Computer Forensics: Investigating Network Intrusions and Cybercrime (CHFI) (2016)
8
Chapter
Investigating Corporate
Espionage
Objectives
After completing this chapter, you should be able to:
• Understand corporate espionage
• Describe the motives behind spying
• Understand the information that corporate spies seek
• Understand the causes of corporate espionage
• Describe spying techniques
• Defend against corporate spying
• Understand the tools used to fight against corporate espionage
Key Terms
Corporate espionage the use of spies to gather information about the activities of an
organization for commercial purposes
Honeypot a system that is attractive to an attacker and serves no other purpose than to keep
attackers out of critical systems and observe their attack methods
Honeytoken a file that an administrator places on a server that serves no other purpose than to attract the attention of an attacker
Netspionage network-enabled espionage, in which an attacker uses the Internet to perform
corporate espionage
Introduction to Investigating Corporate Espionage
This chapter focuses on the various aspects of corporate espionage and strategies to prevent and investigate such cases.
Espionage is the use of spies to gather information about the activities of an organization. Information gathered through espionage is generally confidential information that the source does not want to divulge or make public. The term corporate espionage is used to describe espionage for 8-1
8-2
Chapter 8
commercial purposes. Corporate espionage targets a public or private organization to determine its activities and to obtain market-sensitive information such as client lists, supplier agreements, personnel records, research documents, and prototype plans for a new product or service. This information, if leaked to competitors, can adversely affect the business and market competitiveness of the organization.
It is widely believed that corporate espionage is a high-tech crime committed by highly skilled persons. On the contrary, corporate penetration is accomplished with simple and preventable methods. Corporate spies do not depend on computer networks alone for information; they look for the easiest ways to gather information.
Even trash bins and scrap bits of papers can be of great help in collecting sensitive information. Spies look for areas that are generally ignored. For example, they take advantage of people’s negligence, such as forgetting to close doors or leaving scrap or waste paper around that contains sensitive information.
Market research and surveys show the severity of corporate espionage. According to the FBI and other similar market research organizations, U.S. companies lose anywhere from $24 billion to $100 billion annually due to industrial espionage and trade secret thefts, whereas technical vulnerabilities are responsible for just 20% or less of all losses.
Motives Behind Spying
The motives behind spying include the following:
• Financial gain: The main purpose of corporate espionage is financial gain. Any company’s trade secrets can be sold for millions of dollars. Competitors can use the stolen information to leverage their market position and obtain great financial benefits.
• Professional hostilities: Professional hostilities are also a result of market competition. Competitors often resort to negative publicity of an organization’s issues, which otherwise may have been kept secret and sorted out in time. There have been many instances when a rival company has disclosed secret information collected through corporate espionage of an organization, resulting in plummeting stocks and drastic decrease in market capitalization.
• Challenge and curiosity: People sometimes indulge in corporate espionage just for fun and to test their skills. Students of security programs and researchers often try to reenact corporate espionage. Though not disastrous, it compromises corporate information security.
• Personal relations: Many times, a corporate spy is motivated by personal or nonideological hostility toward the country or organization. Personal hostilities of disgruntled employees and job seekers toward an organization play a major role in almost all corporate espionage cases. The offenders reveal important, sensitive information to others out of spite.
Information That Corporate Spies Seek
The following are some of the types of information that corporate spies seek:
• Marketing and new product plans
• Source code of software applications: It can be used to develop a similar application by a competitor or to design a software attack to bring down the original application, thus causing financial losses to the original developer.
• Corporate strategies
• Target markets and prospect information
• Business methods
• Product designs, research, and costs: Huge investments will be in vain if the product design and related research is stolen, because the competitor can also develop the same product and offer it for less.
• Alliance and contract arrangements: delivery, pricing, and terms
• Customer and supplier information
• Staffing, operations, and wages or salaries
• Credit records or credit union account information
Techniques of Spying
8-3
All of the above information is considered crucial for the success of an organization. Information leaks could have catastrophic effects on organizations.
Corporate Espionage: Insider/Outsider Threat
Corporate espionage threats can be classified into the following two basic categories:
• Insiders: Insiders such as IT personnel, contractors, and other disgruntled employees who can be lured by monetary benefits are the main targets of corporate spies. An insider threat is always considered more potent than an outsider threat because insiders have legitimate access to the facilities, information, computers, and networks. According to the available study reports, almost 85% of espionage cases originate from within an organization. Insiders can easily misuse their privileges to leak sensitive information, and they can collaborate with an outsider. There are several factors that may prompt an insider to sell information to a competitor or spy, such as the following:
• Lack of loyalty
• Job dissatisfaction
• Boredom
• Mischief
• Money
• Outsiders: Outsiders include corporate spies and attackers who have been hired by a competing organization or are motivated by personal gain. These people try to intrude into an organization’s affairs for the purpose of stealing sensitive information. An outsider can enter a company through Internet connection lines, physical break-ins, or partner (vendor, customer, or reseller) networks of the organization.
Corporate Espionage Threat Due to Aggregation of Information
Espionage is a great threat to organizations that practice information aggregation, where all information concerning an organization is brought together and stored in one location. Both insiders and outsiders can easily access critical information because there is only one point of infiltration.
In an insider attack, insiders with access privileges can tamper with, edit, overwrite, or send critical information to the organization’s competitors. In an outsider attack, an outsider who breaks into the private network of an organization can search, aggregate, and relate all the organization’s critical information.
Techniques of Spying
The following are some common spying techniques:
• Hacking computers and networks: This is an illegal technique for obtaining trade secrets and information. Hacking involves gaining unauthorized access to computers and networks.
• Social engineering: Social engineering is the use of influence and the art of manipulation to gain credentials. Individuals at any level of business or communicative interaction can make use of this method. All the security measures that organizations adopt are in vain when employees get socially engineered by strangers. Some examples of social engineering include unwittingly answering the questions of strangers, replying to spam e-mail, and bragging to coworkers.
• Dumpster diving: Dumpster diving is searching for sensitive information in the following places at a target organization:
• Trash bins
• Printer trash bins
• User desks
• Whacking: Whacking is wireless hacking that is used to capture information passing through a wireless network.
• Phone eavesdropping: Phone eavesdropping is overhearing phone conversations while being physcially present.
