Total Information Risk Management (2014)
PART 2 Total Information Risk Management Process
OUTLINE
Chapter 5 Overview of TIRM Process and Model
Chapter 6 TIRM Process Stage A
Chapter 7 TIRM Process Stage B
Chapter 8 TIRM Process Stage C
Chapter 9 Integrating the TIRM Process within the Organization
Chapter 10 TIRM Process Application Example
CHAPTER 5 Overview of TIRM Process and Model
Abstract
This chapter gives a brief overview of the stages of the TIRM process and explains the two continuous stages: communicate and consult and monitor and review. The TIRM model for quantifying information risk is introduced, which supports the information risk assessment of the TIRM process. It also shows how to determine the risk appetite of an organization.
Keywords
TIRM Process; Communicate and Consult; Monitor and Review
What you will learn in this chapter
![]() What is the TIRM process
What is the TIRM process
![]() What are the stages of the TIRM process
What are the stages of the TIRM process
![]() How to communicate and consult during information risk management
How to communicate and consult during information risk management
![]() How to monitor and review the TIRM process
How to monitor and review the TIRM process
![]() How to quantify information risks using the TIRM model
How to quantify information risks using the TIRM model
![]() How to determine the risk appetite of your organization
How to determine the risk appetite of your organization
Introduction
In this part of the book, we show ways to assess and treat information risk by following the Total Information Risk Management (TIRM) process. The TIRM process is a best-practice procedure for managing information risks. It contains the most important aspects that you need to consider to be successful in managing information risk. The process is explained in detail in the following commentary. The TIRM process can be divided into three stages:
A. Establish the context
B. Information risk assessment
C. Information risk treatment
This chapter provides a step-by-step guide on how to implement the TIRM process in your organization.
Every organization follows business processes, even if this often happens on a subconscious level. A business process has been defined as “a specific ordering of work activities across time and place, with a beginning, an end, and clearly identified inputs and outputs: a structure for action” (Davenport, 1993). An information risk management process is a management process that focuses on controlling and monitoring organizational risk that arises through data and information assets inside and outside an organization. Information is used in abundance in your business and it is hard to keep track of where it might cause risk. Luckily, we have gained a great deal of experience on how to manage information risks effectively through our work with a number of organizations in different sectors. We will share the experiences gained during our research at the University of Cambridge and provide you with guidance on how to assess and treat data risks effectively. In Chapter 3, we discussed why an information risk management process is probably the right way forward for your organization. In the next few chapters, we will show which steps should be followed in an information risk management process that we call the TIRM process.
The TIRM process is compliant with the widely accepted ISO 31000 risk management standard. This has the advantage of sharing the same risk terminology and concepts. For risk managers, many of the concepts should be well known and therefore easy to apply.
![]() IMPORTANT
IMPORTANT
The TIRM process aims to systematically manage risks arising from data and information assets of all possible types and sources—that is, external and internal, tacit and explicit, and structured and unstructured. It is based on the widely accepted ISO 31000 risk management standard.
![]() IMPORTANT
IMPORTANT
Information risk is the effect of uncertainty on an organization’s business objectives that arises from information quality.
What does the word total stand for in tirm?
We believe that you should consider all types of information used in all operational and management processes that are important to your business, no matter whether they are stored in:
![]() Databases
Databases
![]() Word-processed files
Word-processed files
![]() Slideshows
Slideshows
![]() Spreadsheets
Spreadsheets
![]() Videos
Videos
![]() Audio recordings
Audio recordings
![]() XML and HTML files
XML and HTML files
![]() Social networks
Social networks
![]() Twitter
Twitter
![]() Websites
Websites
![]() Paper hardcopies
Paper hardcopies
![]() Email
Email
![]() Mail
Mail
![]() Fax
Fax
![]() Telephone
Telephone
![]() Face-to-face communications
Face-to-face communications
The only condition is that the information that is considered in the TIRM process should be significant enough for your business (you have to determine for yourself what you consider significant information). Moreover, you should not limit your information risk management efforts to a single function or business process (although it might be a good starting point from which to extend to the whole organization). If something goes wrong in one of your core business processes it affects the rest of the business.
With the word total, we also emphasize that all core business processes have to be considered in the information risk management process, making TIRM an enterprise-wide program, rather than a local one. However, you may choose to begin implementation in a single defined area.
Stages of the TIRM process
The TIRM process consists of three main stages and two continuous activities that are executed throughout these stages, as illustrated in Figure 5.1.
