Building an Information Security Awareness Program: Defending Against Social Engineering and Technical Threats, First Edition (2014)
CHAPTER 7. Social Engineering
Valerie Thomas Securicon, Lorton, VA, USA
Abstract
A common misconception is that all attacks are purely technical in nature. Social engineering is the art of gaining trust or acceptance in order to persuade someone to provide information or perform an action to benefit the attacker. The attacker then combines the newly acquired information, which is usually obtained through research and multiple attacks, with a technical attack to produce a result that is disastrous to the target.
Keywords
Social engineering
Phishing
Spear phishing
Dumpster diving
Deception
What is Social Engineering?
“Nice weather we're having,” Mark said with a grin as he flicked his lighter to the cigarette in his mouth while struggling to hold his umbrella. “Yeah, just great,” agreed Jerry as he blew out a cloud of smoke toward the windows of an office building. Taking another drag, Jerry asked, “Did you catch the game last night?” Mark flicked some ashes to the ground, “Nah, the wife wanted to check out some new tapas place. Spent 70 bucks and I'm still hungry.” Jerry smirked as the two men extinguished their smokes. “Yeah, I know how that goes,” he said with a nod as Mark swiped his access card and held the door as Jerry shook the rain from his jacket and then stepped inside the building. The men went opposite ways in the hallway. Mark returned to his desk to take an incoming call. Jerry found an empty conference room to set up his laptop and then began stealing the company's data.
You see, Jerry wasn't an employee; he was an attacker.
Social engineering is the art of gaining trust or acceptance in order to persuade someone to provide information or perform an action to benefit the attacker. Even though most social engineering attacks are nontechnical, when combined with technical attacks, the results can be disastrous for the target. Famous hacker Kevin Mitnick coined the term social engineering in his first book The Art of Deception. Using persuasion and deception in combination with technical attacks, Mitnick was able to infiltrate organizations such as Pacific Bell and Nortel before his apprehension in 1995. Upon his release in 2000, Mitnick founded Mitnick Security Consulting and is now one of the most sought-after computer experts in the world.
Who are Social Engineers?
Not all hackers fit the stereotype of an antisocial teenager living in his mom's basement; the same applies to social engineers. Most social engineers are highly extroverted and have no qualms about chatting up a stranger. In order to manipulate the trust of people, one must be willing to talk to them. Usually, they dress to blend into the environment but occasionally dress to stand out if the situation is right. It also isn't safe to assume that all social engineers and hackers are men. Women are perceived to be less threatening than men, which enable them to be very effective attackers. Above all, they are likeable people who make others they come in contact with feel good about them.
Why Does It Work?
From a young age, we're taught “The Golden Rule: Treat others the way you want to be treated.” When we see someone struggling, our first reaction is to help him or her. This is especially true if the person indicates that he or she will get in trouble if the target doesn't help. Social engineering uses our psychological makeup against us by striving for empathy from the target. Empathy is the drive to identify another person's emotions and/or thoughts and respond with the appropriate emotion. Lastly, these types of attacks are effective because many people are unaware of what social engineering attacks are and the threat they pose.
How Does It Work?
Not all social engineering attacks are designed to yield pieces of sensitive information, such as passwords. Some are meant to obtain a piece of information that seems insignificant to the target, such as the name of their cleaning company. The attacker uses these smaller pieces of information to create a cover story, or pretext, to perform an attack. The goal of a pretext is to pass the age-old “Duck Test: If it looks like a duck, swims like a duck, and quacks like a duck, then it probably is a duck.”
The attack cycle can be broken into three phases:
■ Information gathering
■ Attack planning
■ Attack execution
For the sake of discussion, we'll combine attack planning and execution, as we'll site many examples and don't want to confuse them.
Information Gathering
Deception is a very meticulous business that involves the smallest of details, in some cases including the weather. In order for a social engineer to be successful, they have to blend into the target environment.
Blending isn't merely physical; one must also be able to speak the lingo of the organization and know its key players. Information is gathered from a multitude of Internet sources. We'll discuss the most popular resources and how a social engineer uses them.
The Company Website
Social engineers examine the target's website closely for some obvious reasons, such as identifying their industry and products/services. Some less obvious items they look for are the following:
■ Number of employees—It's more difficult to social engineer an organization where everyone is on a first-name basis, difficult but not impossible.
■ Locations—Understanding where the target's offices are located is crucial. If the attacker is going to impersonate an employee from engineering, they want to be sure that their target is not sitting in the next cubicle.