8-4
Chapter 8
• Network leakage: Most organizations set up their network to block or limit inbound and outbound connections. Even organizations that are starting to filter outbound traffic still allow certain traffic out.
Two types of traffic that are always allowed out of an organization are Web and e-mail traffic.
• Cryptography: Cryptography is a technique to garble a message in such a way that the meaning of the message is changed. Cryptography starts with a plaintext message, which is a message in its original form. An encryption algorithm garbles a message, which creates ciphertext. A decryption algorithm can later take the ciphertext and convert it back to a plaintext message. During the encryption and decryption process, what protects the ciphertext and stops someone from inadvertently decrypting it back to the plaintext message is the key. Therefore, the secrecy of the ciphertext is based on the secrecy of the key and not the secrecy of the algorithm. Thus, to use an encryption program, a user has to generate a key. The key is often tied to a username and e-mail address. No validation is performed, so an attacker can put in bogus information that could be used later to launch a man-in-the-middle attack where the attacker can trick someone into using a false key. If someone knows the public key for a user, he or she can encrypt a message; but he or she can only decrypt the message if he or she knows the user’s private key. The public key can be distributed via a trusted channel, but a user’s private key should never be given out. If someone can get access to a user’s private key, he or she can decrypt and read all that user’s messages.
• Steganography: Steganography is data hiding and is meant to conceal the true meaning of a message.
With steganography, a user has no idea that someone is even sending a sensitive message because he or she is sending an overt message that completely conceals and hides the original covert message. Therefore, cryptography is often referred to as secret communication and steganography is referred to as covert communication. Insiders often use steganography to transmit credentials to other organizations.
Defense Against Corporate Spying
The following are some techniques that can secure the confidential data of a company from spies:
• Controlled access
• Encrypt the most critical data.
• Never store sensitive information on a networked computer.
• Classify the sensitivity of the data and thus categorize personnel access rights to read/write the information.
• Assign duties to personnel where their need-to-know controls should be defined.
• Ensure authorization and authentication to critical data.
• Install antivirus software and password-protect the secured system.
• Regularly change the password of confidential files.
• Separate duties.
• Background investigations of personnel
• Verify the background of new employees.
• Do not ignore physical security checks.
• Monitor employee behavior.
• Monitor systems used by employees.
• Disable remote access.
• Make sure that unnecessary account privileges are not allotted to normal users.
• Disable USB drives on employees’ systems.
• Enforce a security policy that addresses all employee concerns.
The following are the basic security measures to protect against corporate spying:
• Destroy all paper documents before trashing them. Secure all dumpsters and post
“NO TRESPASSING” signs.
• Regularly conduct security awareness training programs for all employees.
Steps to Prevent Corporate Espionage
8-5
• Place locks on computer cases to prevent hardware tampering.
• Lock the wire closets, server rooms, phone closets, and other sensitive equipment.
• Never leave a voice mail message or e-mail broadcast message that gives an exact business itinerary.
• Install electronic surveillance systems to detect physical intrusions.
Steps to Prevent Corporate Espionage
The following sections outline some steps that help in preventing corporate espionage.
Understand and Prioritize Critical Assets
An administrator needs to determine the criteria that are used to estimate value. Monetary worth, future benefit to the company, and competitive advantage are sample criteria that could be used. Whatever the criteria are, they need to be determined first.
After all assets are scored, the administrator needs to prioritize them based on the criteria. When the administrator is done, he or she should have a list of all the critical assets across the organization. These assets represent the crown jewels of the organization and need to be properly protected. Once the list of assets has been determined, the critical assets need to be protected. An administrator needs to understand the likely attack points and how an attacker would compromise each asset.
Define Acceptable Level of Loss
The possibility for loss is all around, and risk management becomes a driving factor in determining what an organization should focus its efforts on and what can be ignored. As difficult as it may seem for all critical assets, an adequate level of risk needs to be defined. This helps an organization to focus on what should or should not be done with regard to insider threats. Cost-benefit analysis is a typical method of determining the acceptable level of risk. The general premise behind cost-benefit analysis is determining what the cost is if the asset is lost in part or in whole, versus what the cost is to prevent that loss. While this is hard for some people to swallow, there are actually many situations where it is more cost effective to do nothing about the risk than to try to prevent or reduce the risk from occurring.
Typically, there are two methods to deal with potential loss: prevention and detection. Preventive measures are more expensive than detective measures. With a preventive measure, the organization stops the risk from occurring. With detective measures, the organization allows the loss to occur but detects it in a timely manner to reduce the time period in which the loss occurs. Defining an acceptable level of loss enables an organization to determine whether it should implement preventive or detective measures. If the organization’s acceptable level of loss is low, which means it has a low tolerance for a loss of a given asset, a preventive measure would be more appropriate to stop the loss. The organization would have to be willing to spend the extra money on appropriate preventive measures. If the organization’s acceptable level of loss is high, this means it has a higher tolerance and would most likely spend less money on a solution and implement detective measures. Now, the organization is allowing the loss to occur, but it is controlling and bounding it. Therefore, performing calcula-tions on acceptable level of loss plays a critical role in controlling insider threats.
Control Access
The best method for controlling insider threats is limiting and controlling access. In almost every situation in which an insider compromises, it is usually because someone had more access than he or she needed to do his or her job. There are usually other factors at play, but the number one factor is properly controlling access. For preventing insider attack, it is better to allocate someone the least amount of access that he or she needs to do his or her job. Encrypt the most critical data. Never store sensitive information on a networked computer; store confidential data on a standalone computer that has no connection to other computers and the telephone line.
Regularly change the password of confidential files.
Bait: Honeypots and Honeytokens
A honeypot is a system that is put on a network that has no legitimate function. It is set up to look attractive to attackers and keep them out of critical network systems. The key thing about a honeypot is that there is no legitimate use for it, so no one should be accessing it. If someone accesses the honeypot in any way, that person is automatically suspicious because the only way he or she could have found it is if he or she was wandering around 8-6
Chapter 8
the network looking for something of interest. If the attacker was only doing what he or she was supposed to, he or she would have never found the system.
Note that there are some legal ramifications to using honeypots. If the honeypot is used to protect critical systems and to observe attack methods to be able to better protect network systems, it is simply enticement to provide the attacker with a more attractive target. If, on the other hand, the intent is to lure or trick the attacker into attacking the system so an administrator can catch and prosecute the attacker, it could be considered en-trapment, which is illegal.