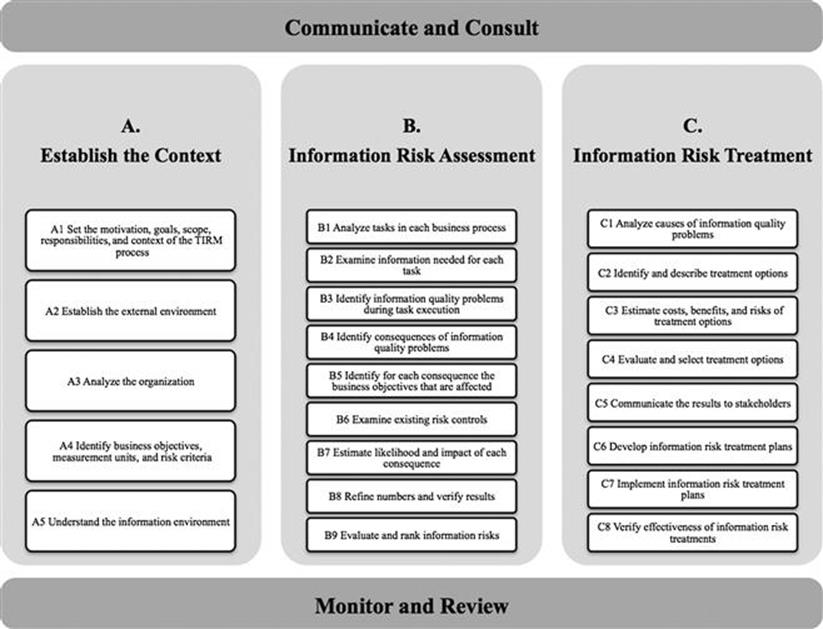
FIGURE 5.1 TIRM process.
When starting a TIRM initiative, the first thing that needs to be done is to establish the context—this is stage A. Every organization exists in different internal and external environments that are specific to it. To understand an information risk, establishing the organizational context is absolutely necessary. A major risk in one organization—for example, due to regulatory requirements, a particular competitive environment, or organizational culture—can be a low risk in another organization that operates in a different context.
Information risk is assessed in stage B. Information risks have to be identified and analyzed qualitatively and/or quantitatively and then evaluated. This is the heart of the TIRM process. In this stage, you will collect the inputs that are needed to model and quantify data and information risks.
In stage C, information risk treatment options have to be examined, selected, and implemented.
Communicate and consult is the basis of the process needed in all three stages. Without support of relevant stakeholders, your efforts are destined to fail. You also need senior management backing for the TIRM process.
The TIRM process should be constantly monitored and reviewed to verify and improve the effectiveness of the process and adapt it to the organizational context.
All stages and continuous activities are required for a successful TIRM initiative.
If you are already familiar with the ISO 31000 standard, you might have observed that the stages of the TIRM process do not differ much from the ISO 31000 risk management process stages. This is because the TIRM process is based on and refines the ISO 31000 risk management process for managing information risk, and therefore looks very similar to a general risk management process at a high level.
![]() IMPORTANT
IMPORTANT
There are three stages in the TIRM process that follow each other: The process starts with (A) establish the context, followed by (B) information risk assessment, and ends with (C) information risk treatment. There are two activities that are actually executed throughout the process: communicate and consult and monitor and review.
![]() ATTENTION
ATTENTION
All three stages of the TIRM process and the two continuous activities are required to successfully manage information risk.
Chapter 6 deals explicitly with establishing the context in stage A, Chapter 7 explains how to assess information risk in stage B, and Chapter 8 shows how a procedure for information risks can be treated in stage C.
The two continuous stages communicate and consult and monitor and review are discussed in the following sections. Moreover, we will explain how to determine the risk appetite of your organization.
Communicate and consult
An ongoing activity throughout the TIRM process that is absolutely essential for the success of the TIRM process is to communicate and consult with all relevant stakeholders. Relevant stakeholders can include personnel from the business function(s) involved, IT management, risk management, as well as senior executives. As the TIRM process crosses functional boundaries, it is a key requirement that senior management will be committed to the information risk management initiative. It is also important that the IT management and risk management executives are aware of and willing and able to support the initiative. The goals and benefits of the information risk management program need to be clearly communicated to all people involved in, or affected by, the TIRM process to gain active support.
To assess risk, information has to be gathered from across the whole organization. If it is not clearly and transparently communicated how information risk is assessed, people will not believe the figures and findings from the assessment, and it will be very hard to convince them to support information risk treatments that are required or beneficial. Communicating and consulting has to be done in parallel with all other stages.