■ Job openings—Detailed postings provide insight into specific technologies that the target may be using, such as antivirus and intrusion detection systems (IDS). Job postings also provide high-level detail on where company departments are located. For example, three accounting jobs are posted with a location of Dallas.
■ Names of executives and managers—This information can be used to draft an organizational chart.
■ E-mail address format—Once an attacker knows the target's e-mail scheme, such as john.smith@abc.com, they can create e-mail lists with names discovered from other sources. The user's naming scheme in their e-mail address can sometimes be the same format for their login username.
■ Current events—Has the target company merged with another company recently? Posing as an employee from the newly acquired company could be a possible attack vector. Are they having any events that are open to the public? These events can be an opportunity to learn company lingo and observe their level of security awareness.
Ultimately, attackers need a granular understanding of the target in order to pose as an employee or trusted insider. The company website is a valuable intelligence source, but not the only one.
Social Media
While social media websites are great for staying connected with friends and colleagues, they are fertile hunting ground for attackers. Facebook and Twitter provide an in-depth look into the personal lives of potential targets. In addition to a near real-time update of the person's activities, other pieces of useful information are usually included. A few examples include
■ names of family members
■ high school attended
■ birthday
■ names of pets
■ favorite color
■ hobbies or interests
All the items listed above provide potential answers to password reset or other security-related questions. These pieces of personal information also provide an attacker potential attack vectors for infecting the victim's computer, more about that later.
To a social engineer, LinkedIn is a shopping list for targets. The granular search options allow for filters such as current employer, previous employer, physical location, industry, and more. Want to know who works in the engineering department of your target company? No problem. With a premium LinkedIn account and a few tailored searches, you can have a list in a matter of minutes. Better yet, most profiles include a partial resume detailing job duties and technical skills, which provide an overview of defensive technologies in place at the target organization.
Search Engines
Using your search engine of choice, it may be possible to obtain “juicy” documents. These may obtain internal information such as common acronyms, financial details, network diagrams, and other items of interest. Some refer to this as “Google hacking,” but any search engine will suffice. The following examples are written for Google searching:
■ “Company name” internal filetype:doc
■ “Company name” sensitive filetype:xls
■ “Company name” private filetype:ppt
■ “Company name” “do not disseminate” filetype:pdf
The Dumpster
Dumpster diving is an old and popular information gathering method. Although it isn't very enjoyable, it often yields great results. During red team assessments, my team has discovered everything from documents marked “Sensitive-Do Not Print” to ID cards that opened the facility door. You'd be surprised just how much information the dumpster may hold…just don't forget to wear gloves.
The Popular Lunch Spot
Ever heard the phrase “Loose lips sink ships?” Often times, if an attacker (or anyone else for that matter) wants to know what's going on in an organization, all they need to do is go to lunch. Hitting the popular restaurants and cafes around the target location is a no-risk method for gathering data. If two or more coworkers are together for any length of time, it's almost inevitable that they will “talk shop.” The larger the group, the more detailed the conversation. When I train security professionals in the ways of social engineering, one of their assignments is to go out to lunch and do nothing but listen to conversations around them and take notes. There's usually a prize waiting for whoever brings back the juiciest story. The next time you're in a restaurant or coffee shop, try it for yourself and see what knowledge can be gained by simply listening. Employees of the target company are usually easy to spot based on the forgotten ID card dangling from their neck or corporate shirts and jackets. This is also a fantastic opportunity to learn company lingo.
Attack Planning and Execution
Jerry the Attacker
Let's revisit our characters from the beginning of the chapter. Prior to arriving onsite, Jerry had gathered multiple aerial maps of the target location in an attempt to locate potential smoking areas. Generally, smoking areas are in the side or back of the building away from the main entrance and away from most security guards. Once Jerry arrived onsite, he had an early lunch at a café across the street and observed the building from a distance. As the waiter served his burger and fries, Jerry spotted Mark in the smoking area along with two other men. Jerry recognized Mark from his LinkedIn profile picture, which reaffirmed the target location was correct. Popping a few fries into his mouth, he watched as the men made conversation and then smiled as Mark held the door open for everyone heading back inside as the rain began to fall.
While the above example appears simple and straightforward, a significant amount of time was invested researching potential attack vectors for the target company. Not only did Jerry need a plan to obtain building access, but also he needed to plan his goals once inside, and an exit strategy if detected.