A honeytoken works the same way as a honeypot, but instead of an entire system, it is done at the directory or file level. An administrator puts an attractive file on a legitimate server and if anyone accesses it, the administrator catches the attacker with his or her hand in the cookie jar. This usually has a higher payoff. Insiders are good at figuring out a certain system or even a certain directory that contains critical intellectual property for a company. If an administrator adds an additional file to the system or directory, there is a chance that someone might stumble across it. Once again, since this is not a legitimate file, no one should be accessing it. There is no speculation involved if someone accesses the honeytoken file. That person is clearly up to no good since there is no reason anyone should be accessing it. Therefore, honeytokens can enable administrators to set up a virtual minefield on critical systems. If a person is a legitimate user and knows the files he or she is supposed to access, he or she can easily navigate the minefield and not set off any mines; however, if a user is an insider trying to cause harm, there is a good chance that he or she will be tempted by a honeytoken.
Detect Moles
With mole detection, an administrator gives a piece of data to a person and if that information makes it out to the public domain, the administrator knows the organization has a mole. If an administrator suspects that someone is a mole, he or she could “coincidentally” talk about something within earshot of the suspect. If the administrator hears the information being repeated somewhere else, he or she knows that person is the mole.
Mole detection is not technically sophisticated, but it can be useful in trying to figure out who is leaking information to the public or to another entity.
Perform Profiling
An ideal way to control and detect insiders is by understanding behavioral patterns. There are two general types of profiling that can be performed: individual and group. Individual profiling is related to a specific person and how he or she behaves. Every person is unique, so individual profiling learns the pattern of normality for a given individual, and if any behavior falls outside of that norm, that person is flagged. The advantage of this method is that it closely matches to an individual and is more customized to how a single individual acts. The problem is that it changes with the person, so if the attacker knows that individual profiling is being performed and makes slow, minor adjustments to his or her behavior, he or she could slip through the system.
Perform Monitoring
Monitoring is easy to do and provides a starting point for profiling. With monitoring, an administrator is just watching behavior. In order to profile a given person and flag exceptional behavior, the administrator has to establish a baseline. Therefore, in many cases, it is better to start with monitoring to see how bad the problem is and then move toward profiling if that is deemed necessary at a later point in time. Before an organization performs monitoring, it is critical that it does it in a legal and ethical manner. From a legality standpoint, it is critical that an organization determines whether information has an implied expectation of privacy.
The following are some of the different types of monitoring that an organization can perform:
• Application specific
• Problem specific
• Full monitoring
• Trend analysis
• Probationary
Analyze Signatures
Signature analysis is a basic but effective measure for controlling insider threats or any malicious activity. Signature analysis is also called pattern analysis because the administrator is looking for a pattern that is indicative of a problem or issue.
Investigating Corporate Espionage Cases
8-7
The problem with signatures is that an administrator must know about an attack in order to create a signature for it. The first time an attack occurs, it becomes successful because there is no signature. After it is successful and the administrator performs incident response and damage assessment, he or she can figure out how the attack occurred and can build an appropriate signature for the next time; however, if the next time the attacker attacks in a different manner, the signature might miss the attack again. This brings up two important points with regard to signatures. First, they will only catch known attacks; they will not catch zero-day attacks. A zero-day attack is a brand new attack that has not been publicized and is not well known. Second, signatures are rigid.
If an administrator has a signature for an attack and it occurs exactly the same way each time, he or she can detect it and flag it. However, if it is morphed or changed, there is a good chance the signature will no longer be effective. The last problem with signatures is that they take a default allow stance on security. A default stance blocks what is malicious, and anything else that falls through is flagged as good. By itself, signature detection says if there is bad behavior but there is no signature match, then the behavior must be good.
Key Findings from U.S. Secret Service and CERT Coordination
Center/SEI Study on Insider Threats
A U.S. Secret Service and CERT Coordination Center/SEI study revealed the following things concerning insider threats:
• A negative work-related event triggered most insiders’ actions.
• The most frequently reported motive was revenge.
• The majority of insiders planned their activities in advance.
• Remote access was used to carry out a majority of the attacks.
• Insiders exploited systematic vulnerabilities in applications, processes, and/or procedures, but relatively sophisticated attack tools were also employed.
• The majority of insiders compromised computer accounts, created unauthorized backdoor accounts, or used shared accounts in their attacks.
• The majority of attacks took place outside normal working hours.
• The majority of the insider attacks were only detected once there was a noticeable irregularity in the information system or a system became unavailable.
• The majority of attacks were accomplished using the company’s computer equipment.
• The insiders not only harmed individuals but also the organizations.
Netspionage
Netspionage is network-enabled espionage, in which an attacker uses the Internet to perform corporate espionage. Corporate espionage is an old practice, but the advent of the Internet has made it easier, faster, and much more anonymous. Netspionage enables spies to steal sensitive corporate information without physically entering the company’s premises.
Investigating Corporate Espionage Cases
The following are some steps an investigator should take when investigating corporate espionage cases: 1.
Check the possible points of physical intrusion: Before starting an investigation into a corporate espionage case, an investigator should scan all possible points of physical intrusion carefully. These points may provide clues about how the information might have leaked and can also provide fingerprints if anybody passed through. This information may be helpful when presenting the case before a court of law.
2.
Ch eck the CCTV records: An investigator should check all CCTV records for any unusual activity. This often leads to the real culprit.
3.
Check e-mails and attachments: An investigator should check all official e-mails and other e-mails with attachments used at the workplace. In many cases, the information is passed outside using e-mails. An investigator should thoroughly scan any suspicious e-mail and try to find out its destination.
8-8
Chapter 8
4.
Check systems for backdoors and Trojans: Disgruntled employees install backdoors and Trojans in their systems using their privileges as employees before quitting their jobs. So an investigator should scan all the systems and check for backdoors and Trojans. If any backdoor or Trojan is discovered, an investigator should trace its connections.
5.
Check system, firewall, switch, and router logs: Logs show each and every event taking place in a network.
An investigator should examine the logs of all network devices to detect suspicious activities, such as when and which data passed through the network and which kind of services and protocols were used.
6.
