions. Some investigative software is great for e-mail extraction, while another tool may be best suited for registry pulls. The focus of investigators when purchasing software is having a good idea of what mobile devices they will likely encounter during their investigation.
Removing Moisture from a Cell Phone
There have been numerous cases in which a suspect threw a mobile device into a body of water to destroy evidence. The iPhone has four water indicators on the inside of the phone that turn pink if the device is submerged in water (The Full Signal 2012).
When an investigator discovers that a phone has been in water, the number one priority is to ensure the device does not stay powered on; unless, of course, there is a need for that risk. There is a Save-A-Phone product sold by Paraben that absorbs moisture from a mobile device, allowing for a safer power-up. Another option would be to set the mobile device in a bag of salt, allowing the salt to absorb the moisture. Another method that works is putting the phone in a sandwich bag that has packets of silica gel inside. In all cases it is recommended that the investigator allow the phone to dry for 3 to 5 days. Afterward, the investigator should examine the phone for any moisture that could be hidden, before turning on the device.
Legal Aspects of Mobile Device Forensics
Cell phone technology has posed some interesting problems for the courts as well as the investigator. Courts have had a difficult time establishing precedents for a variety of questions regarding the legality of evidence extracted from cell phones. Legal issues include
• The legality of the search
• The integrity of the evidence extracted
• The validity of the evidence extracted
• The relevance of the evidence extracted
Because so much information can be stored in a cell phone, investigators frequently look at the device as a gold mine filled with smoking guns. As we’ve seen, the contents of a cell phone can include photographs, deleted text messages, GPS information showing where the device has been, contact information, and call logs. The issue the courts have had to face is when it is legal to search a phone and whether certain evidence stored on the phone might be considered either protected or exempt. Just as an example, Newitz (2007) pointed out that Mobile Phone Manager had been used by law enforcement agencies nationwide to collect cell phone evidence for two years before the developers (Oxygen Forensic) released a version that generated hash values of data images before and after capture. Before that, it was a crapshoot whether the data captured could be considered “tamperproof.”
The Legality of a Cell Phone Search
Search and seizure laws regarding cell phones differ in whether the target of the search is protected by the Constitution or by regulatory law. Any time law enforcement or a government agency is involved, the constitutional rights of the person being searched come into play. In situations involving civil law, the legal issues can become more convoluted and might be governed by any one (or more) of several different privacy laws.
Legal Issues Facing Law Enforcement
Early case law involving cell phones was directly impacted by a court decision handed down not too long before mobile telephones became commonly available to the public. In The United States v. Ortiz (1996), the Seventh Federal Circuit ruled that law enforcement could legally search a person’s pager. The assumption guiding the decision was that any new pages issued from the time of the incident to the moment at which a warrant could be obtained could potentially overwrite valuable evidence.
Cell phones are considered the property of the person in possession until proven otherwise. As such, a random search or seizure of the device would constitute a breach of the owner’s Fourth Amendment rights. Two situations exist that can allow a judge to deem evidence obtained by law enforcement without a warrant to be admissible. These are the incident to search and the exigent circumstances exceptions. There is a history of the courts generally accepting both of these exceptions in criminal cases.
U.S. v. Finley (2007) decided in favor of the government regarding the right of law enforcement to search a cell phone seized at the time of the arrest. (This same case will be examined later in this chapter regarding the rights of a private individual when using a corporate telephone.) In this incident, the cell phone of the suspect was removed from his possession at the time of arrest and incriminating evidence was found. The key point in this decision was that the cell phone was in his possession and within his reach.
An exigent circumstances exception is likely to be granted whenever law enforcement can demonstrate that there is a strong likelihood that a crime is in the process of being committed or that safety to life and limb is at risk. However, the argument that critical evidence is at risk of being destroyed if the device remained in the possession of the suspect may not always hold water. There has been a leaning toward citing U.S. v. Salgado (1986) in recent cases. In this decision, Judge William Campbell wrote, “A mere possibility that evidence will be destroyed—a possibility that exists any time a drug dealer is arrested outside of his home or other place of (illicit) business—is not enough. Otherwise the requirement of a warrant would have little meaning in the investigation of drug crimes.” This suggests that other mitigating conditions must support a search and seizure based on exigent circumstances.