The Spear Phishing E-mail
During the information gathering phase, the attackers discovered that their target company was using a Cisco VPN client. Employees were able to install the client on their work laptops to connect to the corporate network upon proper authentication. The attackers then created a malicious version of the VPN client software that would provide them with access to the victim's computer but would still function as a normal VPN client. Once the malicious VPN client was fully functional, the attackers performed the following actions to carry out the attack:
■ Purchased a domain similar to the target company's.
■ Selected the target employee by reviewing the gathered names and job titles. They selected “Dan” from the marketing department who traveled frequently (and was therefore very dependent on the VPN). Dan was also selected because of his nontechnical position in the company. Nontechnical employees are less likely to question a coworker from the company's network team when instructed to install software.
■ Selected the employee whose name they would use to send the attack e-mail. According to his LinkedIn profile, Joey was the lead network engineer for the company. Choosing a person with seniority is preferred because people are more likely to comply with a request from an authoritative figure, rather than a low- or mid-level employee.
■ Configured an e-mail address for Joey at their newly purchased domain.
■ Then, they waited. Remember, in social engineering attacks, timing is everything. They waited until Joey had announced on Twitter that he would be attending a conference for the remainder of the week out of state.
■ Late Friday morning, the attackers e-mailed Dan from Joey's fictitious account stating:
“In order to increase connection speed and availability we have upgraded the VPN Infrastructure. A client software update is required for use. Users who do not update by COB today will no longer have VPN access.
All VPN users must update their client software by running the attached installation program.
A system restart is not required. Please contact User Support if additional assistance is required.”
Respectfully,
Joey Smith
Network Operations
Ext. 1402
■ The team monitored the fictitious e-mail account for activity. A few minutes later, Dan replied saying that he had installed the software. The attackers then had obtained full access to Dan's system and the company network.
It may seem unrealistic that an attacker would spend weeks researching and preparing for an attack just to send a single e-mail, but this is a prime example of a real-world social engineering attack. Taking small pieces of data from multiple sources and creating a believable story is what social engineering is all about. Another view into this is that a few short weeks of intelligence gathering, one e-mail, and one piece of software have thwarted hundreds of thousands of dollars of a company's security infrastructure.
Hello, Help Desk?
Sarah was targeting a large insurance company with offices throughout the United States. Locating their web-based e-mail and VPN sites had been trivial with some customized search terms. The websites didn't require certificate-based authentication, and from what Sarah could tell without valid login credentials, two-factor authentication was not in place. This meant that all she needed was a valid username and password to access the company's resources. Using the tool FOCA, Sarah examined the metadata in various documents and presentations located on the company website. The metadata search yielded ten usernames using the scheme first initial and last name. Now that Sarah understood the username format, she could easily deduce usernames with only the employee's name. Then Sarah searched Facebook for employees of the target company and discovered 43. Of those 43 profiles, 20 of them were completely open to the public. Open profiles reveal all data that have been entered into Facebook, including the user's status updates. Sarah compiled a list of female employees with open Facebook profiles and began searching for additional information, such as signature blocks and office phone numbers.
It was the week of Christmas and the holiday season was in full swing. Sarah monitored the list of female employees with open Facebook profiles until the right status update appeared from Natalie Green. “Heading to Hawaii for ten blissful days away from the snow and ice!” This was great news for Sarah! Now, Sarah could attempt to gain control over Natalie's account with little risk of detection. Sarah compiled her list of notes on Natalie including birthday, hometown, office and cell phone numbers, home address, department name, work title, and supervisor name.
On Christmas Eve at 7:00 PM, Sarah contacted the help desk using a caller ID spoofing program to make her number appear as Natalie's cell phone. A pleasant-sounding young man answered. “Help desk, this is Paul. How may I help you?” Using her best “whiny voice,” Sarah replied. “Hi Paul. This is Natalie Green from the Denver office. I changed my password earlier this week, and now I can't remember it. It wouldn't be such a big deal if I wasn't on call this week.” She said with a sigh. Paul gave a knowing chuckle “Understand that all too well. Let's get you back online Natalie. I just need your office phone number to verify your identity.” Sarah blinked in surprise. Could it really be this easy? She bit her tongue to hold back the excitement. “Sure thing, Paul.” She replied and proceeded to read the phone number from her notes. The line went quiet, but Sarah could hear typing and the low melody of Christmas music in the background. “You're all set, Natalie. I set your password to ‘2013Denver$,’ but you'll have to change it once you log in.” Sarah smiled and let out an audible sigh of relief. “Thanks a lot Paul. I really appreciate your help tonight. I hope you aren't stuck there tomorrow too.” Paul replied “Thankfully no, but I'll be here the rest of the night if you run into any more problems.” Sarah began typing in Natalie's username and new password to verify they were in working order. “Looks like I’m good to go. Thanks again Paul. Have a Merry Christmas!” Sarah now had unrestricted access to Natalie's account for the entire week. Prior to Natalie's scheduled return, Sarah installed a backdoor that would allow her access into Natalie's account even after her password had been changed.