Screen the logs of network and employee monitoring tools, if any: If an administrator has installed any kind of employee monitoring tools on the organization’s systems, an investigator should analyze their reports. But before using any such monitoring tools, the investigator must take care of any legal aspects.
7.
Seek the help of law enforcement agencies, if required: An investigator should enlist the help of law enforcement agencies if it is necessary to track the culprit and bring him or her to trial.
Tool: Activity Monitor
Activity Monitor allows an administrator to track how, when, and what a network user did on any LAN. The system consists of server and client parts.
The following are some of the features of Activity Monitor:
• Remotely views desktops
• Monitors Internet usage
• Monitors software usage
• Records activity log for all workplaces on a local or shared network location. Log files include typed keystrokes, records of switching between programs with time stamps, application path, and window names, visited Web sites, and more.
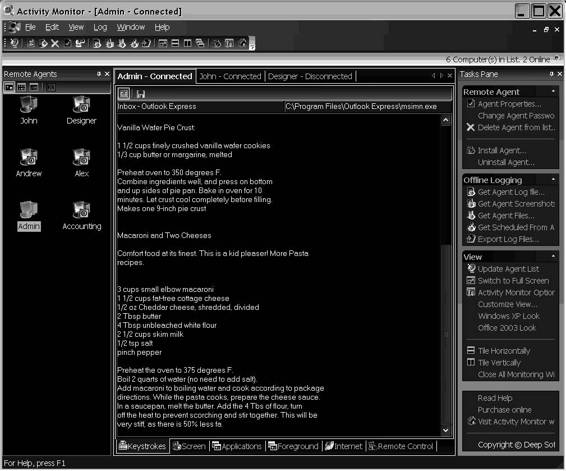
• Tracks any user’s keystrokes on an administrator’s screen in real-time mode. This includes passwords, e-mail, and chat conversations, as shown in Figure 8-1.
Source: http://www.softactivity.com/employee-monitoring.asp. Accessed 2/2007.
Figure 8-1 Activity Monitor can capture keystrokes in real time.
Tool: Track4Win
8-9
• Takes snapshots of remote PC screens on a scheduled basis
• Total control over networked computers. An administrator can start or terminate remote processes, run commands, copy files from remote systems, turn off or restart remote systems, and log the current user off.
• Deploys the client part of the software remotely from the administrator’s PC to all computers on the network
• Automatically downloads and exports log files from all computers on a scheduled basis
• Provides HTML, Excel, and CSV support to export data and reports
• Monitors multiple employee computers simultaneously from a single workstation
• Runs completely invisibly
Tool: Spector CNE
Spector CNE provides an organization with a complete record of employee PC and Internet activity. Spector CNE collects information about every e-mail sent and received, every chat conversation and instant message, every Web site visited, every keystroke typed, and every application launched. It also provides detailed pictures of PC activity via periodic screen snapshots.
The following are some of the features of Spector CNE:
• It allows an administrator to monitor and conduct investigations on employees suspected of inappropriate activity.
• It increases employee productivity by reducing frivolous and inappropriate activity.
• It monitors and eliminates leaking of confidential information.
• It monitors and recovers lost crucial communications (e-mails, chats, and instant messages).
• It assists help desk staff with PC recovery.
• It meets or exceeds federal, industry, and agency compliance requirements for keeping records of company communications and transactions.
• It monitors ongoing employee performance and PC proficiency.
• It obtains proof to support accusations of wrongdoing.
• It reduces security breaches.
• It detects the use of organization resources to engage in illegal or unethical activities.
• It limits legal liability (including sexual and racial harassment).
• It enforces PC and Internet acceptable-use policies.
Tool: Track4Win
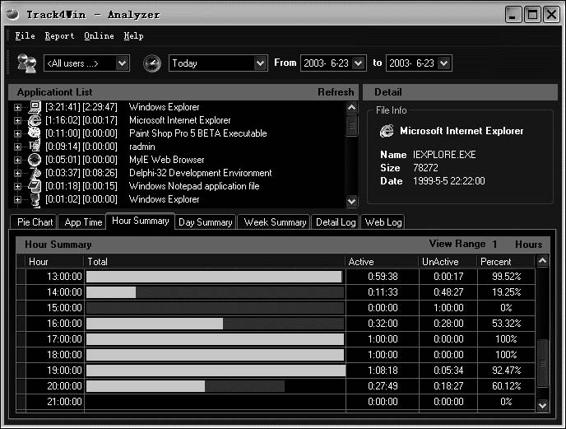
Track4Win monitors all computer activities and Internet use. With powerful network support, it can easily collect application running times (Figure 8-2), track Internet use information through the network, log this information in a database, analyze the information, and produce reports.
The following are some of the features of Track4Win:
• Employee’s current status monitoring
• Multiuser and real-time monitoring
• URL/Web site address capture and Web content tracking
• Invisibility in Windows Task Manager
The following are the technical features of Track4Win:
• Data storage in Microsoft Access database format
• Microsoft SQL Server upgradeable
• Supports Microsoft Access, Microsoft SQL, Oracle, and ODBC database connections
8-10
Chapter 8
Source: http://www.track4win.com/. Accessed 2/2007.
Figure 8-2 Track4Win keeps track of application running times.
Tool: SpyBuddy
SpyBuddy monitors the computer usage of employees. It enables an administrator to track every action on a PC, down to the last keystroke pressed or the last file deleted. SpyBuddy is equipped with the functionality to record all AOL/ICQ/MSN/AIM/Yahoo! chat conversations, all Web sites visited, all windows opened and interacted with, every application executed, every document printed, every file or folder renamed and/or modified, all text and images sent to the clipboard, every keystroke pressed, every password typed, and more.