![]() IMPORTANT
IMPORTANT
Not everyone appreciates the importance of information. You need to explain and demonstrate the business value of the information you are using.
![]() EXAMPLE
EXAMPLE
A senior executive is hostile and blocks your efforts to implement an information risk management program. You start to investigate and find out that a failed information governance program in the past has turned the senior executive into a strong opponent of any further initiatives related to information governance. The communication plan has to incorporate solid arguments that are communicated to this executive to convince him why the mistakes that occurred in the past will not be repeated once again.
Identifying information stakeholders
Information stakeholders are all people and groups of people who have a stake in the information that is managed or the management of information in the organization. The only exception would be if TIRM was applied to part of an organization. A list of all information stakeholders should preferably be created. New stakeholders might be added during other stages of the TIRM process.
Make a list of all stakeholders (using as a basis the one provided in Figure 5.2) that are relevant for your TIRM initiative. Investigate and document the attitude of each stakeholder group toward the initiative (e.g., supportive, enthusiastic, neutral, or opposed) and what you think might motivate their attitude, and draw up a plan that articulates how to effectively communicate matters to each of the stakeholders to best gain their support. Also, organize presentation and training sessions so that they are tailored to each specific group of stakeholders.
![]() ACTION TIP
ACTION TIP
Identify relevant participants and organize information and training sessions at the start, and run them during the TIRM initiative.
![]() ACTION TIP
ACTION TIP
Develop a communication plan: Who needs to be informed about what and at which stage? See Table 5.1, which can be used as a template.
Table 5.1
Information Stakeholders


FIGURE 5.2 Information stakeholders. (Source: English, 1999.)
Involve stakeholders in stage A
In stage A, a check needs to be made to identify whether the perceptions of the external and internal environment of the organization, the business objectives, and risk criteria are shared among key stakeholders.
Involve stakeholders in stage B
Stakeholders are involved during information risk assessment to get additional information and advice, and to ensure that everyone accepts the findings from this stage. In particular, the validity and plausibility of results from the information risk assessment stage should be validated with relevant stakeholders.
Involving stakeholders in stage C
During information risk treatment, it needs to be explained with care why particular options have been chosen or not chosen and why a particular way is selected in which to implement the option. A participative approach is of benefit here. Potential information risk treatment options should be discussed with all involved parties to better understand their weaknesses, risks and strengths, and to get support during implementation.
Monitor and review
Finally, the implementation of the TIRM process itself should be constantly improved based on the experiences gained during its application in your organization. Some problems can be more easily identified from an external perspective. By interviewing a wide range of stakeholders, the TIRM process can be better enhanced and improved.
The ISO 31000 risk management standard (ISO, 2009a, p. 20) highlights the purpose of monitoring and review:
![]() Ensuring that controls are effective and efficient in both design and operation.
Ensuring that controls are effective and efficient in both design and operation.
![]() Obtaining further information to improve risk management.
Obtaining further information to improve risk management.
![]() Analyzing and learning lessons from events (including near-misses), changes, trends, successes, and failures.
Analyzing and learning lessons from events (including near-misses), changes, trends, successes, and failures.
![]() Detecting changes in the external and internal context, including changes to risk and the risk itself, which can require revision of risk treatments and priorities.
Detecting changes in the external and internal context, including changes to risk and the risk itself, which can require revision of risk treatments and priorities.
![]() Identifying emerging risks.
Identifying emerging risks.
TIRM model: Quantifying information risk
In Chapter 3, we discussed, at a high level, how information risks are created. To be able to assess and quantify risks, an even more granular view is needed. We will now take a look “under the hood” by presenting a model to quantify information risks.
TIRM modeling symbols
We explain here the components of the TIRM model. In our experience, it helps to draw diagrams to visualize information risks. Therefore, we introduce TIRM modeling symbols to represent each of the constructs graphically.
Business process
The first construct is the business process, for which we use a (six-sided) hexagon (Figure 5.3).

FIGURE 5.3 Business process construct.
Task
A business process can consist of several tasks, which are represented as a circle (Figure 5.4).

FIGURE 5.4 Task construct.
Data and information assets
We represent a data and information asset with a star (Figure 5.5).

FIGURE 5.5 Data and information asset construct.
Information quality problem
We use a diamond for the information quality problem construct (Figure 5.6).

FIGURE 5.6 Information quality problem construct.
Consequence
We use a square to represent a consequence, no matter if it is a direct or an intermediate consequence (Figure 5.7).