Help desks are prime targets for attackers because their entire purpose is to help people. The attack was performed on the evening of a holiday due to the high probability that a less experienced employee would be on shift. This was a fail-safe in case Sarah was missing a piece of key information to verify her identity. The new employee would be more likely to break procedure in order to help keep someone out of trouble.
The Social Engineering Defensive Framework (SEDF)
As a security consultant, I've performed social engineering assessments for a multitude of clients—from e-commerce to government and everything in between. Each engagement is unique, but almost always results in the same question from management: “How do we stop social engineering attacks?” I found that I didn't have a definitive resource to refer them to or even a high-level guideline to get them started.
The simple truth is that social engineering attacks can't be stopped with technology alone, nor can they be stopped with training alone. I created the Social Engineering Defensive Framework (SEDF) to help organizations prevent social engineering attacks at the enterprise level. SEDF outlines basic phases for attack prevention:
■ Determine exposure
■ Evaluate defenses
■ Educate the workforce
■ Streamline existing technology and policy
The SEDF phases are independent from each other and can be performed in an order that suits the priorities of the organization. If you've just completed a large training campaign, then perhaps evaluating defense is the next step for you.
Determine Exposure
This phase focuses on seeing websites and other available resources through the eyes of a social engineer. A web exposure assessment is a nonintrusive method of gathering client information in order to provide a clear picture on what data are exposed to the Internet.
A major area of focus is the company website. Are you providing too much information? An online employee directory, while helpful to customers, is a gold mine for social engineers. In most cases, listing key customer-focused employees provides customers with the point of contact without listing everyone who works at the company. Superfluous job postings can provide details about software deployed in your environment. Announcing your brand of antivirus and other deployed security technologies to the world is like putting out the welcome mat for attackers. Metadata analysis is a key part of the assessment to determine if usernames, passwords, and operating system details are exposed in documents that are posted on your website.
Another portion of the assessment is searching for leaked documents. Not all of these documents are discovered via Google. Peer-to-peer networks, social media, and other information-sharing websites can be excellent resources. Whenever I perform one of these assessments and attach the discovered documents, the client always asks, “Where did you get this!?”
A few other areas of focus are the following:
■ Technical support forums—You'd be surprised how many folks register for these using their company e-mail address. Code snippets and file paths can be very helpful when planning a technical attack.
■ Social media—These resources provide insight into the lives of employees and are fertile hunting ground for attackers. Personal details such as what high school they attended or pet names are often used as password reset questions. Also, knowing if someone is going to be on vacation for a week provides an attacker the opportunity to masquerade as that employee with minimal risk of detection.
■ Popular hacking websites—Websites similar to http://pastebin.com are popular dumping ground for attackers and can contain everything from account data to intellectual property.
Once the research is complete, a report is made summarizing the discovered information and the most likely attack vectors. In addition to listing attack vectors, include recommendations on how to reduce exposure of the discovered data.
Evaluate Defenses
This phase can be utilized to evaluate employee resistance and reaction to simulated attacks. Organizations can also elect to evaluate the effectiveness of detection technology and appropriate response groups. Types of simulated attacks include phishing, phone, and physical. It is common practice to outsource these assessments to a specialized vendor, but is not required.
Phishing assessments evaluate the organization's resistance against malicious e-mail content. Content can vary from hyperlinks, attachments, to HTML forms to harvest employee information or gain access to their computer. Phishing attacks are popular with attackers and should be high on the list of your organization's cyber threats. If your organization has not performed this type of assessment, a simulated phishing attack should be the first evaluated defense in this process. The detailed process for creating simulated phishing attacks can be found in Chapter 10.