The following are some of the features of SpyBuddy:
• Internet conversation logging: Logs both sides of all chat and instant message conversations
• Disk activity logging: Records all changes made to hard drives and external media
• Window activity logging: Captures information on every window that is viewed and interacted with
• Application activity logging: Tracks every application that is executed and interacted with
• Clipboard activity logging: Captures every text and image that is copied to the clipboard
• Browser history logging: Views all Web sites visited before SpyBuddy was installed and when SpyBuddy was not recording
• Printed documents logging: Logs specific information on all documents that are sent to the printer spool
• Keystroke monitoring: Tracks all keystrokes pressed and which windows they were pressed in
• Web activity logging: Logs all titles and addresses of Web sites that are visited
• Screen capturing: Automatically captures screenshots of the desktop (or the active window) at set intervals
• Web-site filtering: Creates Web site and protocol ban lists to prevent employees from viewing certain Web sites while SpyBuddy is active
• Web-site monitoring: Manages a list of Web sites for SpyBuddy to monitor, and if a specified keyword/
phrase is found, it will record it
• Password protection: SpyBuddy is password protected to prevent others from starting or stopping the monitoring process, as well as changing SpyBuddy configuration settings
Tool: Privatefirewall
8-11
• E-mail log delivery: SpyBuddy can periodically send the administrator recorded activity logs in a specified format (HTML/Excel/text/CSV/XML) and desktop screenshots at specified intervals
• Scheduling agent: Automatically configures SpyBuddy to start or stop at specified times and dates, or configures it to perform at the same time every day of the week
Tool: NetVizor
NetVizor is an employee monitoring solution. NetVizor allows an administrator to monitor the entire network from one centralized location. The administrator can track workstations, or he or she can track individual users who may use multiple systems on the network.
The following are some of the features of NetVizor:
• It logs keystrokes, Web site visits, searches, application usage, files, and document usage.
• It logs Internet connections, chat conversations, windows opened, e-mail activities, Internet traffic data, uploads, and downloads.
• It offers detailed user activity reports and network activity reports.
• It offers real-time visual remote monitoring and Web-based remote control.
• It disables spyware detectors.
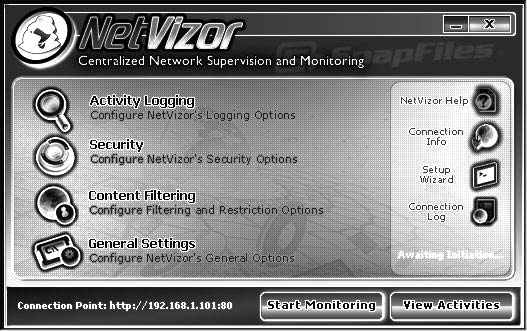
Figure 8-3 is a screenshot from NetVizor.
Tool: Privatefirewall
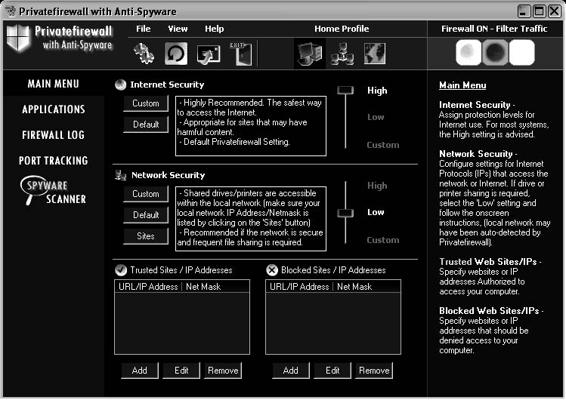
Privatefirewall is a personal firewall and intrusion detection application that eliminates unauthorized access to a PC. Its interface allows users to create custom configurations.
The following are some of the features of Privatefirewall:
• Packet filtering
• Port scanning
• IP/Web site protection
Source: http://www.netvizor.net/. Accessed 2/2007.
Figure 8-3 This shows NetVizor’s main screen.
8-12
Chapter 8
Source: http://www.privacyware.com/personal_firewall.html. Accessed 2/2007.
Figure 8-4 Privatefirewall is a personal firewall application.
• E-mail anomaly detection
• Advanced application protection
Figure 8-4 shows a screenshot from Privatefirewall.
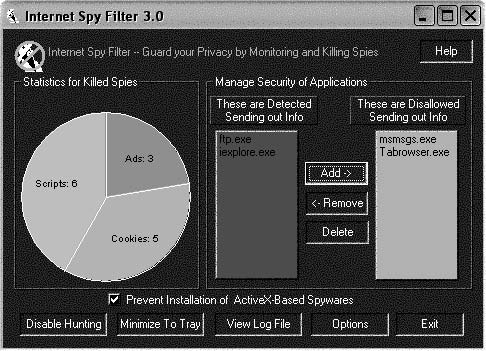
Tool: Internet Spy Filter
Internet Spy Filter blocks spyware, Web bugs, worms, cookies, ads, scripts, and other intrusive devices. When a user is online, an attacker may be monitoring the user without his or her knowledge or explicit permission.
These attackers may try to obtain private information about the user. Internet Spy Filter removes viruses and spyware, and acts as a personal firewall. Figure 8-5 shows Internet Spy Filter’s reporting feature.
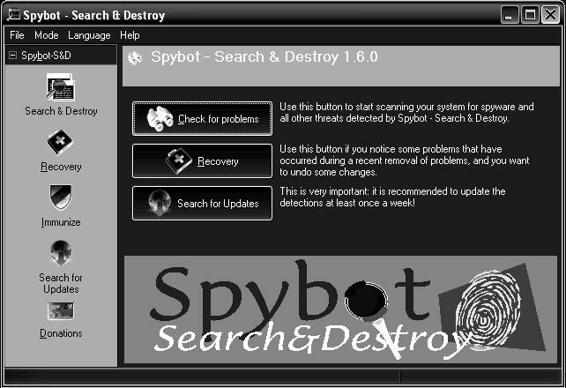
Tool: Spybot—Search & Destroy
Spybot—Search & Destroy detects and removes spyware. Spyware silently tracks a user’s Internet behavior.
This tracking data is then often used to create a marketing profile for the user that is transmitted without the user’s knowledge and sold to advertising companies. Spybot—Search & Destroy can also clear usage tracks—a useful function if a user shares a computer with other users and does not want them to see what he or she has been working on. Figure 8-6 shows a screenshot from Spybot—Search & Destroy.
Tool: SpyCop
SpyCop finds spy programs designed specifically to record screenshots, e-mail, passwords, and more. It detects and disables all known commercially available PC surveillance spy software products.
The following are some of the features of SpyCop:
• Stops password theft: It detects spy software that is placed on a computer to capture passwords.
• Keeps e-mails private: It alerts the user if his or her e-mails are being snooped by spy software.
• Kills instant message and chat spy software: It keeps online chats and instant messages safe from prying eyes.