FIGURE 5.7 Consequence construct.
Impact on business objective
We use the callout symbol to show that a consequence has an impact on one or more business objectives in our modeling (Figure 5.8).

FIGURE 5.8 Impact on business objective construct.
Putting it together: the TIRM model
Figure 5.9 shows how the components of the TIRM model are integrated and interlinked.
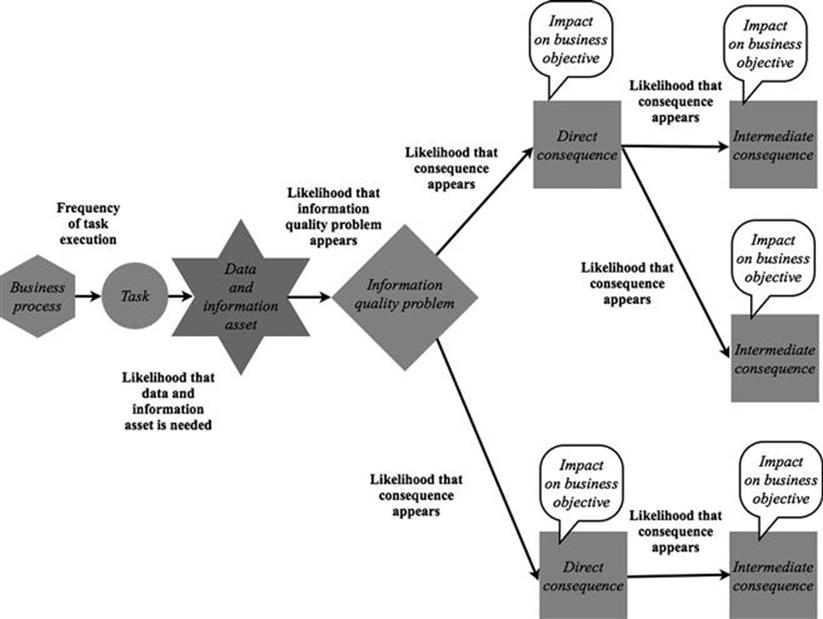
FIGURE 5.9 TIRM model.
Each business process contains any number of tasks that are carried out as part of that business process. To execute a task, data and information assets are required. Each piece of information may contain information quality problems, such as having missing entries (completeness of the data), which result in direct consequences. Further undesirable ramifications may result from the direct consequence, and each of these may still have any number of other, intermediate consequences. This, in turn, could adversely impact the achievement of a business objective.
There are also parameters that specify the link between the components in the model. The first parameter is the frequency of task execution, which is recorded for each task that is part of a business process, and is the number of times (e.g., per month) that the task is actually carried out. Each time the task is executed it may require different data and information assets, and therefore, the probability that the data and information asset is needed is recorded for each task–information pair. Furthermore, the specified information quality problem may not always appear in the particular subset of information used. For example, for a particular type of part, the information (asset) could list all of the suppliers without gaps, and therefore, the problem would not manifest itself in some cases. Therefore, the likelihood that the information quality problem appears in the information that is used for the task needs to be specified. In a similar manner, the likelihood that the problem leads to the direct consequence is recorded along with the likelihood that each consequence leads to other, intermediate, consequences. The last parameter is the severity of the impact in the impact on business objective component.
A demonstration of how risk totals can be calculated using the components and parameters of the TIRM model is given in Chapter 7 in TIRM process step B9.
Providing estimates for the TIRM model
Providing estimates for each of the parameters can be done in three different ways, as discussed in the “Providing Estimates” box. Option 1 is to estimate the expected mean value and will be used in our examples in Chapter 7 when we illustrate how the TIRM model can be put into action for information risk assessment. Options 2 and 3 require a Monte Carlo simulation to be run to calculate the risk totals, which is explained in detail in Chapter 11. A Monte Carlo simulation produces repeatedly random numbers of an estimated distribution to compute their results. If you want to use options 2 and 3, adequate software support is needed. A pilot software tool InfoRAS for the TIRM model that we developed to support the TIRM process is presented in Chapter 12.
PROVIDING ESTIMATES
There are three options to provide quantitative estimates as part of the TIRM process:
Option 1: Estimating the expected value. Often the expected value is not known accurately or is volatile. In these cases, option 2 or 3 can be more suitable.