Phone attacks, otherwise known as vishing, trick individuals into divulging information via a phone call or text message. Attackers perform caller ID spoofing, which causes their call to appear to be from a known phone number. Caller ID spoofing is not illegal in the United States and can be performed using a commercial service or with personal equipment. While vishing may seem out of date, it is still an extremely useful tool for attackers because their targets don't have time to think the situation through prior to providing information to the attacker. Focus your initial simulated phone attacks against employees that mainly deal with the public. Help desk personnel, sales, public relations, and human resources should be included in the initial evaluation.
Physical security education is often overlooked in awareness programs. Although physical security and cyber security usually report to different departments, they are both working to protect the same assets. Completing a physical security assessment can be an eye-opening experience for both physical and cyber security. Physical penetration tests evaluate security controls by gaining access to a specified facility or room. Team members often exploit electronic controls and utilize social engineering to obtain access. Often, physical security assessments are performed in conjunction with a network penetration test. Physical security basics and assessments are covered in detail in Chapter 8.
This outcome of this phase should answer the following questions:
Employees
■ Was access or information obtained?
■ Workstation
■ Server
■ Physical
■ How many employees provided information or access?
■ What weaknesses or vulnerabilities were utilized to obtain information or access?
■ Technology
■ Human
■ Physical barriers, such as fences
■ How many employees reported suspicious activity?
■ Correctly
■ Incorrectly
Defenders
■ How many attacks were detected?
■ What was the average detection time?
■ How were attacks detected?
■ Employee reported suspicious activity
■ Technical alert from IDS/antivirus/proxy
■ Alert from security camera or access control system
■ Discovered by guard force while on patrol
■ Were proper response procedures in place for the attacks?
■ Were the response procedures followed?
■ Was the event escalated properly?
■ Were access control alarms investigated?
The answers to the above questions can be used to evaluate the effectiveness of your current awareness program. Assessment results can also be used to update existing policy and modify detection device configuration for physical and cyber mechanisms. For maximum effectiveness, defenses should be evaluated on a regular basis. Phishing and phone assessments should be performed biannually at minimum. Physical assessments should be performed on an annual basis if your budget allows.
Educate Employees
Describing an attack can be informative, but showing an attack has a far greater impact. The best training session I have ever attended was for a government agency and began with a video of an agency employee telling an adversary sensitive details of a critical defense project. Except the “adversary” was an undercover agent attempting to social engineer information from him; and it worked. Once the video was over, the auditorium was absolutely silent. This short, homemade video was a true eye-opener for the audience. It clearly dictated the message “These threats are real and you could be the next target.” The remainder of the session went on to detail how these attacks worked and what to do if you suspected that you were being targeted.
Breaking down attack scenarios is an essential step in social engineering education. Showing the audience how each piece of information obtained and how it was used in the attack builds a true understanding of the process. Next, you'll want to discuss tactics for preventing data leaks and other attacks. A few areas to discuss are the following:
■ Metadata—Ensure your audience understands metadata and how it is used against them. Provide tutorials on how to remove metadata from documents before publication. Many of the Microsoft Office programs have this functionality built-in, but not enabled.
■ Phishing—It's essential that employees know how to identify and report phishing messages. Demonstrating that links can be disguised and how e-mail addresses can be spoofed is way to drive home the message.
■ Social media safety—Educate your audience on social media privacy settings. Walk them through step-by-step on how to restrict Facebook profiles, disable location services, and make the material non-company-specific so employees can share it with their family members.
■ Your company e-mail address—Never underestimate the significance of your company e-mail address. It should never be used to subscribe to forums, mailing lists, or other special interest groups. Not only does it expose company technology, but also it can also be used to craft spear phishing attacks posing as a mailing list update.
■ Phone attacks—Demonstrate caller ID spoofing to reinforce how easily a phone number can be faked. Discuss what employees should do if they receive a suspicious call. How do they report it?
■ Physical attacks—As we discussed earlier in the chapter, sometimes, the easiest way into a target environment is literally through the door. Emphasize the impact of tailgating attacks and the procedures for visitors.
The most important step in preventing social engineering attacks is teaching your workforce that it's ok to ask questions. If someone is attempting to tailgate in the door, it's ok for an employee to ask, “Can you scan your badge please?” It's ok to place a caller on hold while you contact their manager for verification. The objective of every awareness program should be to educate employees on reporting suspicious behavior to the security team, not to become security professionals themselves. For many organizations, this will require a culture change. Management is more likely to approve of this paradigm shift if they understand the threat, so be prepared to educate your management on these types of attacks.