Tool: SpyCop
8-13
Source: http://www.tooto.com/spyhunter/. Accessed 2/2007.
Figure 8-5 Internet Spy Filter reports on the spyware it has caught.
Source: http://www.safer-networking.org/en/spybotsd/index.html. Accessed 2/2007.
Figure 8-6 Spybot—Search & Destroy scans systems for spyware.
• Stops surfing monitors: SpyCop can prevent spy software from capturing and recording what Web sites a user is visiting.
• Stops keyloggers: SpyCop protects users from spy software that can capture and record every keystroke.
• Prevents online credit card theft: SpyCop can keep a user’s credit card information safe if he or she shops online.
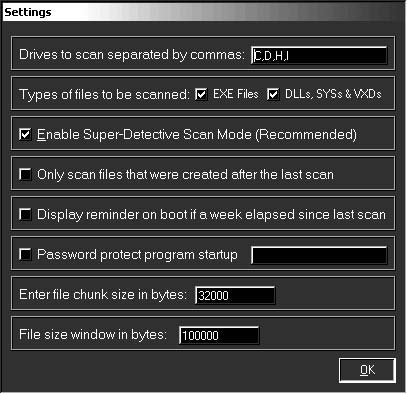
Figure 8-7 shows a screenshot from SpyCop.
8-14
Chapter 8
Source: http://www.spycop.com/. Accessed 2/2007.
Figure 8-7 SpyCop allows a user to specify different
scan settings.
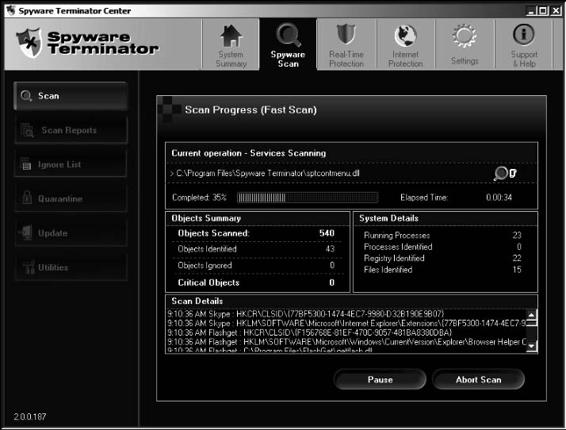
Tool: Spyware Terminator
Spyware Terminator is an adware and spyware scanner. It can remove spyware, adware, Trojans, keyloggers, home-page hijackers, and other malware threats.
The following are some of the features of Spyware Terminator:
• Removes spyware: Spyware Terminator scans a computer for known threats and reports its findings.
• Scheduled scans: It gives users the ability to schedule spyware scans on a regular basis to ensure a computer’s integrity.
• Antivirus integration: It includes an open-source antivirus program to achieve a higher level of security.
Figure 8-8 shows a screenshot from Spyware Terminator.
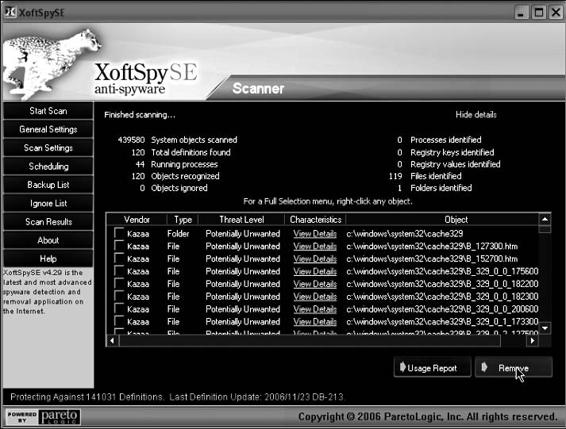
Tool: XoftSpySE
XoftSpySE is a spyware detection, scanning, and removal tool, protecting users from unwanted spyware.
The following are some of its features:
• XoftSpySE completely scans PCs, including memory and registry.
• It removes all spyware, unwanted toolbars, and browser hijacks.
• It prevents identity theft.
Figure 8-9 shows a screenshot from XoftSpySE.
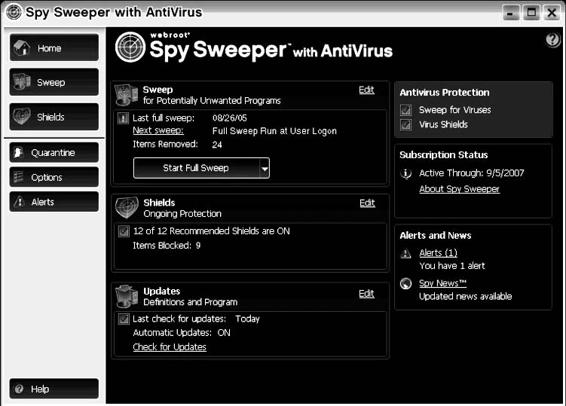
Tool: Spy Sweeper
Spy Sweeper detects and removes traces of spyware, including Trojans, adware, keyloggers, and system monitoring tools. It has the ability to run spyware scans automatically, prevent new malware from being installed, and prevent unauthorized system changes to browser settings, startup programs, and so on.
Tool: Spy Sweeper
8-15
Source: http://www.spywareterminator.com/features/antispyware-features.aspx. Accessed 2/2007.
Figure 8-8 Spyware Terminator scans all the files on a computer for spyware.
Source: http://www.xoftspy.co.uk. Accessed 2/2007.
Figure 8-9 XoftSpySE scans a computer’s files, memory, and registry for spyware.
8-16
Chapter 8
Source: http://www.spychecker.com/software/antispy.html. Accessed 2/2007.
Figure 8-10 This is the main screen of Spy Sweeper.
The following are some of the features of Spy Sweeper:
• Real-time protection: Spy Sweeper blocks spyware threats in real time, before they can infect a user’s system.
• Advanced detection and removal: Spy Sweeper’s advanced detection and removal capabilities are effective at fully removing spyware that is notorious for being difficult to eliminate. Even the most malicious spyware programs are removed in a single sweep.
• Accurate risk assessment: Spy Sweeper uses a risk assessment test when detecting spyware programs to let a user know how dangerous different spyware programs are. Spy Sweeper gives the user a quick overview of each threat, what it does, and its potential danger.
Figure 8-10 shows a screenshot from Spy Sweeper.