In the case of Salgado, the conviction was upheld because the government could demonstrate that there was a near certainty that evidence would be destroyed. Conversely, in U.S. v. Young (2006), the decision read, “This Court finds that exigent circumstances existed because the evidence could be lost if not retrieved immediately without the benefit of a search warrant.” Such contradictory messages from the court are precisely why legal counsel should be involved in all searches. To be safe, always assume that a warrant is needed.
Legal Issues in Civil Cases
Think back to a comment I made in the previous section. A cell phone is considered to be the property of the person in possession until proven otherwise. This can have a direct impact on civil litigation as well. A person who is assigned a company-issued cell phone is the person in possession, but not necessarily the legal owner. Somehow the rights of the individual must be balanced by the rights of the owner. Generally speaking, in the presence of an official company policy regarding cell phone usage, the policy dictates what rights the user has. If the policy states that the company reserves the right to monitor or search the phone, then the individual would have an uphill battle in pursuing claims in the event of a search.
In City of Ontario, California v. Quon (2008), the issue revolved around a mobile phone issued to an employee for official use. When Quon became the target of an internal investigation involving sexually explicit messages being transmitted from his phone, the city confiscated and searched his phone. He argued that since the city was a government entity, he was protected by the Fourth Amendment and that even though he did not own the phone, a warrant was required to seize it. The Supreme Court disagreed. Since this was a government related case, how does this relate to civil issues?
It boils down to a statement made by Justice Scalia in the decision O’Connor v. Ortega, 480 U.S. 709: “Government searches to retrieve work-related materials or to investigate violations of workplace rules—searches of the sort that are regarded as reasonable and normal in the private employer context—do not violate the Fourth Amendment.”
The general interpretation of this rule is that if the company owns the cell phone, a search by the employer is legal. The secondary interpretation is that even when conducted by the government, a search within the context of the workplace, targeting workplace malfeasance, is acceptable.
Chapter Review
1. Explain triangulation and why it would be useful to law enforcement.
2. The PIN and the PUK are two different codes that are significant to the investigator. Explain what they are. How are they related? How are they different?
3. Why is it important to have a device such as a Faraday bag available when transporting cell phones as evidence?
4. Lacking a Faraday bag, what is another way to prevent the device from connecting to external devices (assuming the option is available on that particular phone)? What precautions must the investigator take before using this method?
5. Under what circumstances might it be considered acceptable to seize a cell phone without the benefit of a warrant?
Chapter Exercises
1. Look up U.S. v. Finley (2007) and review the decision. What mitigating circumstances led to the court deciding that the evidence obtained by government agents was admissible, in spite of the fact that no warrant had been obtained?
2. Go online and research at least two different companies that manufacture hardware designed for capturing cell phone data. Put together a short list of each one’s benefits and each one’s limitations. Choose one for your own use, and explain why you chose that particular model.
References
City of Ontario, CA v. Quon, 08-1332 (2010).
Cloudetal. 2011. Triangulation: Fun time with maths. www.cloudetal.com/triangulation-fun-time-with-maths (accessed May 29, 2012).
Daubert v. Merrell Dow Pharmaceuticals, Inc., 509 U.S. 579, 589 (1993).
Faraday Cage. 2012. Faraday cage. www.faradaycage.org/ (accessed June 2, 2012).
GSMA. 2012. GSM. www.gsma.com/aboutus/gsm-technology/gsm/ (accessed June 1, 2012).
Kayne, R. 2012. What is a SIM Card? www.wisegeek.com/what-is-a-sim-card.htm (accessed May 29, 2012).
Mobiledia. 2012. Electronic Serial Number (ESN). www.mobiledia.com/glossary/95.html (accessed May 29, 2012).
National Coordination Office for Space-Based Positioning, Navigation, and Timing. 2012. Official U.S. Government information about the Global Positioning System (GPS) and related topics. www.gps.gov/systems/gps/space/ (accessed Dec. 29, 2012).
Newitz, A. 2007. Courts cast wary eye on evidence gleaned from cell phones. Wired.com. www.wired.com/politics/law/news/2007/05/cellphone_forensics (accessed May 15, 2012).
The Full Signal. n.d. How to dry out a water-damaged iPhone. www.knowyourcell.com/apple/apple-iphone/iphone-guides/357471/how_to_dry_out_a_waterdamaged_iphone.html (accessed June 6, 2012).
U.S. v. Finley, 477 F.3d 250 (2007).
United States v. Ortiz, 84 F.3d 977 65 (1996).
United States v. Salgado, 807 F.2d 603 (1986).
United States v. Young, 2006 U.S. Dist. (2006).