Streamline Existing Technology And Policy
While technology alone cannot prevent social engineering attacks, it can minimize the impact of successful ones. Effective defensive technologies likely exist in your environment but could improve with configuration changes. Rather than reviewing configurations line by line, focus on the big picture with brainstorming sessions, beginning with high-level scenarios that involve key technical members of the cyber security team. This tactic is widely used in the defense industry under the term tabletop exercise and usually involves multiple military branches and civilian agencies. A tabletop exercise is a discussion-based event of scripted scenarios in an informal environment. Usually facilitator-led, these exercises enable security teams to walk through an attack scenario step-by-step to review
■ current incident response policy
■ Continuity of Operations (COOP) plan
■ preventative technologies
■ detection capabilities
■ methods of minimizing impact once exploitation has occurred
The scenarios are designed to encourage constructive discussion and highlight areas that need to be refined in a nonthreatening environment. Tabletop exercises can have a broad scope and include many areas of review, or a narrow focus to highlight specific areas, such as detection and preventative capabilities of deployed technology. A tabletop exercise is inexpensive to perform and can also serve as on-the-job training for new employees. Don't forget to get input from some of the staff that is actually doing the jobs. As some tasks look good on paper, there may be several other related tasks from other groups that are required and are relied on for full support of their job function.
Planning A Tabletop Exercise
The three phases of a tabletop exercise are design, execution, and after-action. The design phase is critical to exercise success and may take days to weeks to complete depending on the size and complexity of the exercise.
The Design Phase
If your organization has not performed a tabletop exercise, it's best to begin with a narrow focused exercise that includes the cyber security team. For SEDF, the main areas of focus include identifying
■ potential detection points for phishing-based attacks throughout the network and host operating system
■ methods of minimizing the impact of a successful attack with currently deployed technologies
■ response policy for social engineering attacks and incident response
It's recommended that each tabletop exercise have one area of focus. This enables participants to concentrate their efforts more effectively. Once the focus has been determined, the scenarios can be created. A scenario is a sequential, narrative account of a hypothetical incident that provides the catalyst for the exercise and is intended to introduce situations that will inspire responses [1]. Each scenario should contain one topic for discussion and discussion points to focus the group on the desired discussion. A few sample scenarios include the following:
■ Phishing attack—A group of attackers is targeting your organization with a phishing e-mail that appears to originate from your human resources department. The e-mail states that the employee must complete a privacy policy acknowledgement in order to receive insurance benefits for the year. The link that is displayed in the e-mail appears to direct the employee to the company website; however, once clicked, the employee is directed to a malicious website, which attempts to capture the information entered into the website.
■ Discussion of detection—What current mechanisms are in place to detect suspicious e-mail and/or suspicious links at the host and network level? Can they be configured to block e-mails that contain disguised links?
■ Discussion of minimizing impact—Once the cyber security team has been notified of the malicious e-mail, is it possible to determine what employees received the e-mail? Can the e-mail be deleted from the recipients' mailbox to prevent additional attacks? Is it possible to block the malicious website (both the URL and IP addresses) using a proxy or other device on the network?
■ Discussion of policy—What actions are taken when an employee reports the suspicious message to the cyber security team? What is the process to block access to the malicious website? What information from this attack can be used to further educate the workforce?
■ Malicious document—An infected PDF has been identified on the network. Once the PDF is opened, backdoor software is installed on the machine providing the attacker with access to the machine and the corporate network. Corporate antivirus does not detect the backdoor software or malicious PDF. The origin of the PDF has not been determined and the number of infected machines on the network is unknown.
■ Discussion of detection—How can compromised machines be identified? Is it possible to detect the communication of the backdoor software to its command and control address(es)?
■ Discussion of minimizing impact—Can a proxy or other network device block the command and control traffic? What options exist for removing the infected PDF and backdoor software? Is it possible to determine if data were removed from the infected machines?
■ Discussion of policy—What analysis steps are performed when a suspicious file has been identified? What authorizations are required to modify detection signatures in endpoint and/or proxy policy? What information from this attack can be used to further educate the workforce? Which departments should be notified of the attack?
Tabletop exercises require the following roles:
■ Facilitator—The facilitator's role is to create an environment that encourages dialogue and guide discussions to meet the objectives of the exercise [2]. Consider hiring an experienced consultant to facilitate the exercise, as facilitating is a specialized skill. The consultant will have a neutral opinion of the participants, enabling a constructive exercise without favoritism. Lastly, an outsider view of the company network can spark new ideas for discussion.