Option 2: Estimating a lower and an upper boundary. There is a high likelihood that between these boundaries will be the real value. In this case, it is assumed that the expected value is equally distributed between the two boundaries (i.e., it is distributed uniformly). A slight possible variation to option 2 is that one assumes that the values are distributed normally between the two boundaries (i.e., a normal distribution is used in this case).
Option 3: Estimating the most likely value (mode) and a lower and upper boundary. The advantage of having these three estimates is that they can be used to calculate the so-called triangular distribution.
If the task is executed by somebody other than the business process representatives participating in the information risk assessment workshop, this information can be obtained by asking the person who usually executes the task. This can sometimes also be supplemented with data that documents the execution of the task, if it is available.
How the TIRM model is used as part of the TIRM process
The TIRM model is used to support the assessment and quantification of information risks in stage B of the TIRM process, which is presented in Chapter 7. The required parameters for the TIRM model will be gathered as part of the process steps in stage B. The risk totals can then be calculated for each information risk, which is explained and demonstrated in TIRM process step B9 in Chapter 7.
Determining risk appetite for TIRM
Before starting with the TIRM process, the risk appetite should be determined. Once the risk appetite has been determined, the organization will be on its way to establishing a robust TIRM process. The risk appetite will be needed to set up risk criteria in step A4 of the TIRM process. Providing clarity about tolerance levels and who is responsible will:
![]() Ensure that better-informed business decisions are made.
Ensure that better-informed business decisions are made.
![]() Provide clear communication channels, alerting senior levels of management to potential information risks at an early stage.
Provide clear communication channels, alerting senior levels of management to potential information risks at an early stage.
![]() Alleviate the possibility of being exposed to unmanageable information risks.
Alleviate the possibility of being exposed to unmanageable information risks.
![]() Allow the organization to prioritize actions in those areas where risk is deemed to exceed the defined appetite.
Allow the organization to prioritize actions in those areas where risk is deemed to exceed the defined appetite.
![]() Help to develop a culture where information risk awareness becomes embedded in day-to-day operations.
Help to develop a culture where information risk awareness becomes embedded in day-to-day operations.
![]() Establish the right balance between being bold and being cautious.
Establish the right balance between being bold and being cautious.
Risk appetite could be expressed on a scale—you can of course decide how to measure your risk appetite but you may wish to consider the following suggestion of a 1 to 4 scale, an example of which is shown in Table 5.2.
Table 5.2
Example Risk Appetite Scale
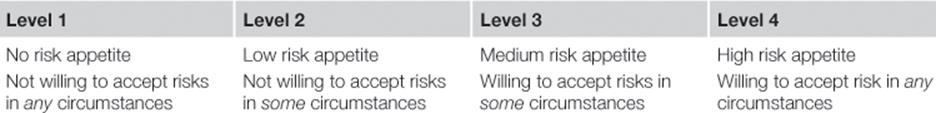
Communicating the tolerance level in this way should also be accompanied by guidance in terms of the discretion available. For example, who can take the decision to tolerate the risk? When does a decision need to be escalated to a higher level of management?
More tangible scales are set in the form of risk criteria for each business objective in step A4 during the establish the context stage.
Many experienced employees will have an intuitive feel for the risk level they may expose the organization to, but it is unwise to rely on this, and boundaries need to be established with clear guidelines put in place so that misunderstandings and bad risks are mitigated.
The level of risk appetite will vary; it will not remain static, not only in respect of specific issues but also over time.
![]() EXAMPLE
EXAMPLE
As an example, with speculative projects you may be prepared to tolerate a higher level of risk appetite than that for mission-critical projects. Over time, an activity or project that may have been deemed to be a level 1 risk in year 1 may become level 3 in year 3 as expertise in managing that specific situation is developed.
Summary
This chapter presented an overview of the TIRM process and generic aspects that need to be considered during all three stages of the TIRM process, such as communicating and consulting with stakeholders of the TIRM, monitoring and reviewing the TIRM process, and determining an organization’s risk appetite. We also presented a model for TIRM that will be used to assess and quantify information risks as part of stage B of the TIRM process. Chapter 6 presents stage A—establish the context—of the TIRM process.
References
1. Davenport L. Process Innovation: Reengineering Work Through Information Technology. Boston: Harvard Business School Press; 1993.
2. English LP. Improving Data Warehouse and Business Information Quality: Methods for Reducing Costs and Increasing Profits. New York: John Wiley and Sons; 1999.
3. International Organization for Standardization (ISO). ISO 31000:2009 Risk Management—Principles and Guidelines on Implementation. 2009; Available at http://www.iso.org/iso/catalogue_detail?csnumber=43170; 2009.