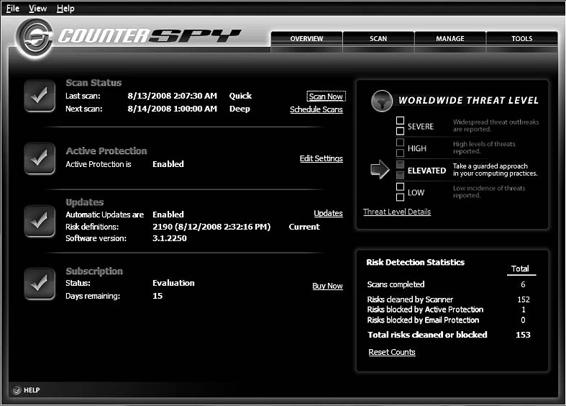
Tool: CounterSpy
CounterSpy detects and removes adware and spyware. The following are some of the features of CounterSpy:
• System scans: The scanning engine checks the entire computer using in-depth scans of the computer’s hard drives, memory, processes, registry, and cookies. It uses a continually updated database of thousands of known spyware signatures to provide ongoing and accurate protection. A user can scan for spyware manually or schedule times for CounterSpy to scan the computer.
• FirstScan: FirstScan is CounterSpy’s scan-and-remove-on-boot technology designed specifically to detect and remove the most deeply embedded malware. CounterSpy scans the disk and cleans out malware
prior to Windows startup so that hard-to-kill malware and rootkits can be exterminated.
• Kernel-level active protection: The kernel is the heart of an operating system. CounterSpy’s active protection works inside the Windows kernel, watching for malware and stopping it before it has a chance to execute on a user’s system.
• ThreatNet: ThreatNet provides ongoing security risk information, which is used to update the CounterSpy spyware database. ThreatNet is a revolutionary network community that connects diverse CounterSpy users so they can share and identify new applications and signatures. This information helps block new spyware.
Figure 8-11 shows a screenshot of CounterSpy.
Tool: iMonitorPC
8-17
Source: http://www.sunbeltsoftware.com/documents/counterspy-user-guide.pdf. Accessed 2/2007.
Figure 8-11 CounterSpy’s main screen provides a comprehensive view of
its protection.
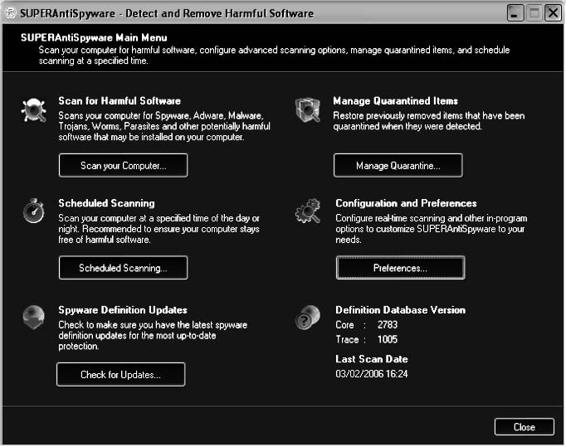
Tool: SUPERAntiSpyware
SUPERAntiSpyware scans computer systems for known spyware, adware, malware, Trojans, dialers, worms, keyloggers, hijackers, and many other types of threats.
The following are some of the features of SUPERAntiSpyware:
• It offers quick, complete, and custom scanning of hard drives, removable drives, memory, the registry, individual folders, and so on.
• It includes excluding folders for complete customization of scanning.
• It repairs broken Internet connections, desktops, registries, and more.
• It offers real-time blocking of threats.
• It schedules either quick, complete, or custom scans daily or weekly to ensure a user’s computer is free from harmful software.
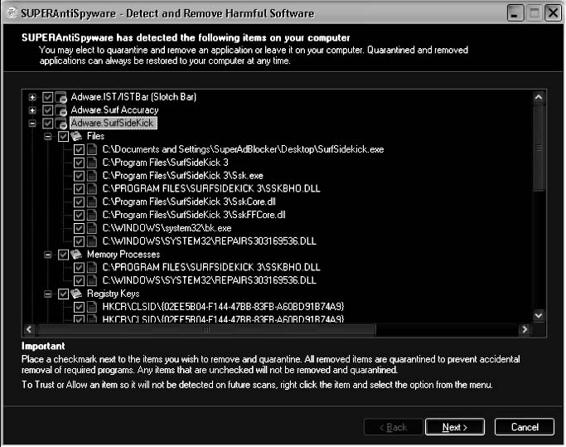
Figures 8-12 and 8-13 show screenshots from SUPERAntiSpyware.
Tool: iMonitorPC
iMonitorPC monitors computer activities and Internet use by employees. It helps in discovering employee productivity and documents any computer or network abuse. It runs invisibly and records the following types of user activity:
• Programs used
• Web sites visited
• Chat history
• Social network usage
8-18
Chapter 8
Source: http://www.superantispyware.com/index.html. Accessed 2/2007.
Figure 8-12 This shows the main screen for SUPERAntiSpyware.
Source: http://www.superantispyware.com/index.html. Accessed 2/2007.
Figure 8-13 SUPERAntiSpyware displays a report of the threats it has found,
allowing users to remove or quarantine those files.
Guidelines for Writing Employee-Monitoring Policies
8-19
Source: http://www.imonitorpc.com/IMonitorPCEnterprise.aspx. Accessed 2/2007.
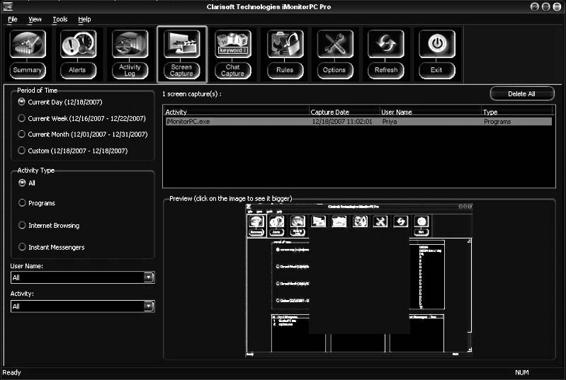
Figure 8-14 iMonitorPC performs screen captures so an administrator can see what
employees are doing.
iMonitorPC records the following types of usage information:
• Screen captures (Figure 8-14)
• Detailed activity reports
• Summary reports
iMonitorPC also includes the following:
• Web site blocking
• Program usage limits
• Chat user blocking
• User alerts
• Advanced filtering
Guidelines for Writing Employee-Monitoring Policies
Because of security reasons, organizations often have to monitor employees. Management should maintain policies concerning employee monitoring. The following are some guidelines for writing employee-monitoring policies:
• Make sure employees are aware of what exactly is being monitored: It is essential that employees are aware of what activities are being monitored. Employee-monitoring policies must specify all
activities that are monitored. Employees must be clear if monitoring occurs only if the organization suspects a problem.