■ Data collector—The data collector's purpose is to document the main discussion points of each scenario and any decisions that were reached during the tabletop exercise. The data collector will also produce the after-action report summarizing the exercise.
■ Participants—Select participants whose job responsibilities are related to the exercise focus, not just managers. For detection and minimizing impact exercises, it may be useful to include key employees involved in network and endpoint implementation in addition to the cyber security team. Policy-based exercises should include representatives from each department with a named role in the current policy.
Logistics, equipment, and documentation should also be included in the design phase. Some organizations choose to conduct their exercises off-site at a meeting space or hotel conference room to focus the participants by removing the distractions of their typical day in the office. The exercise location should be a large enough space to comfortably accommodate the number of exercise participants and include an overhead projector, white board, and adequate power resources for participant laptops. Upon arrival, each participant should receive a participant guide. Participant guides should include
■ purpose for the exercise
■ scope and objectives
■ exercise scenarios
■ supporting material (network diagrams or policies)
The facilitator guide should include the same material as the participant guide along with the facilitator questions that are to be asked during each scenario. Data collection sheets should include the following columns:
■ Problem or objective
■ Department affected
■ Current response actions or technology
■ Resolution or recommendation
The Execution Phase
The exercise should begin with comments from the cyber security management before introducing the facilitator. The facilitator should ask each participant to introduce themselves and their role in the organization. Although most employees are familiar with individual roles and responsibilities, the facilitator is not. The facilitator then provides a high-level overview of the exercise schedule and ground rules. The ground rules are meant to foster a neutral environment for exchange of ideas. A few example ground rules are the following:
■ There are no right or wrong answers. All ideas are welcome and will be captured and acted on as appropriate.
■ Maintain a no-fault, stress-free environment. It's very important that discussion is driven by group decision-making and problem-solving, so the environment must remain open, positive, and encouraging.
■ Use the scenario to provide context and spark creative ideas. All ideas and thoughts should be based on the information provided by the scenario, but this should not limit your thinking.
■ Do not limit the discussion to official positions or policies. Don't be afraid to go beyond your title/position as you think about the situations that are presented [2].
The facilitator should introduce the first scenario. If the participants have no questions regarding the scenario events, the facilitator should ask the first question listed for the scenario and then step back and let the participants discuss. If the group begins to focus on topics that are not relevant to the exercise scope, the facilitator will guide the discussion back to the scenario. At the end of each scenario, the group should conduct a hot wash. A hot wash is a high-level overview of the scenario, discussion points, and conclusions. Not only does a hot wash ensure that the participants agree on the conclusions, but also it validates that the data collector has retained the proper information.
It is important to include breaks in the exercise timeline for participants to refuel on caffeine and get fresh air. If the scenarios are too drawn out, attention spans will begin to dwindle, resulting in less discussion. A typical timeline consists of 90 minute sessions with 20 minute breaks in between. Lunch should be served in an outdoor location if possible, to provide participants with a change of environment.
Once participants have completed the last scenario, perform a hot wash of the entire exercise. Some sample questions to ask are the following:
■ What are some of the key takeaways from today's exercise?
■ Are there suggestions to improve the quality of this exercise regarding
■ venue
■ participants
■ supporting documentation
■ What objectives should be included in the next exercise?
The After-action Phase
Information from the data collector is analyzed and compiled to produce a report detailing the exercise events. Next comes the most critical portion of the exercise, creating and assigning action items from the exercise report. Information from the exercise will only be useful to the organization if it is acted upon. Therefore, assigning and tracking action items is crucial to the success of the exercise process. The exercise organizers should conduct a postexercise meeting to discuss the following:
■ Was the exercise successful?
■ Were appropriate personnel included?
■ Was the facilitator sufficient?
■ Did the venue provide adequate space and power resources?
■ What actions can be taken to improve future exercises?
Many resources exist for exercise planning. The Federal Emergency Management Agency (FEMA) has a complete cyber exercise package available at http://www.fema.gov/media-library/assets/documents/26845.