• Employees should be briefed on an organization’s policies and procedures: New employees should be told about the rules, regulations, policies, and procedures of the organization. Any questions should be answered.
• Employees should be made aware of the consequences of policy violations: Policies should provide detailed information of punishment if an employee violates the rules and regulations of the organization.
8-20
Chapter 8
• Be specific and the policy should be applicable to each and every employee: The policy should be specific and should relate to every employee in the organization, irrespective of the employee’s position.
An organization should take action if any employee violates the rules.
• Terms that are specific should be bold, underlined, or italicized: Specific and technical terms that let the employee understand the policy clearly should be brought to notice by making them bold, underlined, or italicized.
• Apply provisions that allow for updates to the policy: An organization should make provisions for updating policies.
• Policies should adhere to local laws: Policies should relate to local laws, as an organization can involve law enforcement when an employee violates certain rules that are also laws.
Chapter Summary
■ The term corporate espionage is used to describe espionage conducted for commercial purposes on companies and governments, and to determine the activities of competitors.
■ Personal relations, disgruntled employees, and easy money are the main motives behind corporate spying.
■ The major techniques used for corporate spying are hacking, social engineering, dumpster diving, and phone eavesdropping.
■ Steps to prevent corporate espionage are understanding and prioritizing critical assets, defining acceptable level of loss, controlling access, baiting, detecting moles, profiling, monitoring, and analyzing signatures.
■ Netspionage is defined as network-enabled espionage in which knowledge and sensitive proprietary information are stored, transmitted, and obtained via networks and computer systems.
Review Questions
1. What are the reasons behind corporate espionage?
___________________________________________________________________________________________
___________________________________________________________________________________________
2. What type of information do corporate spies look for?
___________________________________________________________________________________________
___________________________________________________________________________________________
3. What are the different techniques of spying?
___________________________________________________________________________________________
___________________________________________________________________________________________
4. What are the techniques for securing the confidential data of a company from spies?
___________________________________________________________________________________________
___________________________________________________________________________________________
5. What are the steps to prevent corporate espionage?
___________________________________________________________________________________________
___________________________________________________________________________________________

Hands-On Projects
8-21
6. How can you investigate corporate espionage cases?
___________________________________________________________________________________________
___________________________________________________________________________________________
7. What is netspionage?
___________________________________________________________________________________________
___________________________________________________________________________________________
8. Briefly explain the guidelines that organizations should follow when writing employee-monitoring policies.
___________________________________________________________________________________________
___________________________________________________________________________________________
Hands-On Projects
1. Perform the following steps:
■ Download and install Nitrous Anti Spy from www.nitrousonline.com/antispy.html.
■ Explore the various options.
2. Perform the following steps:
■ Navigate to Chapter 8 of the Student Resource Center.
■ Install and launch SpyBuddy.
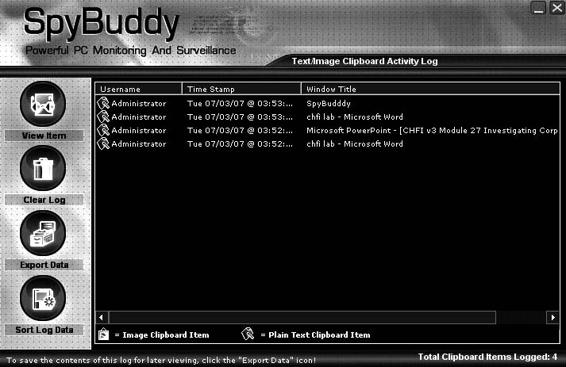
■ Click on Text/Images Sent to Clipboard (Figure 8-15).
Figure 8-15 SpyBuddy shows the text and images that a user has copied to
the clipboard.
8-22
Chapter 8
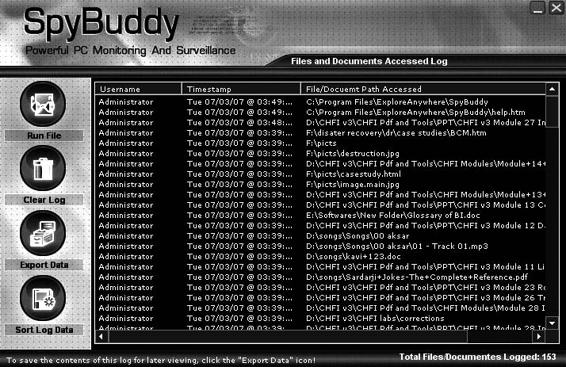
■ Click on Documents and Files Accessed (Figure 8-16).
Figure 8-16 SpyBuddy shows the documents and files that a user
has accessed.
■ Click on Windows Launched (Figure 8-17).
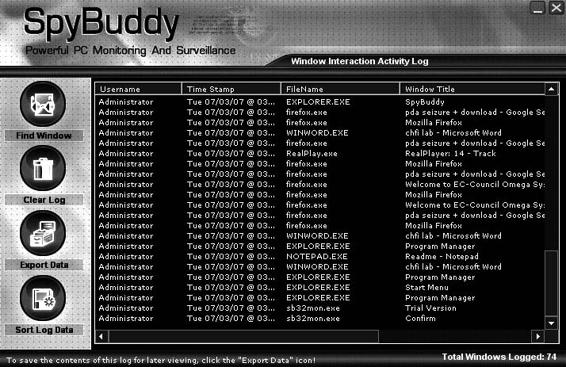
Figure 8-17 SpyBuddy shows the windows that a user has launched.
3. Perform the following steps:
■ Navigate to Chapter 8 of the Student Resource Center.
■ Install and launch Activity Monitor.
■ Explore the various options.

All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.