Preventative Tips
In addition to the outcomes of brainstorming sessions and tabletop exercises, here are some recommendations for hardening your environment against social engineering attacks:
■ Username makeover—Attackers can enumerate usernames easily using tactics discussed earlier in the chapter, such as gathering names via social media. Usernames that are not based on names or any other identifiable characteristics complicate social engineering attacks because the attacker isn't able to quickly determine the username associated with the employee they wish to target. Instead of using vthomas for a username, consider a unique identifier such as HN90346283. Not only would this change make actions more difficult for attackers, but also it would make threat detection and log analysis easier for the cyber security team. Login attempts from usernames that stray from the unique identifiers would be an obvious attempted attack, enabling the cyber security team to properly investigate the involved machines. Because this type of change would impact everyone in the organization, the initial stages of deployment may have negative effects, such as an increase of help desk calls from employees that have forgotten their new username. A username makeover would also require support from senior management, as it would require a culture change for the organization to utilize the new format.
■ Domain purchases—Social engineers prey on their victim's inability to spot small details in attacks. A popular tactic for phishing attacks is to purchase a domain similar to the target's primary domain. For instance, if your primary domain iswww.myorganization.com, an attacker would purchase www.myogranization.com or www.my-organization.com so that the malicious link would appear legitimate at first glance. These malicious domains can also be used to attack your organization's customers if they mistype your website address and inadvertently visit the attacker's website. Creating e-mail accounts from the malicious domain adds credibility to phishing messages, as the e-mail address appears to be from within your organization. Purchasing domains that are similar to your organizations will decrease the risk of attackers using fictitious websites and e-mail addresses to lure their targets. Include popular domain extensions such as .org and .net in your purchases for maximum prevention.
■ Webmail addresses—Registering webmail addresses, such as myorganizationadmin@yahoo.com, reduces the likelihood of an attacker utilizing a webmail provider to launch phishing attacks. If an attacker is unable to purchase a convincing domain or create a convincing webmail account, the chances of their attacks being detected by spam filters increases.
Putting It All Together
The SEDF provides a high-level road map for organizations to identify areas that require improvement in order to prevent, detect, or respond to social engineering attacks (Figure 7.1). The phases do not have prerequisites and can be performed in any order you choose.
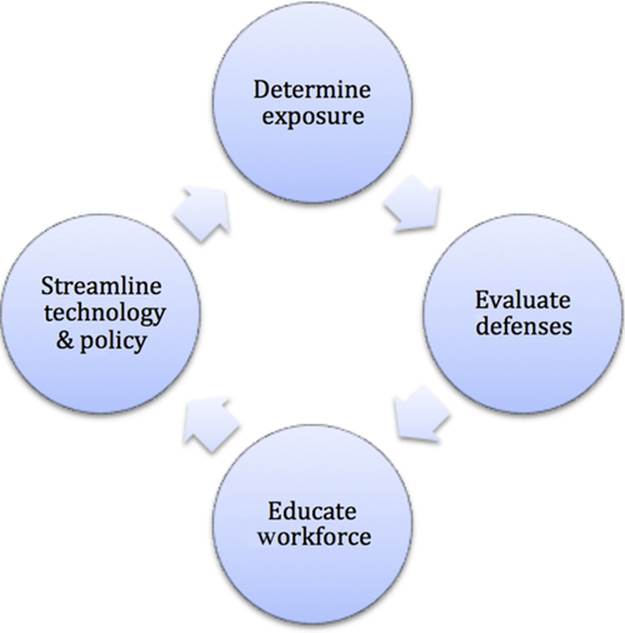
FIGURE 7.1 Phases of the social engineering defensive framework.
The key to successfully implementing the framework is to create environment changes based on the results of each phase. Environment changes can include technology, policy, employee education, organizational culture, or modifications to physical security controls. Preventing social engineering attacks is a continuous process, which will require periodic repetitions of each SEDF phase.
Where Can I Learn More About Social Engineering?
I've barely scratched the surface of social engineering and how it works in this short chapter. I highly recommend the following books:
■ The Art of Deception, The Art of Intrusion, and Ghost In the Wires by Kevin Mitnick
■ Catch Me If You Can by Frank W. Abagnale
■ No Tech Hacking by Johnny Long
Notes
[1] Tabletop Exercises for Incident Response Plans https://ics-cert.us-cert.gov/sites/default/files/ICSJWG-Archive/F2010/Simon%20-%20Tabletop%20Exercise%20Webinar.pdf [accessed on 5.22.2014].
[2] Cyber Security Tabletop Exercise http://www.fema.gov/media-library-data/20130726-1834-25045-1623/nle_12_ttx___facilitator_s_notes_5.10.12_final__508.pdf.